[ad_1]

Malware developers have created a thriving market by promising to add malicious Android apps to Google Play for $2,000 to $20,000, depending on the type of malicious behavior demanded by cybercriminals.
The exact price for these services is negotiated on a case-by-case basis on hacker forums or Telegram channels, allowing cybercriminals to customize malicious Android apps with their own malware or features.
Google Play is Android’s official app store, touted as a trusted and secure way to install apps on mobile devices that taps into an audience of billions of users.
Therefore, the ability to add a malicious Android app to the trusted Google Play store provides a wide target base to steal credentials and data, conduct financial fraud, or serve unwanted advertisements.
A Booming Android Malware Market
In a new report from Kaspersky, researchers illustrate how threat actors offer services that promise to add malicious Android apps to Google Play.
These services are offered through Telegram, dark web marketplaces and hacking forums which allow hackers to promote their services.
Malware developers promise to hide malware in legitimate-looking apps that pose as antivirus programs, cryptocurrency asset managers, QR code scanners, small games, and mobile apps. met.
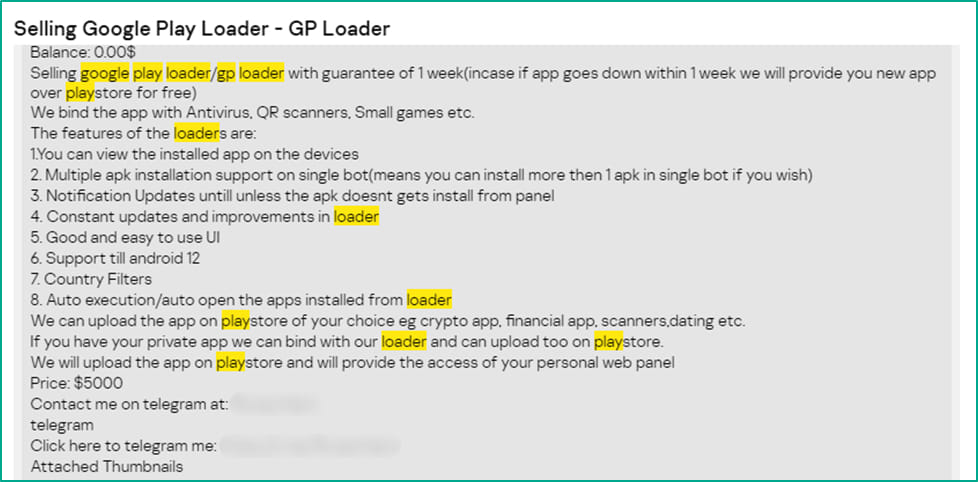
Kaspersky reports that aside from Google Play loaders, which average around $7,000, cybercriminals also sell services such as malware obfuscation for $8-30 or “clean” Google developer accounts that cost $60.
These malicious but harmless-looking apps are released on Google Play but include the ability to grab malicious code through a later update. Alternatively, users may receive a notification to install another app from an external source.
These services ensure the app stays on Google Play for at least a week, with some developers promising at least 5,000 installs.
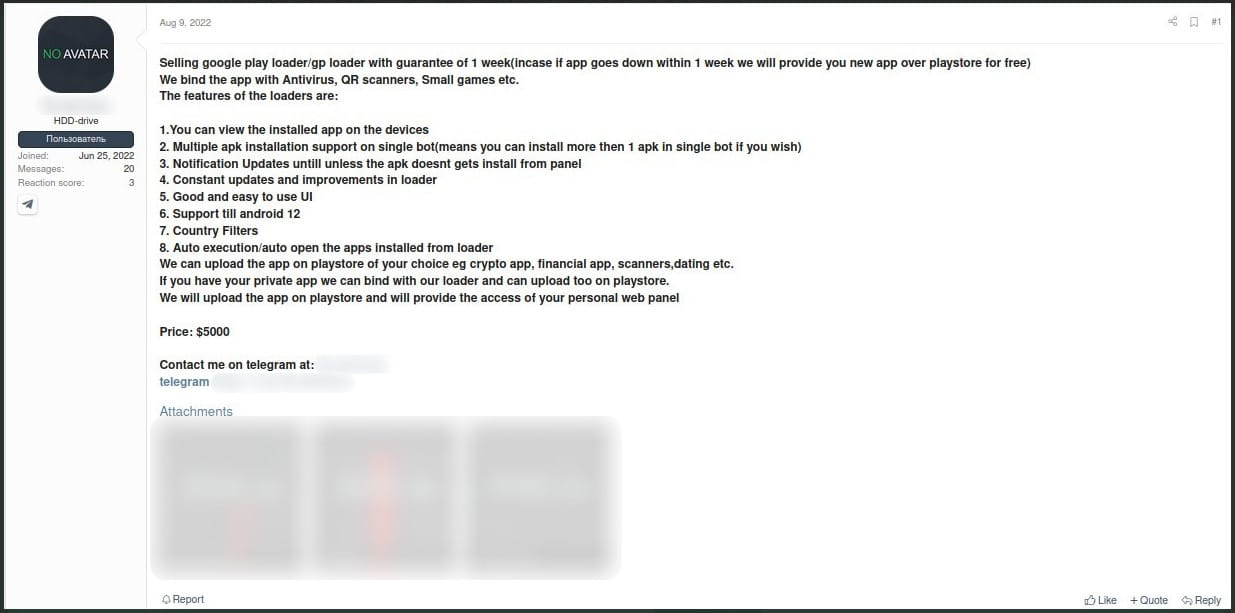
Upon installation, malware-loading apps ask the user to grant risky permissions such as access to the phone’s camera, microphone, or accessibility services and prevents access to the main functions of the application until the requests are approved.
