[ad_1]
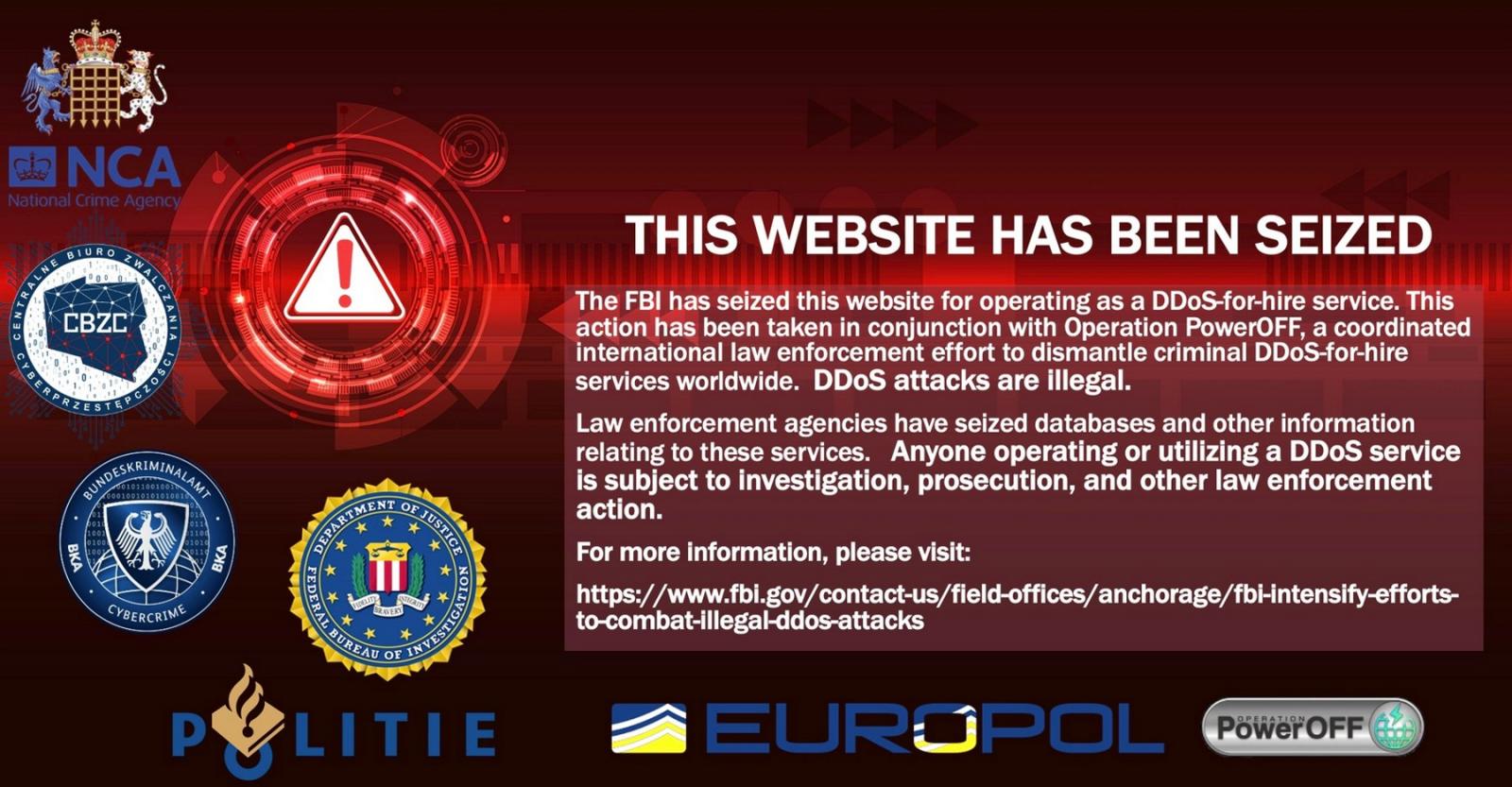
cyberstress.org (DOJ) grab banner
The US Department of Justice today announced the seizure of 13 other domains related to DDoS platforms for rent, also known as “booter” or “stressor” services.
This week’s seizures are part of a coordinated international law enforcement effort (known as the Power off operation) to disrupt online platforms allowing anyone to launch massive Distributed Denial of Service (DDoS) attacks against any target for the right amount of money.
“As part of an ongoing initiative targeting cyberattack booter services, the Department of Justice today announced the court-sanctioned seizure of 13 Internet domains associated with these DDoS services for hire” , said the Department of Justice. said.
“This week’s seizures mark the third wave of U.S. law enforcement actions against major startup services that have allowed paying users to launch powerful distributed denial-of-service, or DDoS, attacks that flood targeted computers with information and prevent them from accessing the Internet.”
