[ad_1]

Extortion group Donut (D0nut) has been confirmed to deploy ransomware in double extortion attacks against the company.
BeepComputer first reported extortion group Donut in August, linking them to attacks on Greek natural gas company DESFA, British architectural firm Sheppard Robson and multinational construction company Sando.
Strangely, data from Sando and DESFA has also been published on several ransomware operation sites, with the Sando attack claimed by Hive ransomware and DESFA claimed by Ragnar Locker.
Unit 42 Researcher Doel Santos also shared that TOX ID used in ransom notes has been seen in samples of HelloXD ransomware.
This cross posting of stolen data and affiliation leads us to believe that the threat actor behind Donut Leaks is an affiliate for many operations, now trying to monetize the data in their own operation.
Donut ransomware
This week, BleepingComputer found a sample [VirusTotal] of an encryptor for Operation Donut, aka D0nut, showing that the group uses its own custom ransomware for double extortion attacks.
The ransomware is still being scanned, but once executed, it will search for files matching specific extensions to encrypt. When encrypting files, the ransomware will avoid files and folders containing the following strings:
Edge
ntldr
Opera
bootsect.bak
Chrome
BOOTSTAT.DAT
boot.ini
AllUsers
Chromium
bootmgr
Windows
thumbs.db
ntuser.ini
ntuser.dat
desktop.ini
bootmgr.efi
autorun.inf
When a file is encrypted, Donut ransomware will append the .d0nut extension to encrypted files. So for example 1.jpg will be encrypted and renamed to 1.jpg.d0nut as shown below.
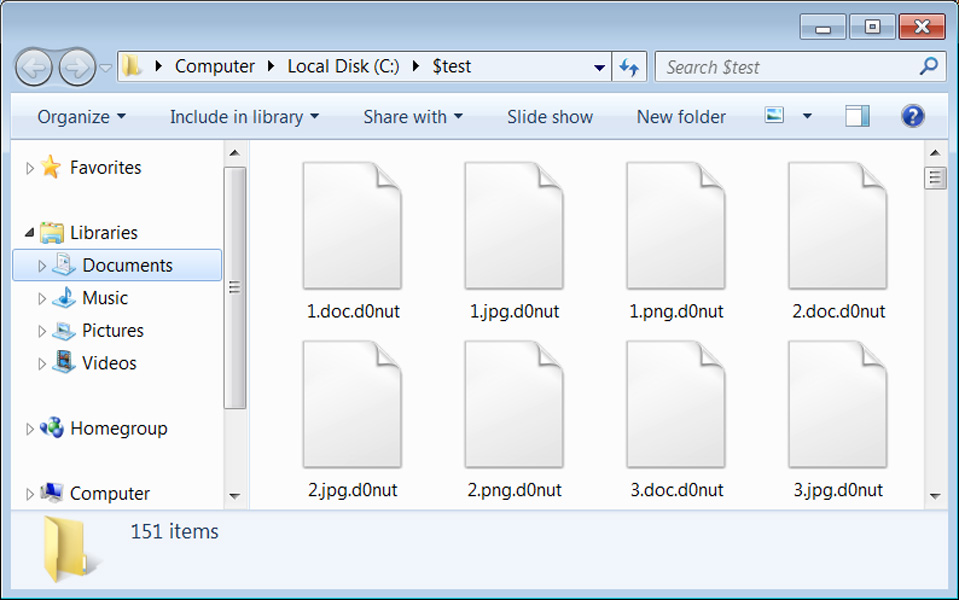
Source: BleepingComputer
Operation Donut Leaks has a theatrical flair, uses interesting graphics, a bit of humor, and even features a builder for an executable that acts as a gateway to their Tor data leak site (see below).
This flair is especially visible in its ransom notes, where they use different ASCII arts, such as the spinning ASCII donut below.
