[ad_1]

A hacker is using fake code-signing certificates impersonating cybersecurity firm Emsisoft to target customers using its security products, hoping to bypass their defenses.
Code signing certificates are digital signatures used to sign an application so that users, software, and operating systems can verify that the software has not been tampered with since the publisher signed it.
Threat actors try to take advantage of this by creating fake certificates whose name appears to be associated with a trustworthy entity but, in reality, they are not valid certificates.
In a new security advisory, Emsisoft has warned that one of its customers was being targeted by hackers using an executable signed by a spoofed Emsisoft certificate. The company believes this was done to trick the customer into thinking any detection was a false positive and to allow the program to run.
“We recently observed an incident in which a fake code-signing certificate purporting to belong to Emsisoft was used in an attempt to obfuscate a targeted attack against one of our customers,” Emsisoft said in the security consulting.
“The organization in question used our products and the attacker’s goal was to get that organization to authorize an application that the threat actor installed and intended to use by making its detection appear as a false positive .”
While the attack failed and Emsisoft’s security software blocked the file due to the invalid signature, the company is warning customers to remain vigilant against similar attacks.
Emsisoft spoofing for remote access
Emsisoft claims that the threat actor likely gained initial access to the compromised device via brute force RDP or by using stolen credentials belonging to an employee of the targeted organization.
After accessing the endpoint, the attackers attempted to install MeshCentral, an open-source remote access application generally trusted by security products because it is used for legitimate purposes.
However, this MeshCentral executable was signed with a fake Emsisoft certificate claiming to be from “Emsisoft Server Trusted Network CA”.
While Emsisoft didn’t share details about the executable, BleepingComputer discovered it was called ‘smsse.exe’ [VirusTotal]as shown below.
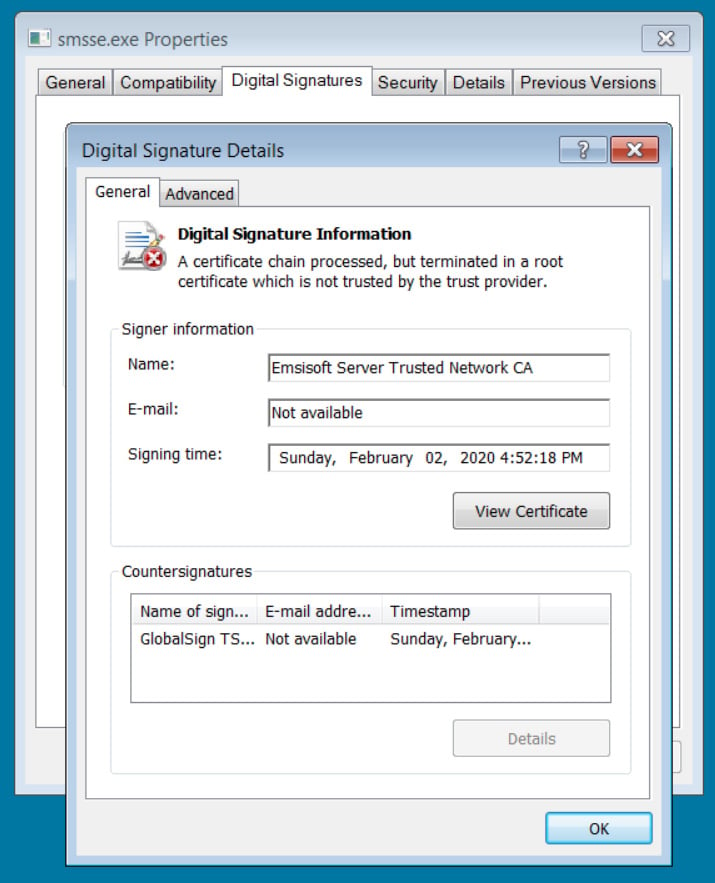
Source: BleepingComputer
When Emsisoft’s security product scanned the file, it marked it as “Unknown” due to the invalid signature and quarantined the file.