The FBI also targeted major stress services in December 2022 when it seized 48 other areaswith ten previously discontinued platforms registering new domains, allowing them to stay online.
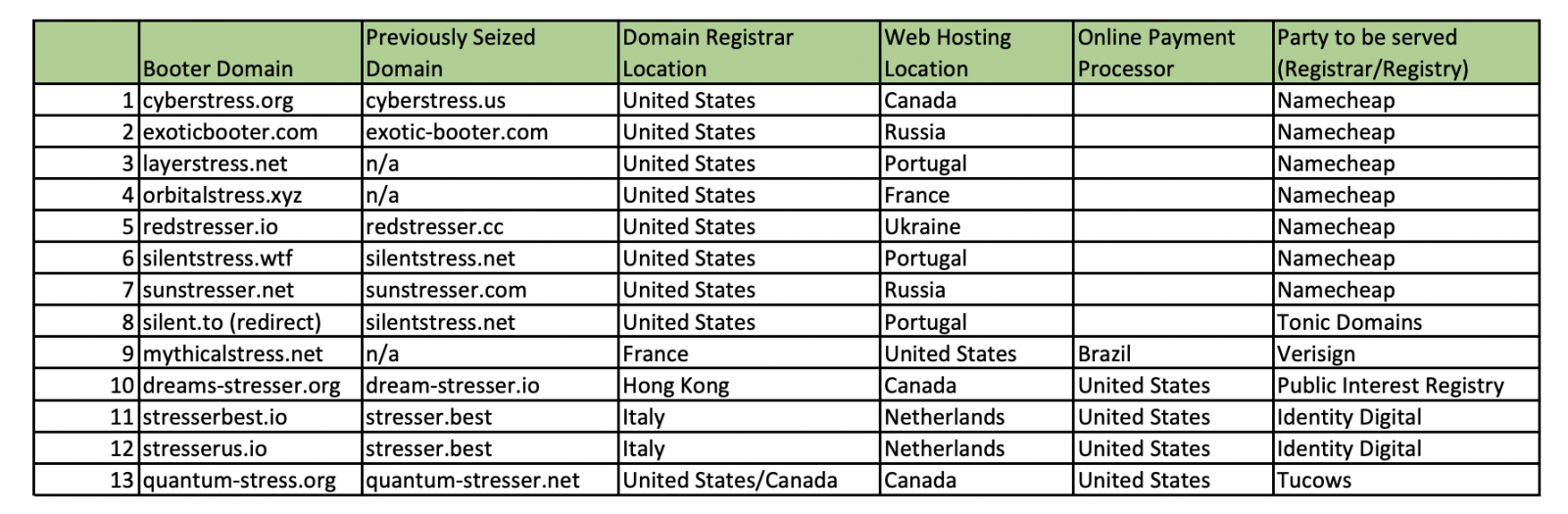
“Ten of the 13 domains seized today are reincarnations of services that were seized in a previous sweep in December, which targeted 48 prime services,” the DOJ said. said.
“For example, one of the domains seized this week – cyberstress.org – appears to be the same service operated under the domain cyberstress.us, which was seized in December.”
The full list of domains deleted this week by the FBI and previously seized domains related to the same operations are incorporated below.
