[ad_1]

CISA and the FBI have released a joint advisory highlighting the growing threat behind ongoing Royal ransomware attacks targeting numerous critical infrastructure sectors in the United States, including healthcare, communications, and education.
This follows an advisory issued by the Department of Health and Human Services (HHS), whose safety team revealed in December 2022 that the ransomware operation had been linked to multiple attacks on US healthcare organizations.
In response, the The FBI and CISA shared indicators of compromise and a list of related tactics, techniques, and procedures (TTPs), which would help defenders detect and block attempts to deploy Royal ransomware payloads on their networks.
“CISA encourages network advocates to review the CSA and apply the mitigations included therein,” the US Cybersecurity Agency said. said THURSDAY.
Federal agencies are asking all organizations at risk of being targeted to take concrete steps to protect against the growing threat of ransomware.
To protect their organizations’ networks, enterprise administrators can start by prioritizing patching any known vulnerabilities that attackers have already exploited.
Training employees to effectively spot and report phishing attempts is also crucial. Cybersecurity defenses can be further strengthened by enabling and enforcing multi-factor authentication (MFA), which makes it significantly more difficult for attackers to gain access to sensitive systems and data.
Samples submitted to the ID-Ransomware platform for analysis show that the corporate-targeting gang has been increasingly active since late January, showing the huge impact of this ransomware operation on its victims.
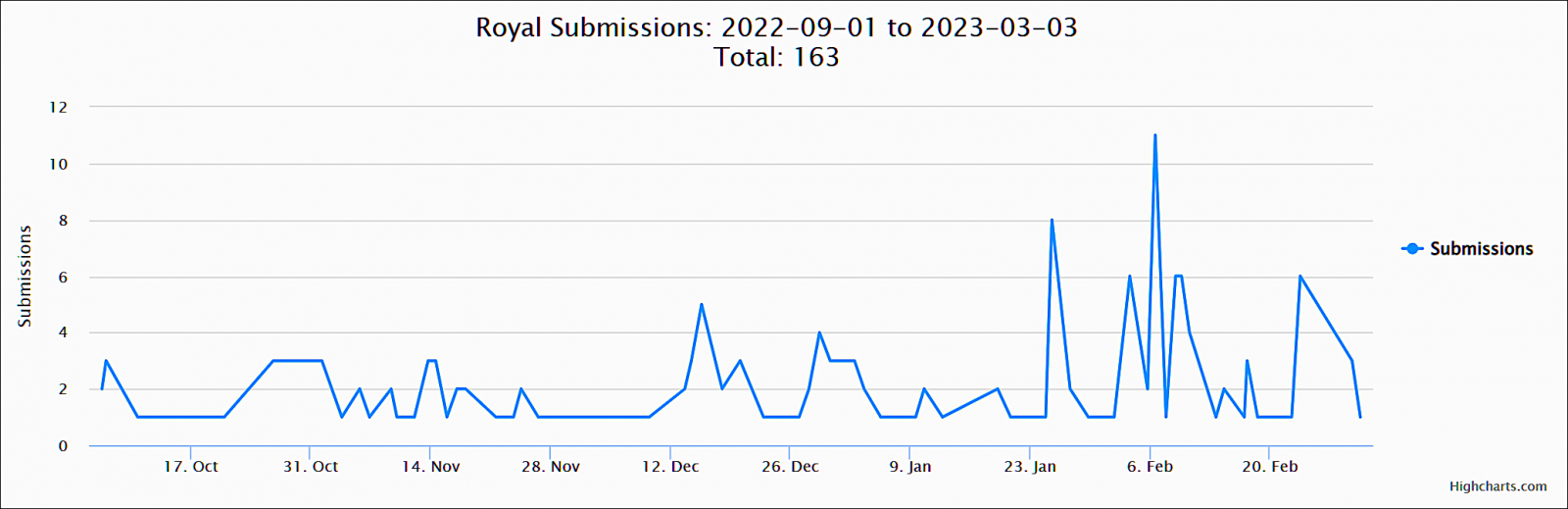
Request for Royal Incident Reports
Even though the FBI says paying ransoms will likely encourage other cybercriminals to join attacks, victims are encouraged to report incidents of Royal ransomware to their local FBI office or to CISA, whether they paid a ransom or not.
Any additional information will help collect critical data needed to track ransomware group activity, help stop further attacks, or hold attackers accountable for their actions.
Royal Ransomware is a private operation comprised of highly experienced threat actors known to have previously worked with the notorious Conti cyber crime gang. Their malicious activities only saw a jump in activity since Septemberalthough it was first detected in January 2022.
Even though they initially deployed ciphers from other operations like BlackCat, they have since moved on to using their own.
The first was Zeon, which generated ransom notes similar to those used by Conti, but they switched to a new encryptor in mid-September after rebranding to “Royal”.
The malware was recently upgraded to encrypt Linux devicesspecifically targeting VMware ESXi virtual machines.
Royal operators encrypt their targets’ business systems and demand hefty ransoms ranging from $250,000 to tens of millions per attack.
This ransomware operation also stands out from the crowd due to its social engineering tactics to trick victimized businesses into installing remote access software as part of callback phishing attackswhere they claim to be software providers and food delivery services.
Additionally, the group employs a unique strategy of using hacked Twitter accounts to send reporters details of compromised targets, hoping to attract media coverage and add further pressure on their victims.
These tweets contain a link to leaked data, which the group allegedly stole from the victims’ networks before encrypting it.
[ad_2]
Source link
