[ad_1]

Proof-of-concept exploit code is now available for a high-severity flaw in Cisco Secure Client for Windows (formerly AnyConnect Secure Mobility Client) software that may allow attackers to elevate privileges to SYSTEM.
Cisco Secure Client helps employees work from anywhere using a secure virtual private network (VPN) and provides network administrators with telemetry and endpoint management capabilities.
The vulnerability (tracked as CVE-2023-20178) may allow authenticated attackers to elevate privileges to the SYSTEM account used by the Windows operating system in low complexity attacks that do not require user interaction. ‘user.
Successful exploitation requires abusing what Cisco describes as a “specific feature of the Windows installation process”.
Cisco released security updates to fix this security bug last Tuesday when he said his Product Security Incident Response Team (PSIRT) had no evidence of malicious use or public exploit code targeting the bug in the wild.
CVE-2023-20178 has been fixed with the release of AnyConnect Secure Mobility Client for Windows 4.10MR7 and Cisco Secure Client for Windows 5.0MR2.
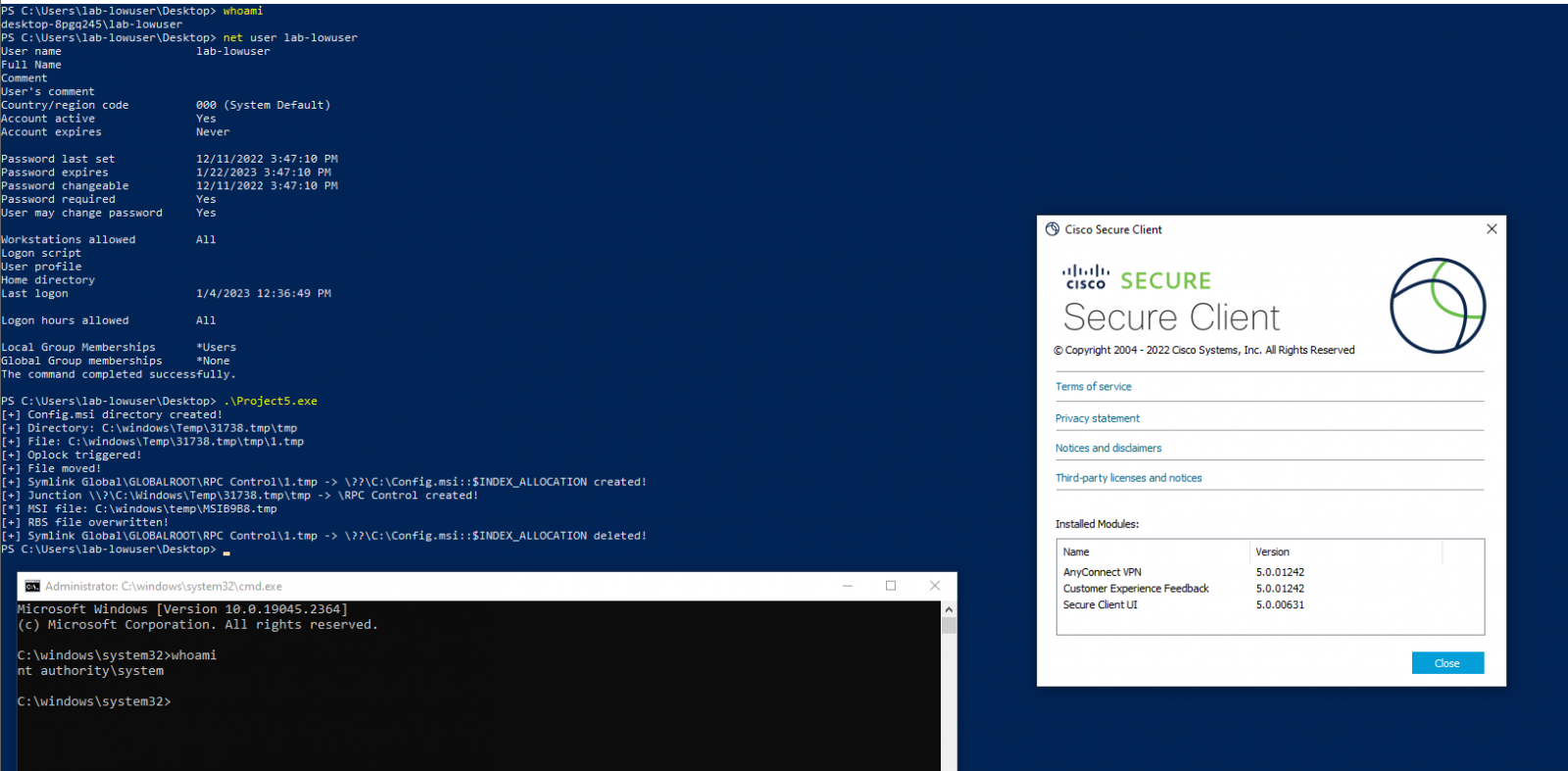
Earlier this week, proof-of-concept (PoC) exploit code was released by security researcher Filip Dragović who discovered and reported the Arbitrary File Delete vulnerability to Cisco.
As Dragović explains, this PoC has been tested on Cisco Secure Client (tested on 5.0.01242) and Cisco AnyConnect (tested on 4.10.06079).
“When a user connects to the vpn, the vpndownloader.exe process is started in [the] background, and it will create [a] directory in c:\windows\temp with default permissions in [the] following format:
“After creating this directory, vpndownloader.exe will check if this directory is empty, and if it is not, it will delete all files/directories in it. This behavior can be abused to perform arbitrary deletion of files as NT Authority\SYSTEM account.”
The attacker can then generate a SYSTEM shell via arbitrary file deletion taking advantage of this behavior of the Windows installer and the fact that a client update process is run after each successful VPN connection, using the technique described here to increase privileges.
In October, Cisco notified customers to fix two other AnyConnect security vulnerabilities (with public exploit code and patched three years prior) due to active exploitation in attacks.
Two years ago, Cisco patched a zero-day AnyConnect with public exploit code in May 2021, six months after its initial disclosure in November 2020,
[ad_2]
Source link