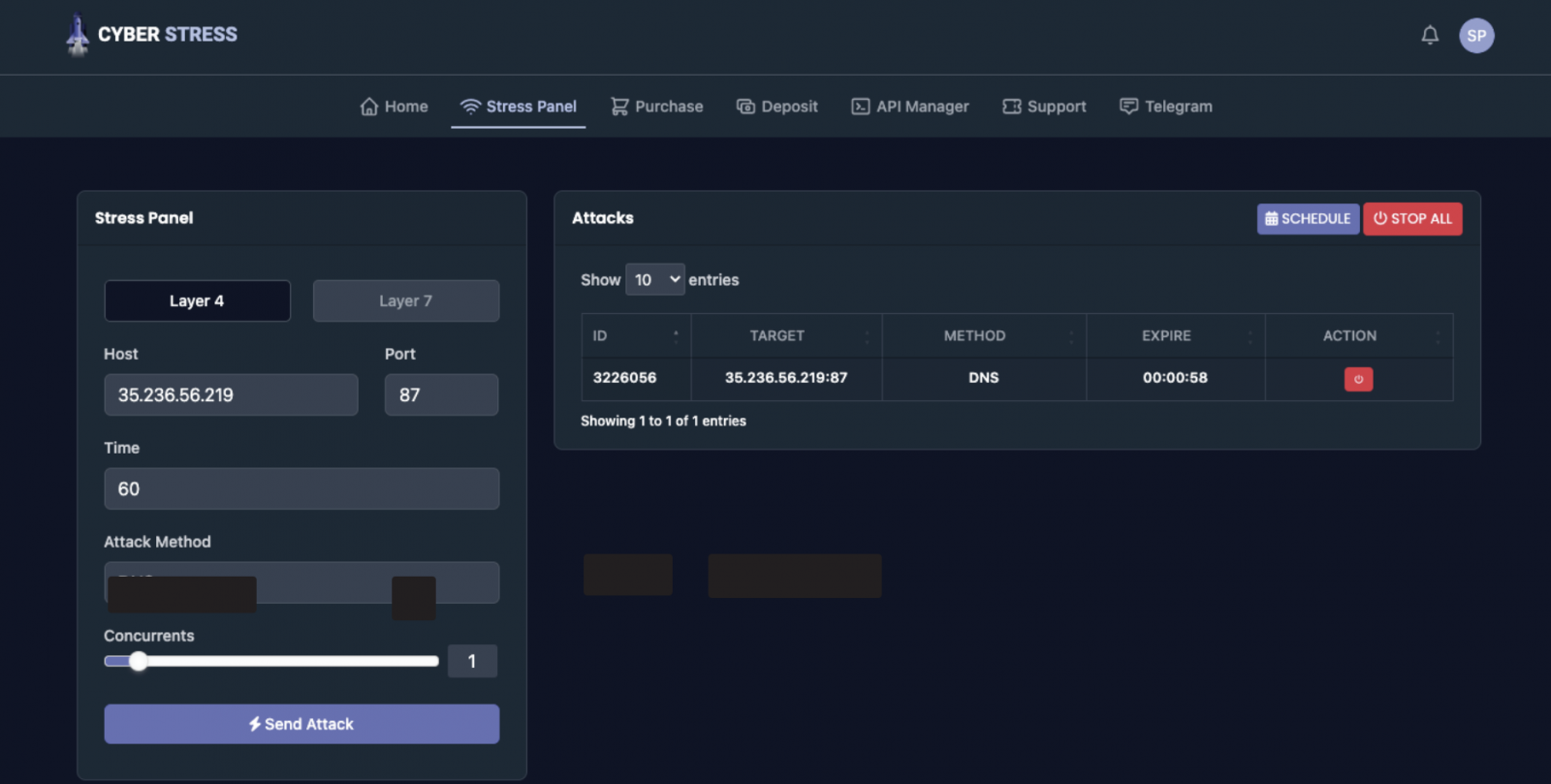
According the affidavitthe FBI tested the booter services whose domains were seized by opening or renewing accounts with each of them and evaluating the effects on the target computers via DDoS attacks launched on the computers controlled by the agency.
These tests helped confirm the functionality of the booters, with the FBI saying some attacks took the targeted devices offline even though they were using high-capacity internet connections.
“The FBI tested each of the services associated with the SUBJECT DOMAINS, which means that agents or other personnel visited each of the websites and either used the previous login credentials or registered a new account on the service. to carry out attacks,” FBI Special Agent Elliott Peterson said.
“I believe that each of the SUBJECT DOMAINS is used to facilitate the commission of attacks against unintended victims to prevent victims from accessing the Internet, disconnecting the victim or degrading communication with established Internet connections, or cause other similar damage.”
Four defendants indicted in late 2022 also pleaded guilty earlier this year to federal charges, admitting they were involved in or operated some of the startup services targeted by law enforcement.
The list of defendants and the charges to which they pleaded guilty include:
- Jeremiah Sam Evans Miller, aka “John The Dev”, 23, of San Antonio, Texas, admitted on April 6 to conspiring and violating the Computer Fraud and Abuse Act in connection with the operation of a boot named RoyalStrasser.com (formerly known as Supremesecurityteam.com);
- Angel Manuel Colon Jr., aka “Anonghost720” and “Anonghost1337,” 37, of Belleview, Fla., pleaded guilty Feb. 13 to conspiracy and violating the Computer Fraud and Abuse Act related to the operation of ‘a bootstrap service named SecurityTeam.io;
- Shamar Shattock, 19, of Margate, Fla., pleaded guilty on March 22 to conspiring to violate the Computer Fraud and Abuse Act related to the operation of a booter service known as Astrostress.com; And
- Cory Anthony Palmer, 23, of Lauderhill, Fla., pleaded guilty on February 16 to conspiring to violate the Computer Fraud and Abuse Act related to the operation of a booter service known as Booter.sx.
Recent law enforcement seizures show a commitment to targeting startup service platforms, even as some previously removed domains have resurfaced.
[ad_2]
Source link
