[ad_1]
A new Emotet phishing campaign is targeting US taxpayers by impersonating W-9 tax forms allegedly sent by the Internal Revenue Service and companies you work with.
Emotet is a notorious malware infection distributed through phishing emails that previously contained Microsoft Word and Excel documents with malicious macros that installed the malware.
However, after Microsoft started blocking macros by default in downloaded Office documents, Emotet switched to using Microsoft OneNote files with embedded scripts to install Emotet malware.
Once Emotet is installed, the malware will steal victims’ emails for future use response chain attackssend other spam and ultimately install other malware which provides initial access to other threat actors, such as ransomware gangs.
Emotet prepares for tax season in the United States
Emotet malware operations typically use themed phishing campaigns to coincide with the holidays and annual business activities, such as the current tax season in the United States.
In the new phishing campaigns observed by security researchers from Malwarebytes And Palo Alto Networks Unit42Emotet malware targets users with emails containing fake W-9 tax form attachments.
In the campaign seen by Malwarebytes, threat actors send emails titled “IRS Tax Forms W-9,” while posing as an Internal Revenue Service “inspector.”
These phishing emails contain a ZIP archive named “W-9 form.zip” which contains a malicious Word document. This Word document was bloated to over 500MB to make it harder for security software to detect it as malicious.
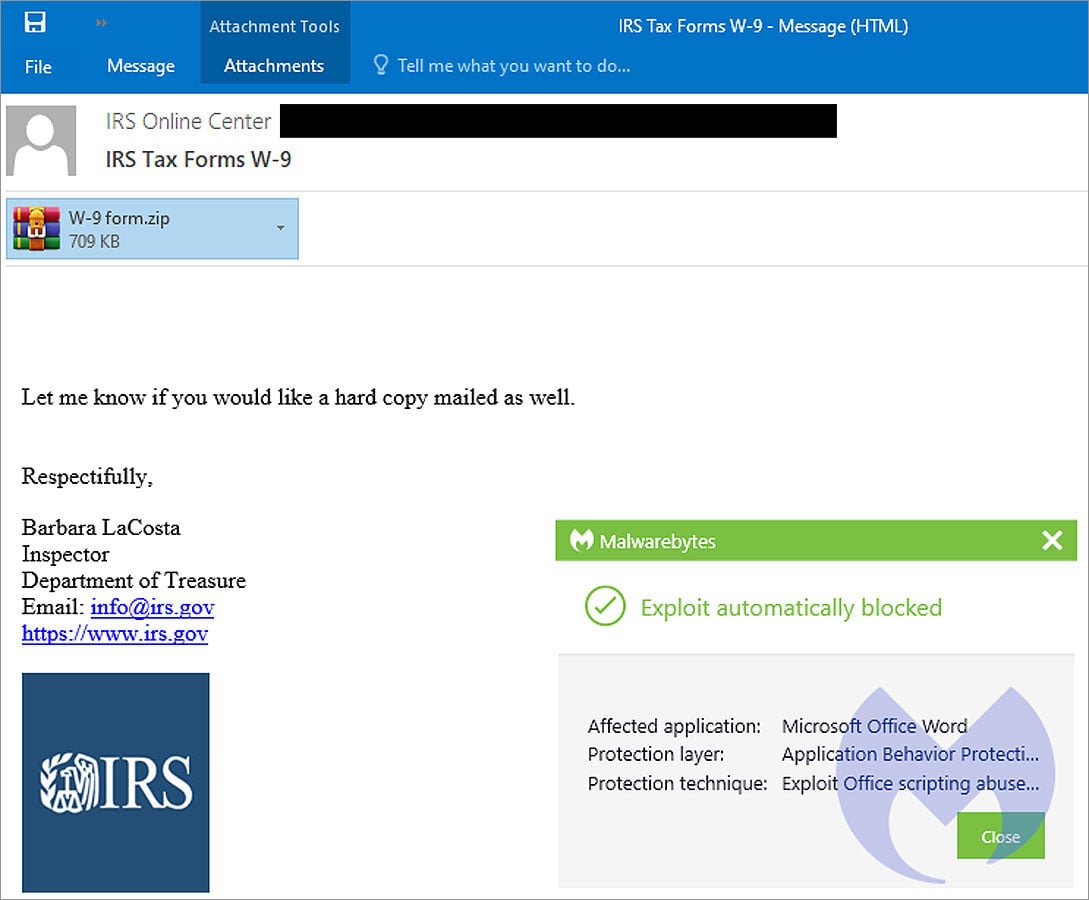
Source: Malwarebytes
However, now that Microsoft blocks macros by default, users are less likely to bother to enable macros and get infected with malicious Word documents.
