[ad_1]

Stealer logs represent one of the main threat vectors for modern businesses. However, many security teams still focus on leaked credentials and ignore the significant threat posed by devices infected with infostealer malware.
This how-to article from Flare will dive into the lifecycle of thieving malware and provide guidance for detection and remediation.
what is a Thief’s Diary? Several variants of infostealer malware exist, but the main groups we often come across are Red line, Raccoon, Vidar and Titan. This malware infects victim computers and exports passwords saved in the browser, as well as host data such as OS version, IP address, clipboard data, browser history, saved credit cards and cryptocurrency wallet data.
The malware then sends this data back to the threat actor’s command-and-control infrastructure. It is then sold as individual ads on dedicated dark web marketplaces or distributed via Cybercrime Telegram channels.
The Stealer Malware Lifecycle – Malware as a Service Provider
The growth of the cybercrime ecosystem has seen an increasing trend towards the commoditization of malware, and infostealer malware is no exception.
Malware-as-a-service vendors sell access to major infostealer variants on specialized Telegram channels for a fixed monthly price, usually between $100 and $300, depending on the age of the malware. and with lifetime subscriptions available.
Buyers also have access to a web portal tied to a command and control infrastructure, which can be used to collect victim logs in a centralized location.
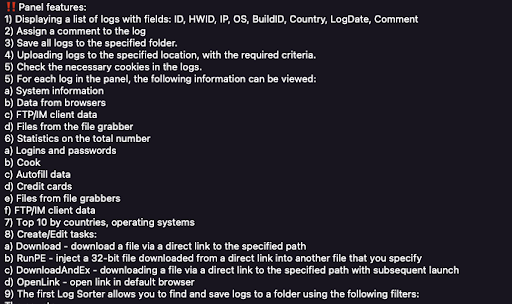
Source: Flare
The Stealer Malware Lifecycle – Distribution
Threat actors who purchase theft logs bear the responsibility of distributing the malware to victims. This distribution usually occurs through three main vectors: pirated software downloads, illegitimate advertisements, and spear phishing emails for targeted attacks on organizations.
Once the Infostealer malware is downloaded to the victim’s computer, it automatically runs and attempts to establish communication with the C2 infrastructure. After successful communication, credentials and host data are returned to the threat actor.
The Stealer Malware Lifecycle – Resale
The vast majority of thieves’ logs come from personal computers without access to corporate computing environments. In many cases, threat actors use flight logs to gain access to VPN environments, streaming services, and other basic consumer applications. However, logs that provide access to corporate computing environments are highly prized.
At Flare, we process over one million flight logs per week and estimate that at least 1% contain access to corporate computing environments. Stealer logs are typically distributed through one of four main channels:
Russian Market Genesis Marketplace Public Telegram Rooms “VIP” Private Telegram Rooms
Using Flare’s cyber-intel SaaS platform, we have found that logs sold in the Russian and Genesis markets come with a basic list of saved credentials that have been saved in the browser. Full victim machine information and passwords are provided upon purchase.
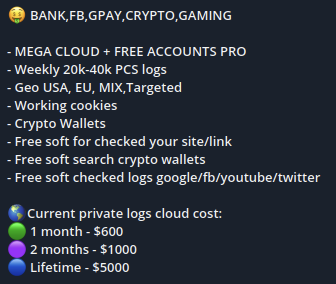
Source: Flare
These marketplaces are designed for cybercriminals to “buy” specific credentials, and prices for credentials often vary widely depending on the type of credentials being sold. For example, the average price of an infected device listed on the Genesis Marketplace is $14.39, but with a health care domain listed, the price jumps to $93.91 and access to banking services drops the price north of $110 per device.
Private Diary Channel Announcement on Telegram
The logs distributed via Telegram are totally different, they usually appear in large zip files containing hundreds or thousands of individual logs. They are often distributed in public Telegram rooms, but a significant number are also shared on VIP “paid access” private Telegram channels.
These typically cost between $300 and $900 per month and are limited to 10-15 users. This provides exclusivity to threat actors in the channel, allowing them to retrieve and exploit the most valuable logs before they are likely later distributed to a public telegram room.

Source: Flare
The newspapers are distributed for free on a public Telegram channel.
The Stealer Malware Lifecycle – Initial Access Brokers
We believe that many initial access brokers, who are active on dark web forums such as exploit.in and xss.is, are sifting through the millions of flight logs found in VIP Telegram channels and Russian markets and Genesis.
Their purpose is to identify logs containing enterprise access, which can then be used to establish and expand enterprise access. Purchasing logs that already have multiple sets of corporate credentials greatly simplifies the process of compromising a business.
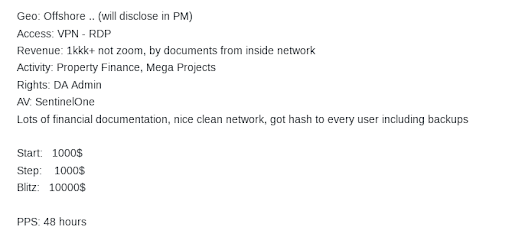
Source: Flare
This allows the threat actor to focus on validating and extending initial access rather than establishing it initially. Once access is validated, Initial Access Brokers (IABs) auction off the established access for prices ranging from thousands to tens of thousands of dollars, depending on the victimized organization and the level of access established.
An article from Exploit.in selling access to a corporate environment. Note that the threat author lists notable information about the affected company in addition to the AV used by the victim. Bidding starts at $1,000 with additional $1,000 increments and a “buy it now” price of $10,000.
Detect and Fix Stealer Logs with Flare
Flare’s SaaS platform provides organizations with personalized, high-value threat exposure management. To burst detects threats on hundreds of dark web marketplaces and forumsthousands of illicit telegram channels and clear risk web sources.
Our SaaS platform integrates with your existing security program in 30 minutes with native integrations that allow you to create a threat-focused cybersecurity program. Request a product demo today to find out more.
Sponsored and written by To burst
[ad_2]
Source link