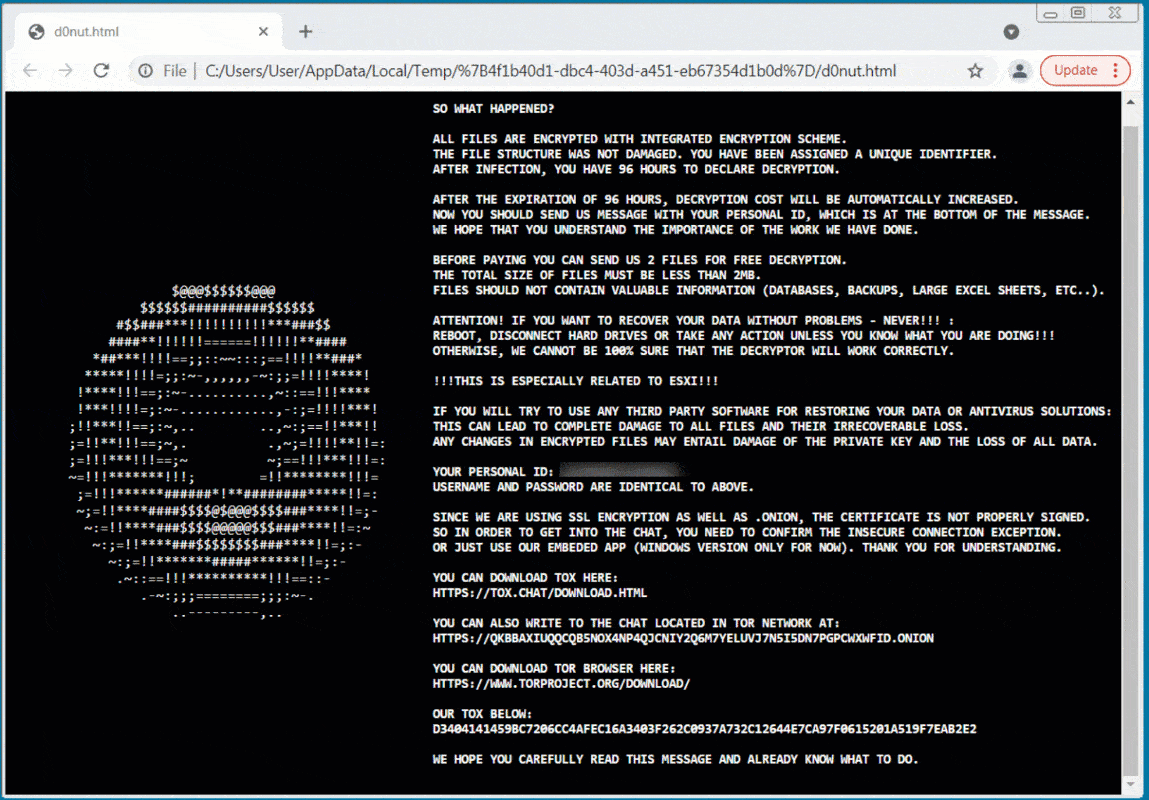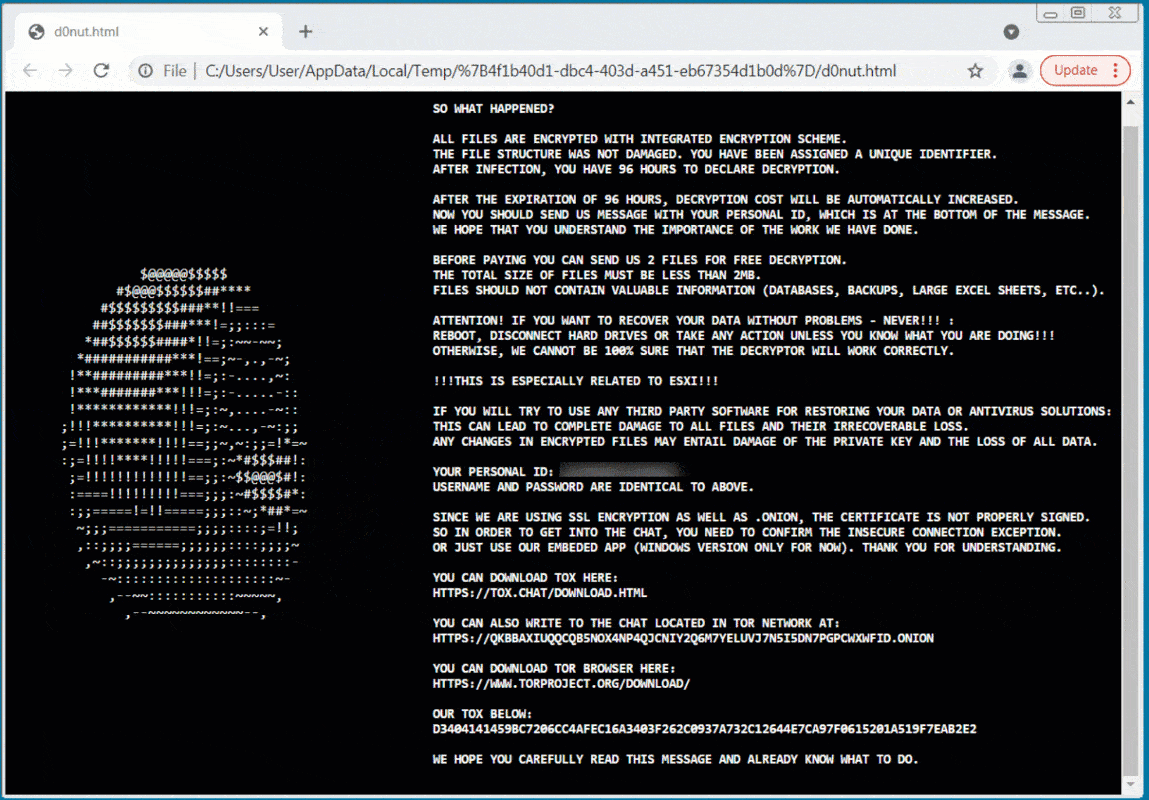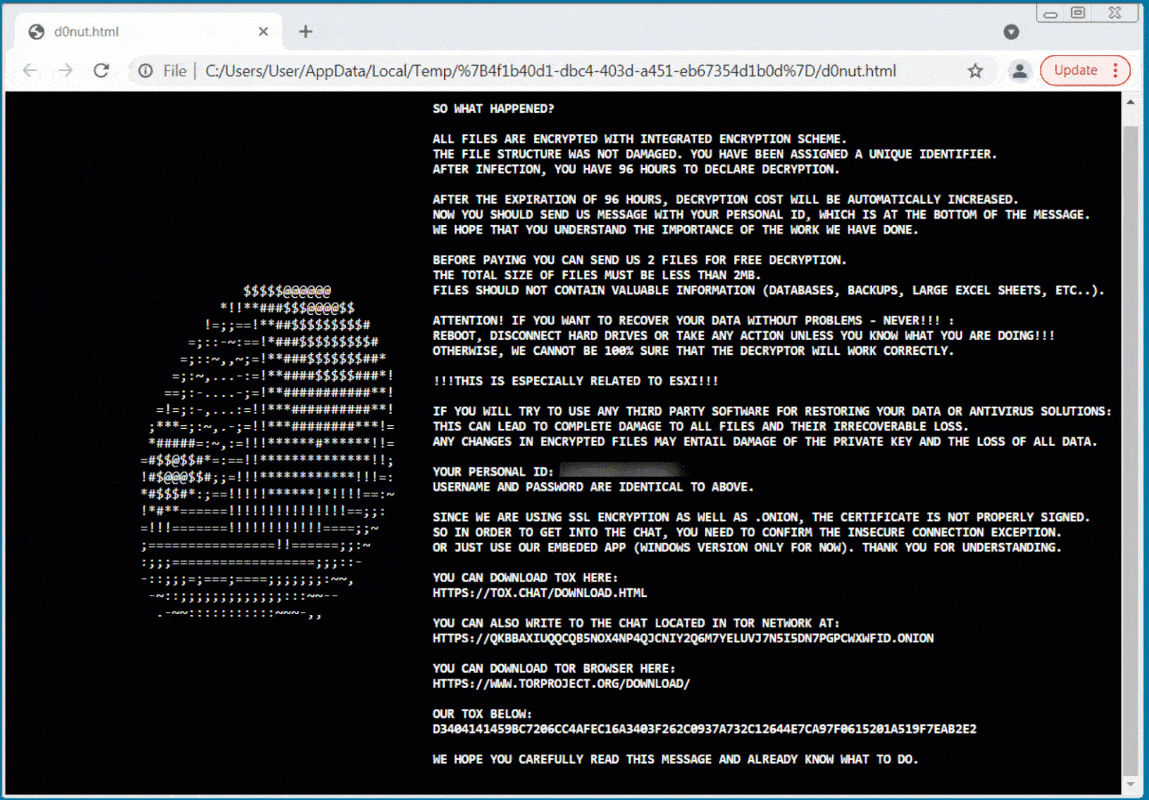