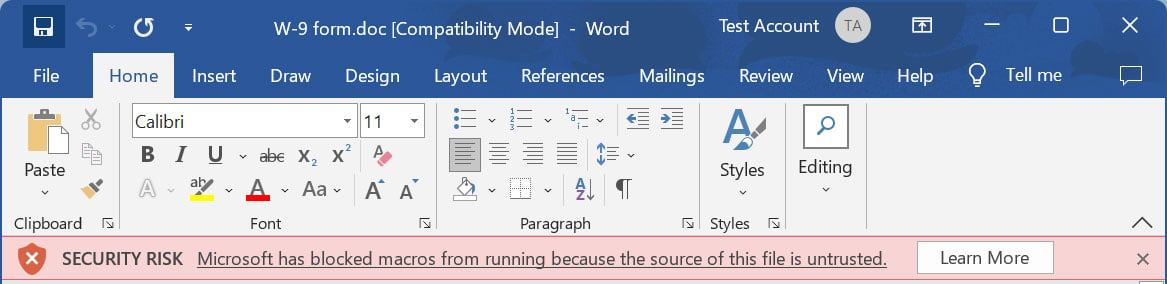
Source: BleepingComputer
In a phishing campaign seen by Brad Duncan of Unit42, threat actors circumvent these restrictions by using Microsoft OneNote documents with embedded VBScript files that install the Emotet malware.
This phishing campaign uses reply string emails containing emails claiming to be from business partners sending you W-9 forms as shown below.
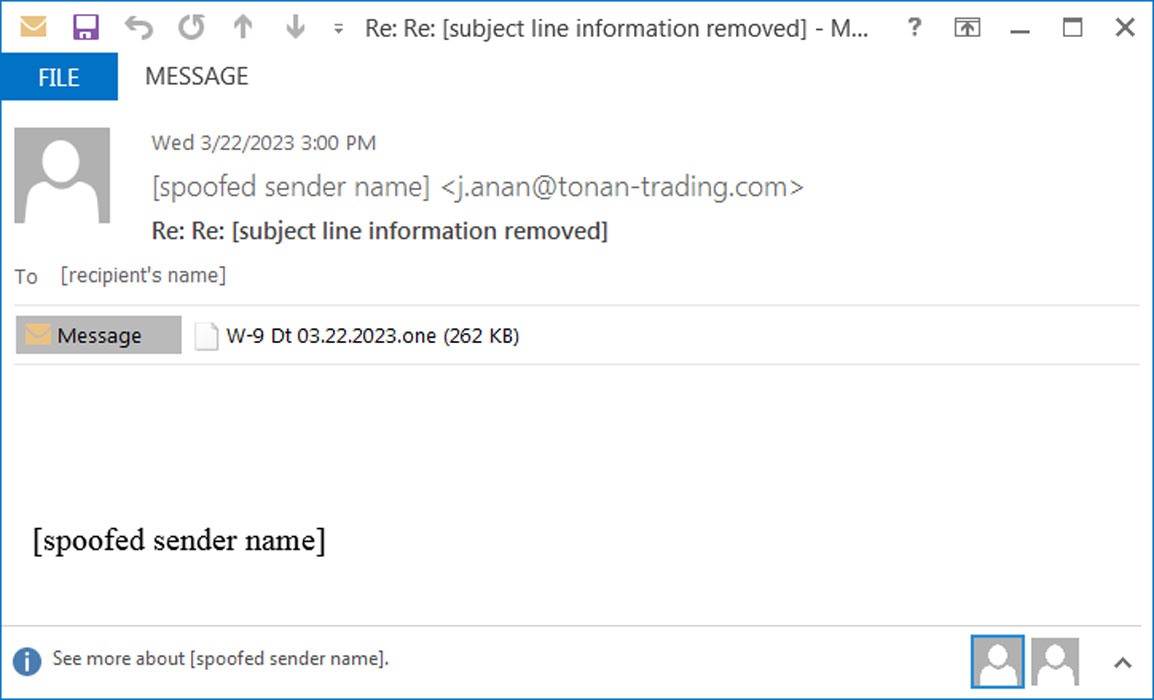
Source: Unit42
Attached OneNote documents will pretend to be protected, asking you to double-click the “View” button to see the document properly. However, hidden under this Show button is a VBScript document that will be launched instead.
