[ad_1]

Industrial cybersecurity firm Dragos today revealed what it describes as a “cybersecurity event” after a known cybercrime gang attempted to breach its defenses and infiltrate the internal network to encrypt devices.
While Dragos says the threat actors did not breach its network or cybersecurity platform, they did gain access to the company’s SharePoint cloud service and contract management system.
“On May 8, 2023, a known cybercriminal group attempted and failed in an extortion scheme against Dragos. No Dragos system was hacked, including anything related to the Dragos platform,” the company said. said.
“The criminal group gained access by compromising the personal email address of a new sales employee before his start date, and then used his personal information to impersonate the Dragos employee and accomplish the first steps in the employee onboarding process.”
After breaching Dragos’ SharePoint cloud platform, the attackers downloaded “general usage data” and accessed 25 Intel reports that were generally only available to customers.
In the 16 hours they gained access to the employee’s account, the threat actors also lacked access to multiple Dragos systems, including its email, IT help desk, financial systems, Request for Proposals (RFP), Employee Recognition and Marketing, because of his role. rule-based access control (RBAC) rules.
After failing to break into the company’s internal network, they sent an extortion email to Dragos executives 11 hours after the attack began. The message was read 5 hours later because it was sent outside business hours.
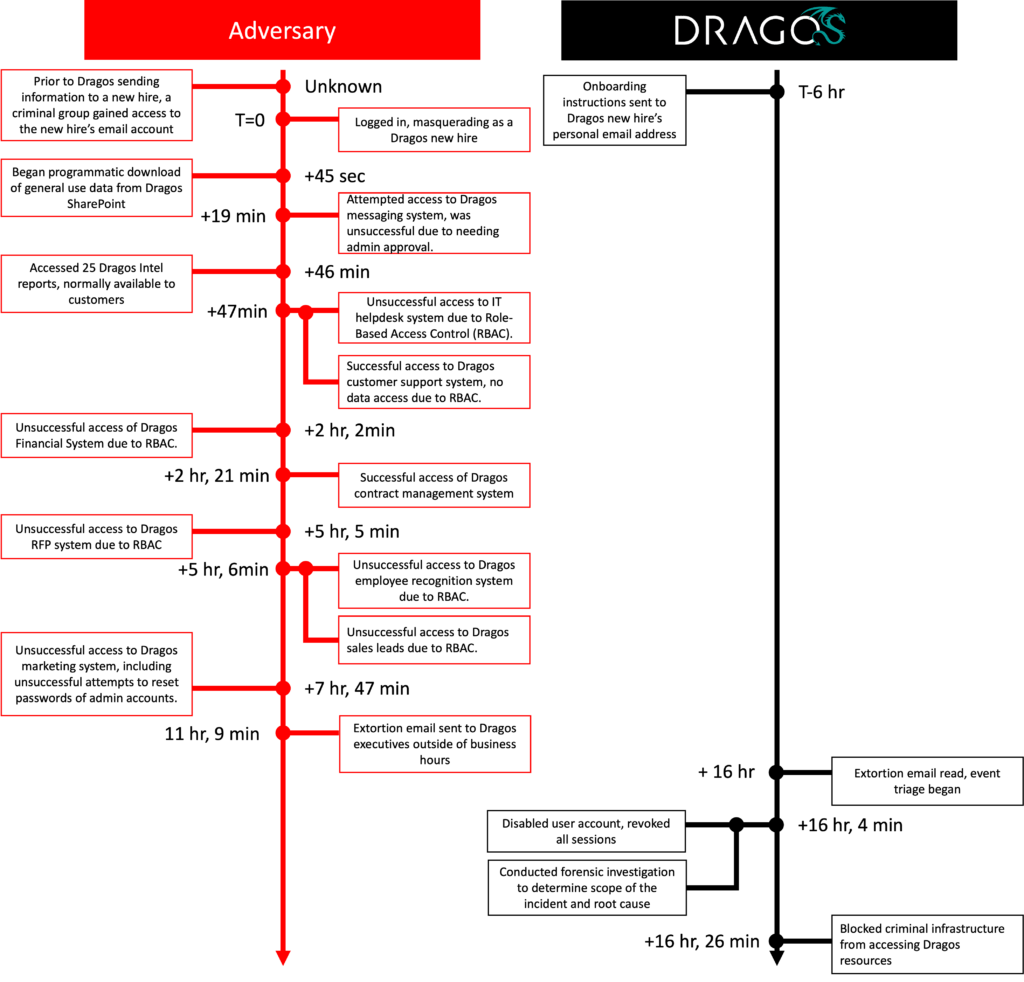
Five minutes after reading the extortion message, Dragos disabled the compromised trusted account, revoked all active sessions, and blocked the cybercriminals’ infrastructure from accessing corporate resources.
“We are confident that our layered security controls prevented the threat actor from accomplishing what we believe to be their primary objective of launching ransomware,” Dragos said.
“They were also prevented from performing lateral movement, escalating privileges, establishing persistent access, or making changes to infrastructure.”
The cybercrime group also attempted to extort the company by threatening to publicly disclose the incident in messages sent through public contacts and personal emails belonging to Dragos executives, senior executives and their family members. .
“While Dragos’ external incident response company and analysts believe the event is contained, it is an ongoing investigation. Data that has been lost and may become public because we we chose not to pay the extortion are regrettable,” Dragos concluded.
One of the IP addresses listed in the IOCs (144.202.42[.]216) was previously spotted accommodation THE SystemBC Malwarecommonly used by ransomware gangs for remote access to compromised systems.
CTI Researcher Will Thomas from Equinix told BleepingComputer that SystemBC has been used by numerous ransomware gangs, including Conti, ViceSociety, BlackCat, Quantum, Zeppelin and Play, making it difficult to identify the threat actor behind the attack.
Thomas said the IP address was also used in recent BlackBasta ransomware attackspossibly reducing the suspects.
A spokesperson for Dragos said he would respond later when BleepingComputer asked for more details about the cybercrime group behind this incident.
[ad_2]
Source link
