[ad_1]

Google has fixed a Cloud Platform (GCP) security vulnerability affecting all users that allows attackers to hijack their accounts using malicious OAuth applications installed from Google Marketplace or third-party vendors.
Appointed GhostToken by Astrix Security, the Israeli cybersecurity startup that discovered it and reported it to Google in June 2022, this security flaw was patched via a global patch that was rolled out in early April 2023.
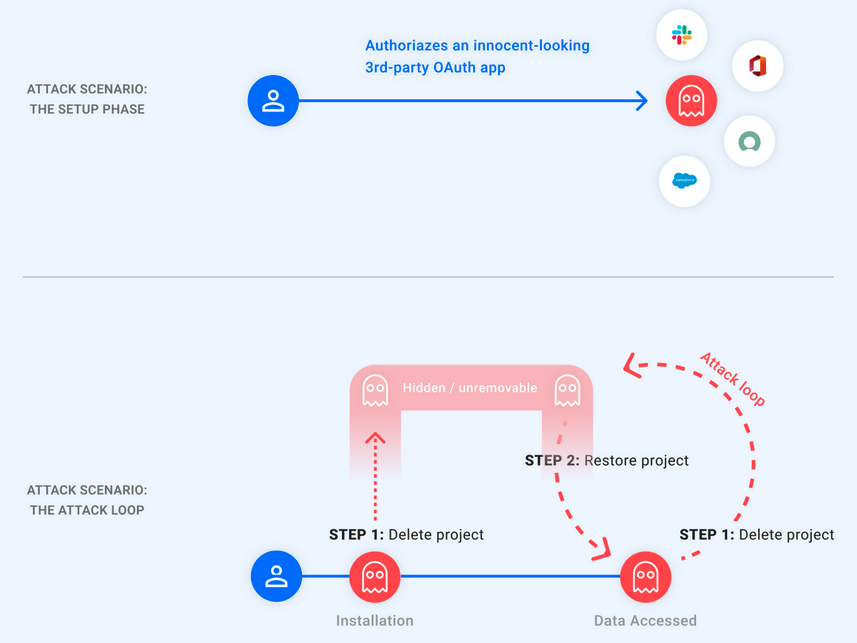
After being authorized and tied to an OAuth token that gives it access to the Google Account, malicious apps could be rendered invisible to attackers after exploiting this vulnerability.
This would hide the application of Google app management page, the only place where Google users can manage apps connected to their accounts.
“As this is the only place Google users can see their apps and revoke their access, the exploit renders the malicious app unremovable from the Google Account,” Astrix Security said. said.
“The attacker, on the other hand, at will, can unhide their app and use the token to access the victim’s account, then quickly hide the app again to restore its unmovable state. In other words, the attacker holds a “ghost token on the victim’s account.”
To hide the malicious applications allowed by the victims, the attackers only had to enter a ‘pending deletion” by deleting the associated GCP project.
However, after the project is restored, they would receive a refresh token to retrieve a new access token that can be used to access victim data.
These steps could be repeated in a loop, allowing attackers to delete and restore the GCP project to hide the malicious application whenever they needed to access victim data.
The impact of the attack depends on the permissions granted to the malicious applications installed by the victims.
The vulnerability “allows attackers to gain permanent, unremovable access to a victim’s Google account by converting an already authorized third-party application into a malicious Trojan horse application, leaving the victim’s personal data exposed forever,” Astrix Security Research Group said.
“This may include data stored on the victim’s Google applications, such as Gmail, Drive, Docs, Photos, and Calendar, or Google Cloud Platform services (BigQuery, Google Compute, etc.).”
Google’s patch allows GCP OAuth apps in “pending removal” states to appear on the “Apps with access to your account” page, allowing users to remove them and protect their accounts from hacking attempts.
Astrix advises all Google users to visit their account’s application management page and check all authorized third-party apps, making sure each has only the permissions it needs to work.
[ad_2]
Source link