Then, the authors of these apps sell access to their payloads to interested buyers and force them to inject additional payloads.
In some cases seen by Kaspersky, sellers auction their chargers to maximize their profit, starting at $1,500 and setting the “instant buy” price at $7,000.
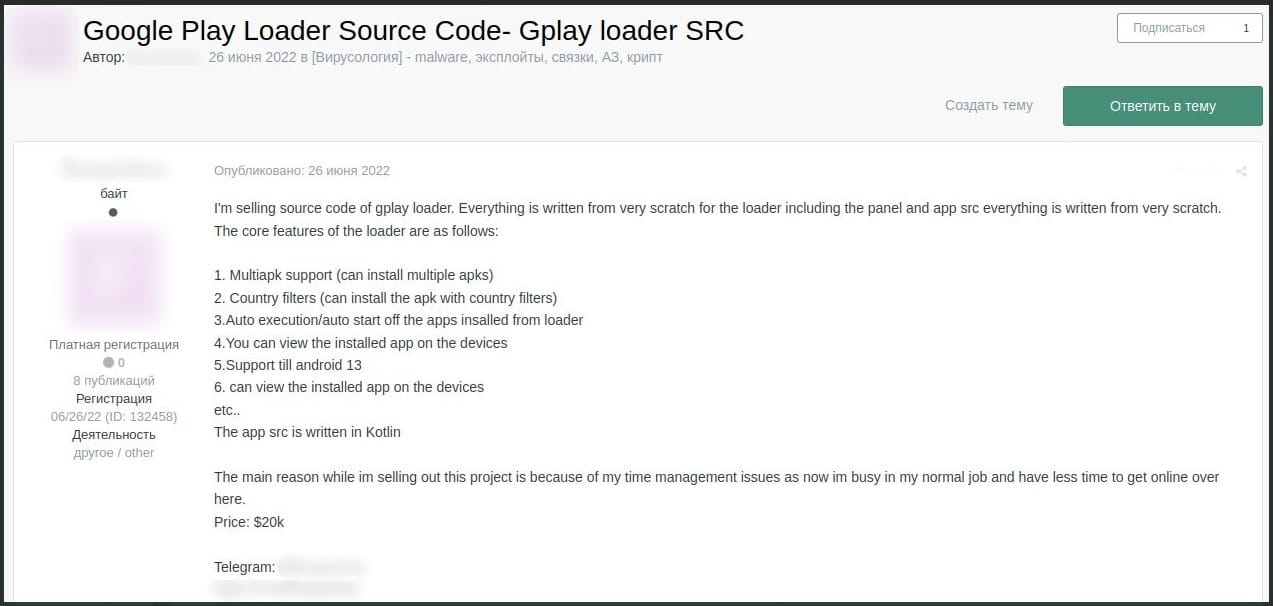
To promote these loaders, vendors post videos showcasing their features, user-friendly interface, granular targeting filters, and more.
“Cybercriminals can also supplement the trojanized application with detection functionality from a debugger or sandbox environment,” explains Kaspersky.
“If a suspicious environment is detected, the loader can shut down its operations or notify the cybercriminal that it has likely been discovered by security investigators.”
To increase the number of malware installations through Google Play loaders, cybercriminals may also offer to run Google Ad campaigns on behalf of their clients.
In addition to loaders, cybercriminals also offer so-called “baiting” services, which involve hiding entire malicious APKs on legitimate apps that can pass Google’s security checks.
Cybersecurity firm ThreatFabric also reported a similar service dubbed ‘zombie‘ in December 2022, pushing Erbium Stealer to thousands of victims.
The cost of these services is significantly lower than that of chargers, asking between $50 and $100 per file.
To defend against these stealthy attacks, Android users should carefully review the permissions requested during app installation, check user reviews on Google Play, and keep the number of apps installed to a minimum.
Most importantly, never install Android APKs from third-party sites, as this is a common distribution method for malware.
[ad_2]
Source link
