[ad_1]

A digitally signed, Trojan-protected version of the 3CX Voice Over Internet Protocol (VOIP) desktop client is reportedly being used to target corporate customers as part of an ongoing supply chain attack.
3CX is a VoIP IP PBX software development company whose 3CX phone system is used by over 600,000 businesses worldwide and has over 12 million daily users.
THE company client list includes a long list of leading companies and organizations like American Express, Coca-Cola, McDonald’s, BMW, Honda, AirFrance, NHS, Toyota, Mercedes-Benz, IKEA and HolidayInn.
According to alerts from security researchers from Sophos and CrowdStrike, attackers are targeting both Windows and macOS users of the compromised 3CX softphone app.
“Malicious activity includes tagging to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on keyboard activity,” the threat intelligence team said. CrowdStrike threats. said.
“The most common post-exploit activity observed to date is the creation of an interactive command shell,” Sophos added in an advisory posted through its Managed Detection and Response service.
As CrowdStrike suspects a North Korean state-backed hacking group, it follows as Labyrinth Collima is behind this attack, Sophos researchers say they “cannot verify this attribution with a high degree of confidence”.
The activity of Labyrinth Collima is known to overlap with other threat actors tracked like Lazarus Group by Kaspersky, Covellite by Dragos, UNC4034 by Mandiant, Zinc by Microsoft and Nickel Academy by Secureworks.
Marked as malicious by security software
CrowdStrike reports that the trojanized version of the 3CX desktop client will connect to one of the following attacker-controlled domains:
| akamacontainer[.]com | msedgeinfopackage[.]com |
| akamaitechcloudservices[.]com | msstorageazure[.]com |
| azureploystore[.]com | msstorageboxes[.]com |
| azuronlinecloud[.]com | office complements[.]com |
| azureonlinestorage[.]com | desktopstorage box[.]com |
| dunamistrd[.]com | pbxcloudeservices[.]com |
| glcloudservice[.]com | pbxphonenetwork[.]com |
| qwepoi123098[.]com | zacharryblogs[.]com |
| sbmsa[.]wiki | pbxsources[.]com |
| sourceslabs[.]com | newspaper[.]org |
| visualstudiofactory[.]com |
Some of the domains mentioned by clients that the desktop client tried to connect to include azureonlinestorage[.]com, msstorageboxes[.]com and msstorageazure[.]com.
BleepingComputer tested an allegedly trojanized version of the software but was unable to trigger connections to these domains.
However, several customers in the 3CX forums have stated that they have been receiving alerts for a week, March 22indicating that the VoIP client application has been marked as malicious by SentinelOne, CrowdStrikeAnd ESET security software.
Customers report that security alerts are triggered after installing 3CXDesktopApp Windows versions 18.12.407 and 18.12.416 or 18.11.1213 and latest version on Mac.
One of the examples of 3CX softphone clients infected with a Trojan share by CrowdStrike was digitally signed over three weeks ago on March 3, 2023 with a legitimate 3CX Ltd certificate issued by DigiCert.
BleepingComputer confirmed that this same certificate was used in older versions of the software.
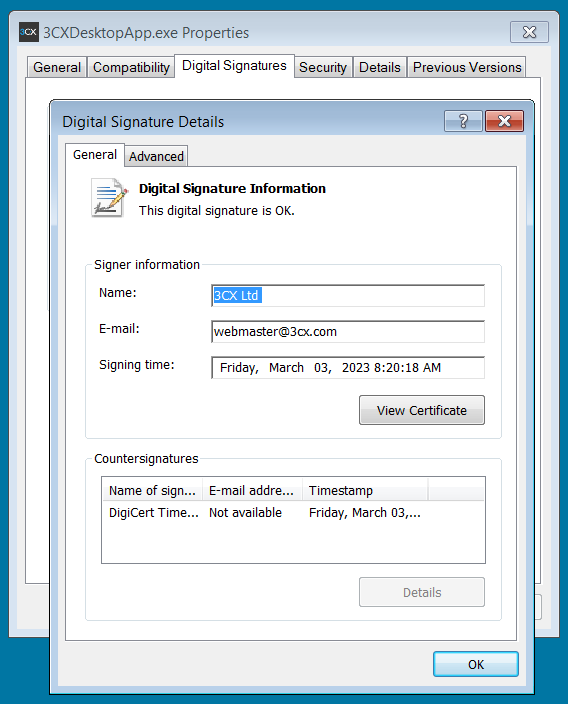
While SentinelOne detects “penetration framework or shellcode” when scanning the 3CXDesktopApp.exe binary and ESET marks it as a “Win64/Agent.CFM” Trojan, the Falcon Managed Threat Hunting Service CrowdStrike’s OverWatch warns users to investigate their systems for malicious activity “as a matter of urgency”. “
Even though 3CX support team members tagged it as a potential SentinelOne false positive in one of the forum threads filled with customer reports on Wednesday, the company has yet to publicly acknowledge the issues.
A 3CX spokesperson did not respond to a request for comment when contacted by BleepingComputer earlier today.
[ad_2]
Source link