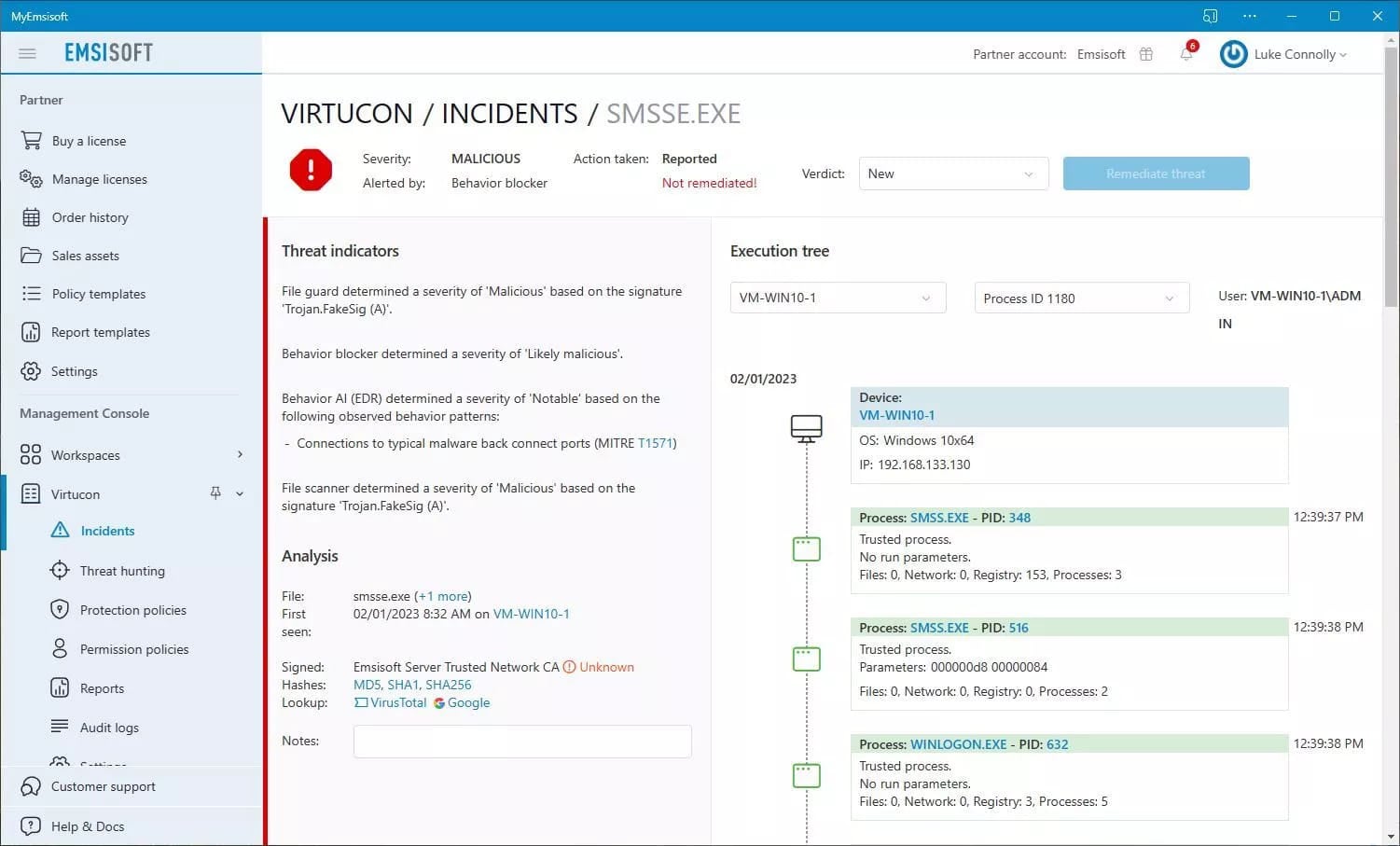
However, if an employee were to treat this warning as a false positive due to the name of the digital signature, they might have allowed the application to run, allowing the attacker to gain full access to the device.
This remote access could then be used to disable protections, spread laterally within the network, steal sensitive data and potentially deploy ransomware.
Emsisoft warns that executables should only be trusted after confirming that a file is not malicious and contacting security vendors before allowing an executable to run with an invalid signature.
“This incident demonstrates the need for organizations to have multiple layers of protection so that if one layer fails to block an attack, another layer will,” says Emsisoft.
The company also suggests system administrators set a password on their Emsisoft product to prevent it from being tampered with or disabled in the event of a breach, such as this one.
[ad_2]
Source link
