[ad_1]

A suspected Chinese hacking group has been linked to a series of attacks on government organizations exploiting a Fortinet zero-day vulnerability (CVE-2022-41328) to deploy malware.
The security flaw allowed threat actors to deploy malware payloads by executing unauthorized code or commands on unpatched FortiGate firewall devices, such as Fortinet disclosed last week.
Further analysis revealed that attackers could use the malware for cyber espionage, including exfiltrating data, downloading and writing files to compromised devices, or opening remote shells when receiving maliciously crafted ICMP packets.
One of the incidents was discovered when a customer’s FortiGate devices shut down with FIPS firmware integrity errors, rendering them unusable.
Devices stopped booting to prevent network infiltration, a standard practice for FIPS-compliant systems. The firewalls were compromised using a FortiGate path traversal exploit CVE-2022-41328, and their simultaneous shutdown led Fortinet to suspect that the attack originated from a FortiManager device.
The company said these were highly targeted attacks against government networks and large organizations, with the attackers also exhibiting “advanced capabilities” including reverse engineering the operating system of FortiGate devices.
“The attack is highly targeted, with some hints of preferred government or government-related targets,” Fortinet said.
“The exploit requires a deep understanding of FortiOS and the underlying hardware. The custom implants show the actor has advanced capabilities, including reverse engineering various parts of FortiOS.”
Links to Chinese cyberspies
A new Mandiant report says the attacks took place in mid-2022 and attributes them to a China-linked threat group the company tracks as UNC3886.
“Recent victims of Chinese spy operators include the DIB, government, telecommunications and technology,” said Mandiant CTO Charles Carmakal.
“Given the incredible difficulty in finding them, most organizations cannot identify them on their own. It is not uncommon for Chinese campaigns to turn into multi-year intrusions.”
While jointly investigating the incident with Fortinet, Mandiant discovered that after hacking into Fortinet devices, UNC3886 hijacked them using two new strains of malware for continued access to victims’ networks: a door Python-based Thincrust backdoor and the passive ICMP port-striking Castletap backdoor. .
The threat actors first gained access to an internet-accessible FortiManager device before exploiting the CVE-2022-41328 zero-day flaw to write files allowing them to move laterally across the network.
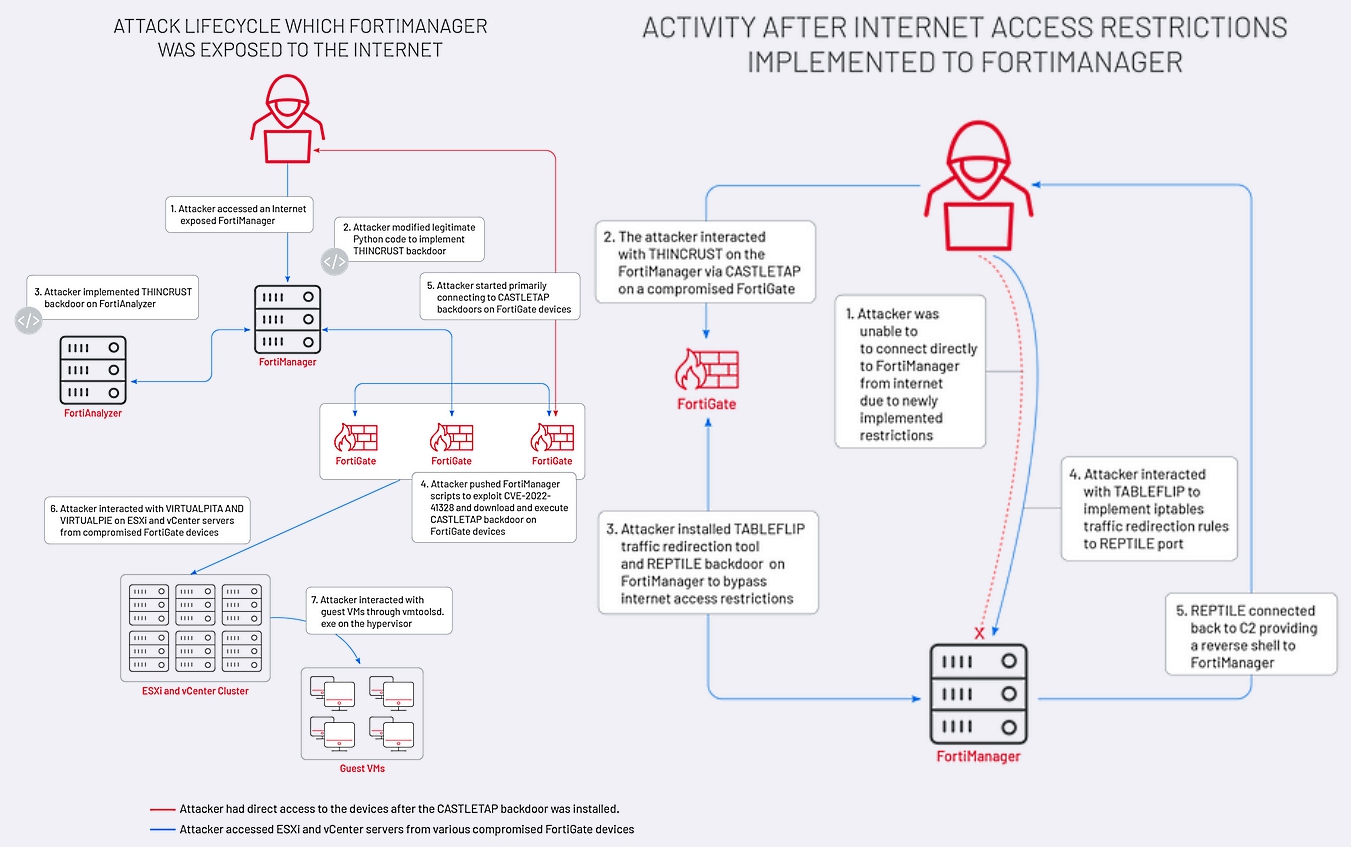
After gaining persistence on FortiManager and FortiAnalyzer devices via the Thincrust backdoor, the group used FortiManager scripts to thwart multiple FortiGate firewalls using Castletap.
Then the attacker connected to the ESXi and vCenter machines by deploying VirtualPita and VirtualPie backdoors to maintain their grip on compromised hypervisors and guest machines, ensuring that their malicious activities go undetected.
On devices configured to restrict access from the internet, attackers installed a traffic redirector (Tableflip) and a passive backdoor (Reptile) after pivoting from previously stolen FortiGate firewalls using Castletap.
“We believe that targeting these devices will continue to be the technique of choice for espionage groups trying to gain access to difficult targets,” said Ben Read, Mandiant Cyber Espionage Analytics Lead at GoogleCloud.
“This is because they are accessible from the Internet, which allows actors to control the timing of the intrusion, and in the case of VPN devices and routers, the large amount of regular incoming connections makes merging easier. “
[ad_2]
Source link