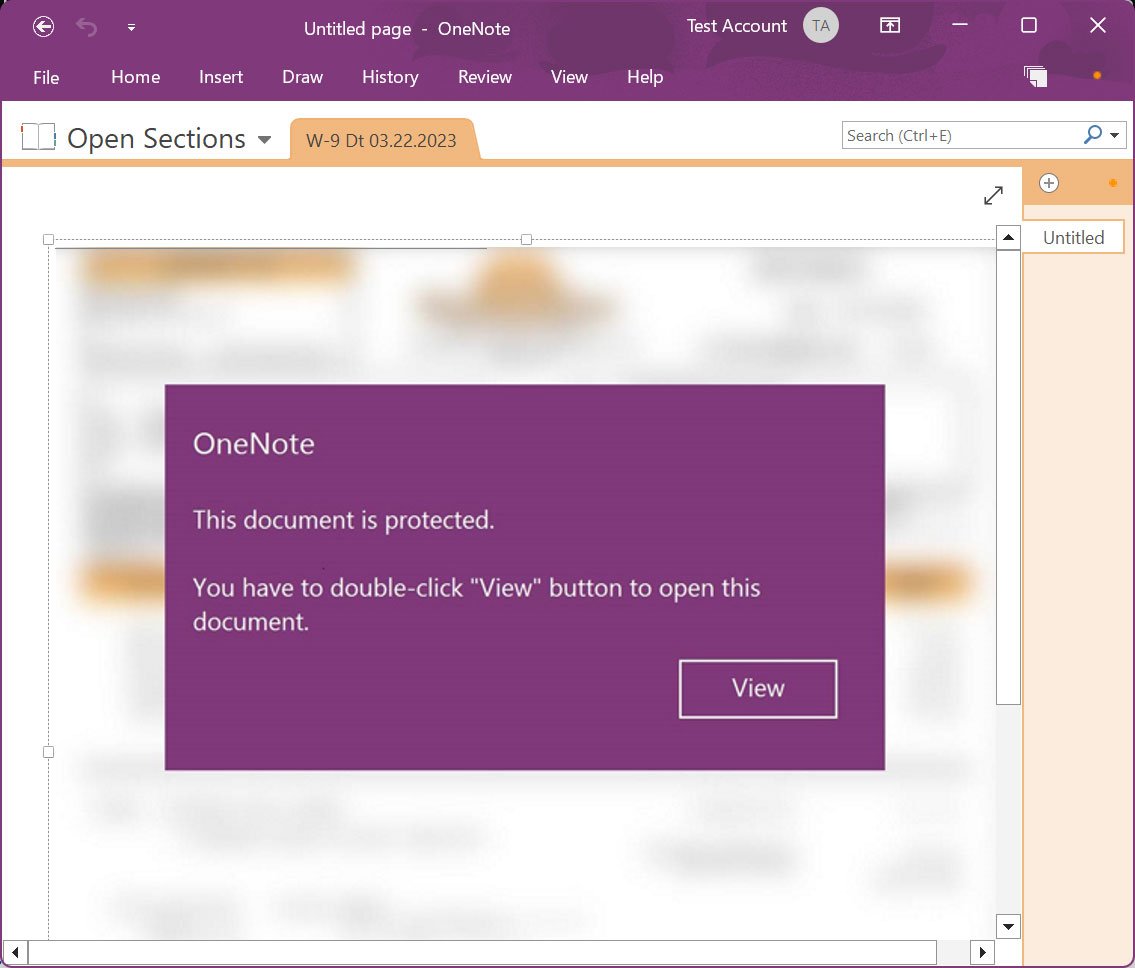
Source: BleepingComputer
When launching the embedded VBScript file, Microsoft OneNote warns the user that the file may be malicious. Unfortunately, history has shown us that many users ignore these warnings and simply allow the files to run.
Once executed, the VBScript will download the Emotet DLL and run it using regsvr32.exe.
The malware will now run silently in the background, stealing emails, contacts, and waiting for other payloads to install on the device.
If you receive emails claiming to be W-9s or other tax forms, scan the documents first with your local anti-virus software. However, due to the sensitive nature of these forms, uploading them to cloud-based scanning services like VirusTotal is not suggested.
Normally, tax forms are distributed as PDF documents and not as Word attachments, so if you receive one, avoid opening it and enabling macros.
Finally, tax forms are unlikely to ever be sent as OneNote documents, so immediately delete the email and don’t open it if you receive one.
As always, the best line of defense is to reject any email from people you don’t know, and if you know them, contact them first by phone to confirm if they sent it.
[ad_2]
Source link