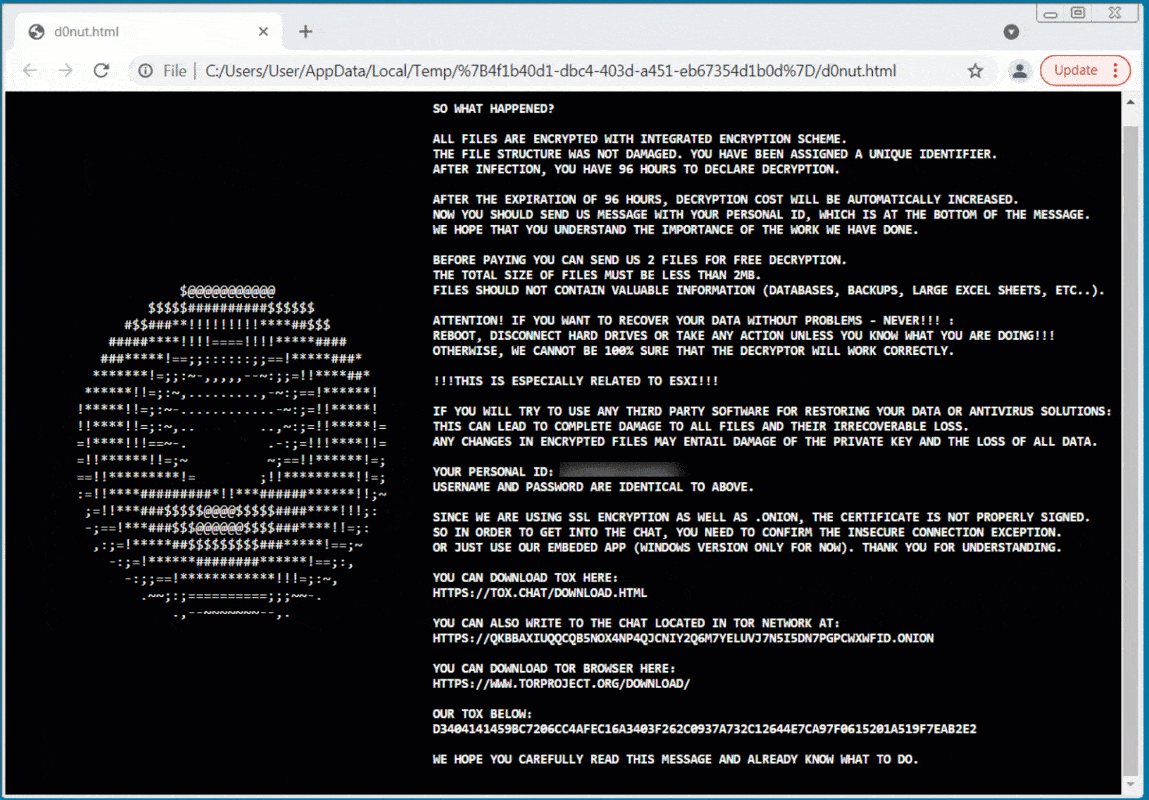
Another ransomware note seen by BleepingComputer pretends to be a command prompt displaying a PowerShell error, which then prints a scrolling ransom note.
