[ad_1]

GitHub is rolling out support for free scanning of exposed secrets (such as credentials and authentication tokens) to all public repositories on its code hosting platform.
Secret scanning is a security option that organizations can enable for additional scanning of the repository to detect accidental exposure of known types of secrets.
It works by matching patterns provided by partners and service providers or defined by the organization. Each match is flagged as a security alert in the Security tab of the repository or to partners if a partner pattern triggers the match.
Previously, the secret analysis service was only available to organizations using GitHub Enterprise Cloud with a GitHub Advanced Security license.
GitHub scans repositories for over 200 token formats (including API keys, authentication tokens, access tokens, management certificates, credentials, private keys, secret keys, etc.).
Since the start of this year alone, the company said it has issued more than 1.7 million alerts of potential secrets exposed in public repositories.
“Today we begin rolling out secret scanning of all free public repositories in the GitHub community for free,” GitHub said.
Mariam Sulakian and Zain Malik said on Thursday.
“We will begin the phased rollout of the public beta version of Secret Scan of Public Repositories today and expect all users to have the feature by the end of January 2023.”
Once activated on a repository, GitHub will automatically notify developers of leaks of secrets in code, allowing organizations to easily track alerts, identify the source of a leak, and quickly take action to prevent misuse. fraudulent of any secret accidentally entrusted to a public repository.
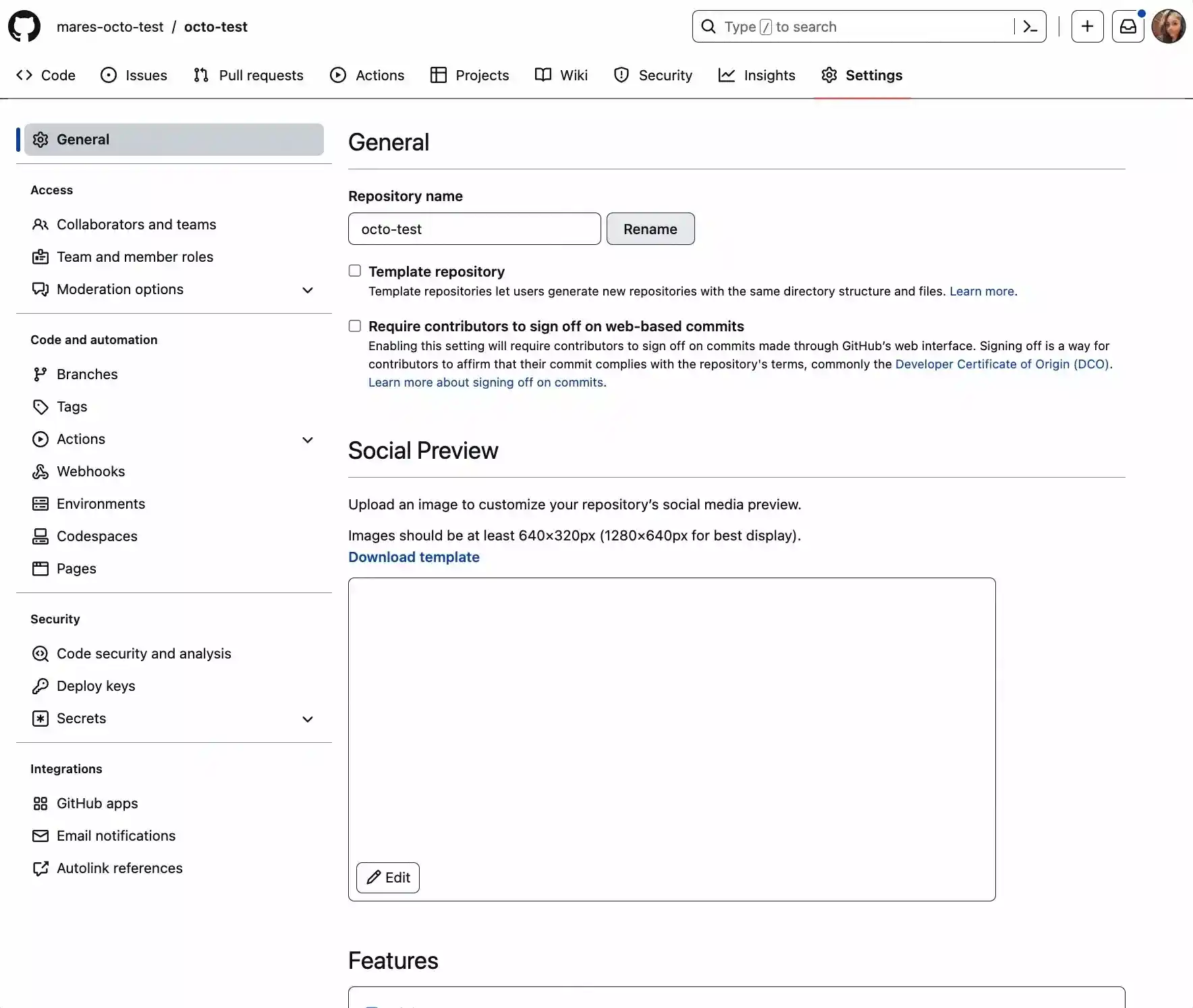
To enable secret scan alerts for free public repositories, you need to follow these steps:
- On GitHub.com, navigate to the repository’s main page.
- Under the name of your repository, click the repository “Settings” button.
- In the “Security” section of the sidebar, click “Security and code analysis”.
- Scroll down the page and click “Enable” for Secret Scan. If you see a “Disable” button, it means that secret scanning is already enabled for the repository.
Detailed information on how to enable secret scanning for your repositories at GitHub documentation site and more details about covert scan capabilities are available here.
In April, GitHub also announced that it had extended secrets scanning capabilities for GitHub Advanced Security customers to automatically block commits with exposed secrets and prevent accidental exposure of credentials before committing code to remote repositories.
Exposed credentials and secrets have led to high-impact breaches, as BleepingComputer previously reported [1, 2, 3].
Enabling secrets scanning is an easy way for organizations using GitHub to increase supply chain security and protect against accidental leaks.
[ad_2]
Source link
