[ad_1]
North Korean hacking group ‘Lazarus’ is linked to a new attack spreading fake cryptocurrency apps under the invented brand, ‘BloxHolder’, to install AppleJeus malware for initial access to networks and steal crypto assets .
According to a seal FBI and CISA report as of February 2021, AppleJeus has been in circulation since at least 2018, being used by Lazarus in cryptocurrency hijacking and digital asset theft operations.
A new report from Volexity identified new fake encryption programs and AppleJeus activity, with signs of changes in the infection chain and malware capabilities.
New BloxHolder campaign
The new campaign attributed to Lazarus began in June 2022 and was active until at least October 2022.
In this campaign, threat actors used the “bloxholder[.]com”, a clone of the HaasOnline automated cryptocurrency trading platform.
.png)
This website distributed a 12.7 MB Windows MSI installer that claimed to be the BloxHolder application. However, in reality, it was the AppleJeus malware bundled with the QTBitcoinTrader app.
In October 2022, the hacking group evolved their campaign to use Microsoft Office documents instead of the MSI installer to distribute the malware.
The 214KB document was called “OKX Binance & Huobi VIP fee comparision.xls” and contained a macro that creates three files on a target’s computer.
Volexity was unable to retrieve the final payload from this latest infection chain, but they noticed similarities in the DLL sideloading mechanism found in previously used MSI installer attacks, so they are confident that it’s the same campaign.
When installing through the MSI infection chain, AppleJeus will create a scheduled task and drop additional files into the “%APPDATA%\Roaming\Bloxholder\” folder.
Then the malware will collect MAC address, computer name and OS version and send it to C2 via POST request, likely to identify whether it is running in a virtual machine or a sandbox.
A new element in recent campaigns is chained DLL sideloading to load malware from a trusted process, avoiding AV detection.
“Specifically, ‘CameraSettingsUIHost.exe’ loads the ‘dui70.dll’ file from the ‘System32’ directory, which then causes the malicious ‘DUser.dll’ file to be loaded from the application directory into the ‘CameraSettingsUIHost’ process. .exe”, ” explains Volexity.
“The ‘dui70.dll’ file is the ‘Windows DirectUI engine’ and is normally installed as part of the operating system.”
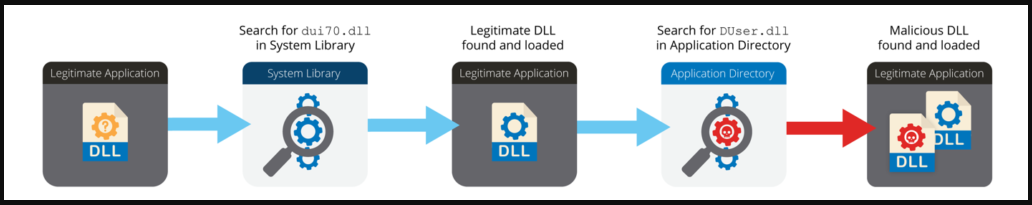
Volexity says it’s unclear why Lazarus opted to sideload chained DLLs, but could be to prevent malware scanning.
Another new feature of recent AppleJeus samples is that all of its strings and API calls are now obfuscated using a custom algorithm, making them more stealthy against security products.
Although Lazarus’ focus on cryptocurrency assets is well documented, North Korean hackers remain fixated on their goal of stealing digital cash, constantly updating themes and improving tools to stay as stealthy as possible. possible.
Who is the Lazarus Group
The Lazarus Group (also tracked as ZINC) is a North Korean hacking group active since at least 2009.
The group gained notoriety after hacking Sony Films in Operation Blockbuster and the world 2017 WannaCry ransomware campaign that has costed companies around the world.
Google discovered in January 2021 that Lazarus was creating fake personas online to target security researchers in social engineering attacks that installed backdoors on their devices. A second attack using this tactic was discovered in March 2021.
The US government sanctioned the Lazarus hacking group in September 2019 and now offers a reward of up to $5 million for information that could disrupt their business.
More recent attacks have turned to spreading trojanized cryptocurrency wallets and trading apps that steal people’s private keys and drain their crypto assets.
In April, the US government bound the Lazarus group to a cyberattack on Axie Infinity that allowed them to steal over $617 million value of Ethereum and USDC tokens.
It was later revealed that the Axie Infinity hack was made possible thanks to a phishing attack containing a malicious PDF file posing as a job offer sent to one of the company’s engineers.
[ad_2]
Source link