The ransom notes are heavily obfuscated to avoid detection, with all encoded strings and JavaScript decoding the ransom note in the browser.
These ransom notes include different ways to contact threat actors including through TOX and a Tor trading site.
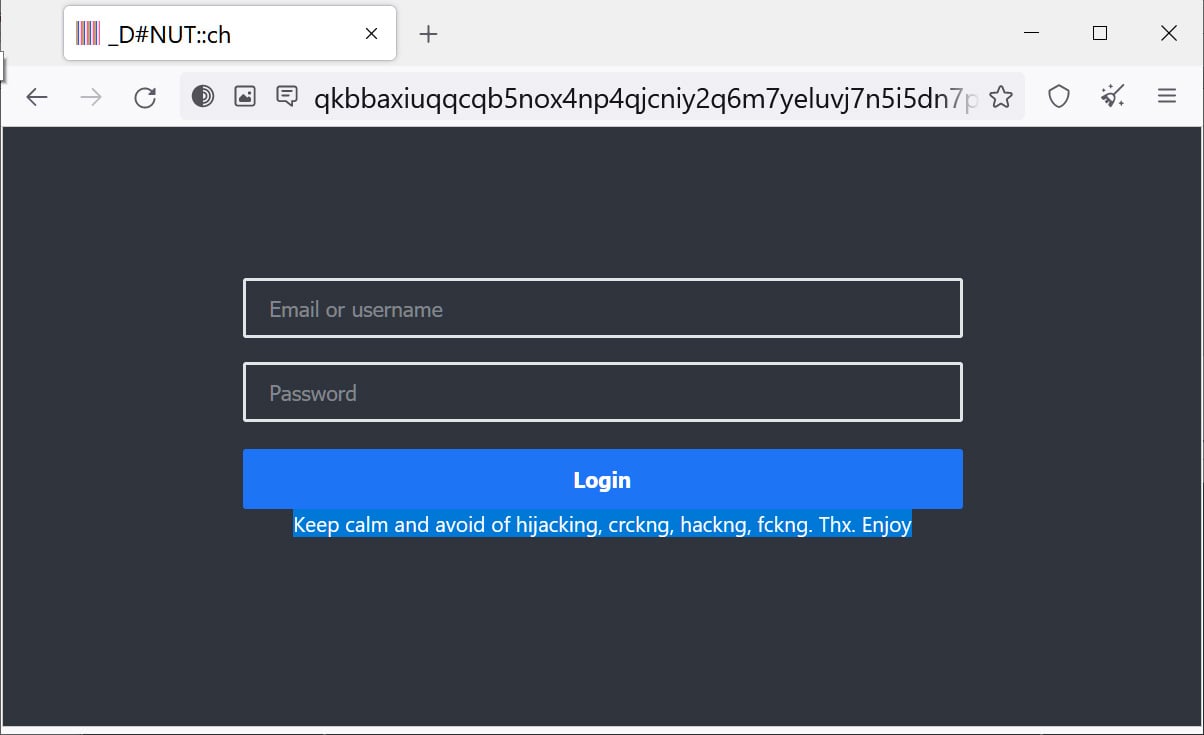
Source: BleepingComputer
The Donut ransomware operation also includes a “builder” on their data leak site which consists of a bash script to create a Windows and Linux Electron application with an integrated Tor client to access their data leak sites.

This app is currently “broken” because it uses HTTPS URLs, which are not currently operational.
Overall, this extortion group is one to watch, not just for its apparent skill, but also for its ability to market itself.
[ad_2]
Source link
