[ad_1]

Several vulnerabilities discovered Nexx smart devices can be exploited to control garage doors, disable home alarms or smart plugs.
Five security issues have been publicly disclosed, with severity scores ranging from medium to critical, which the vendor has yet to acknowledge and address.
The most important discovery is the use of universal credentials which are hardcoded in the firmware and also easily obtained from client communication with Nexx’s API.
The vulnerability can also be exploited to identify Nexx users, allowing an attacker to harvest email addresses, device IDs, and first names.
A video showing the impact of the security flaw, identified as CVE-2023-1748, is available below. It could be used to open any Nexx controlled garage door.
On January 4, independent security researcher Sam Sabetan published a writing on the vulnerabilities, explaining how an attacker could exploit them in real life.
It is estimated that there are at least 40,000 Nexx devices associated with 20,000 accounts. Due to the severity of the security issue, the United States Cybersecurity and Infrastructure Security Agency (CISA) has also published a relevant alert.
CISA warns owners of Nexx products that attackers could access sensitive information, execute API requests, or hijack their devices.
Vulnerability details
Sabetan has discovered the vulnerabilities listed below, which affect Nexx NXG-100B and NGX-200 garage door controllers running version nxg200v-p3-4-1 or earlier, Nexx NXPG-100W smart plug running version nxpg100cv4 -0-0 and earlier, and Nexx Smart Alarm NXAL-100 running version nxal100v-p1-9-1 and earlier.
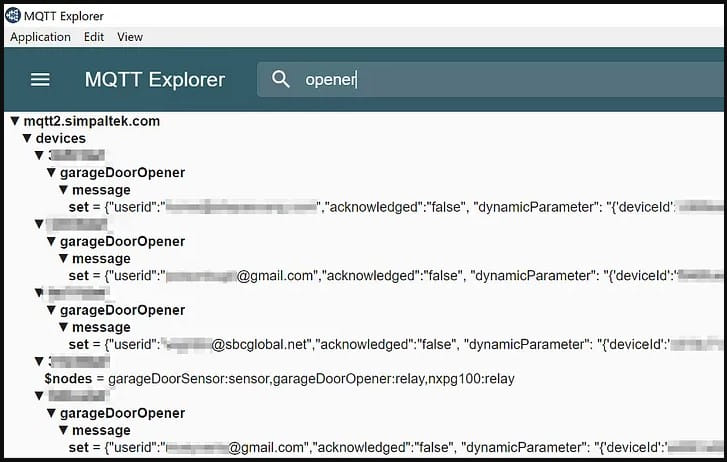
- CVE-2023-1748: Using hard-coded credentials in the mentioned devices, allowing anyone to access the MQ telemetry server and remotely control any customer’s devices. (CVSS rating: 9.3)
- CVE-2023-1749: Incorrect access control on API requests sent to valid device IDs. (CVSS rating: 6.5)
- CVE-2023-1750: Improper access control allowing attackers to retrieve device history and information and change its settings. (CVSS rating: 7.1)
- CVE-2023-1751: Bad input validation, failed to correlate token in authorization header with device ID. (CVSS rating: 7.5)
- CVE-2023-1752: Incorrect authentication check allowing any user to register an already registered Nexx device using its MAC address. (CVSS rating: 8.1)
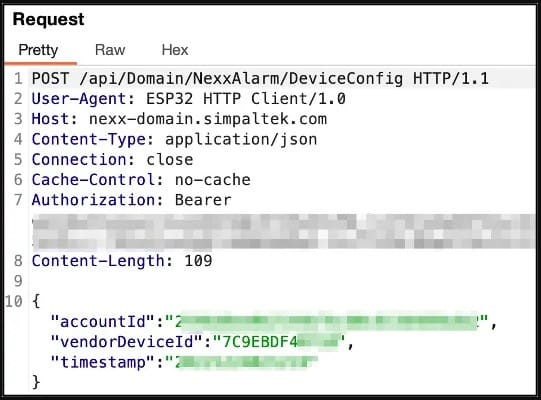
The most severe of the five flaws, CVE-2023-1748, is the result of Nexx Cloud setting a universal password for all newly registered devices through the Nexx Home Android or iOS mobile app.
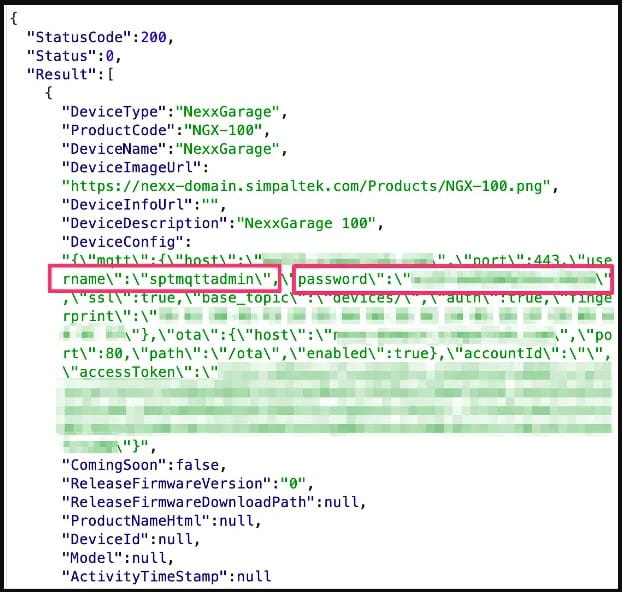
This password is available both on the data exchange API and on the firmware shipped with the device, so it is easy for attackers to obtain it and send commands to devices through the MQTT server, which facilitates communication for Nexx IoTs.
Despite multiple attempts by the researcher to report the flaws to Nexx, all messages went unanswered, resulting in the issues not being fixed.
“Nexx has not responded to any correspondence from myself, DHS (CISA and US-CERT), or VICE Media Group. I have independently verified that Nexx willfully ignored all of our attempts to assist with remediation and let these critical flaws continue to affect their customers” – Sam Sabetan
BleepingComputer has independently contacted Nexx to request comment on the above, but we have not received a response as of press time.
In the meantime, to mitigate the risk of these attacks until a fix is made available by the vendor, it is recommended that you disable internet connectivity for your Nexx devices, place them behind firewalls, and isolate critical networks.
If it is necessary to remotely access or control Nexx devices, do so only through a VPN (virtual private network) connection that encrypts data transmissions.
[ad_2]
Source link
