[ad_1]

A critical Remote Code Execution (RCE) vulnerability affecting multiple Zoho ManageEngine products is now being exploited in attacks.
The first exploit attempts were observed by cybersecurity firm Rapid7 on Tuesday, two days before Horizon3 security researchers released the public exploit code and an in-depth technical analysis of the flaw.
“Rapid7 addresses various compromises resulting from the exploitation of CVE-2022-47966, a pre-authentication remote code execution (RCE) vulnerability affecting at least 24 on-premises ManageEngine products,” the detection company said. threats. said.
“Rapid7 observed exploitation across all organizations as of January 17, 2023 (UTC).”
This was confirmed by researchers from the Shadowserver Foundation, who stated that they “recover attempts to exploit at least 10 IP addresses for unauthenticated CVE-2022-47966 RCE affecting multiple Zoho ManageEngine products (on which SAML SSO is enabled).”
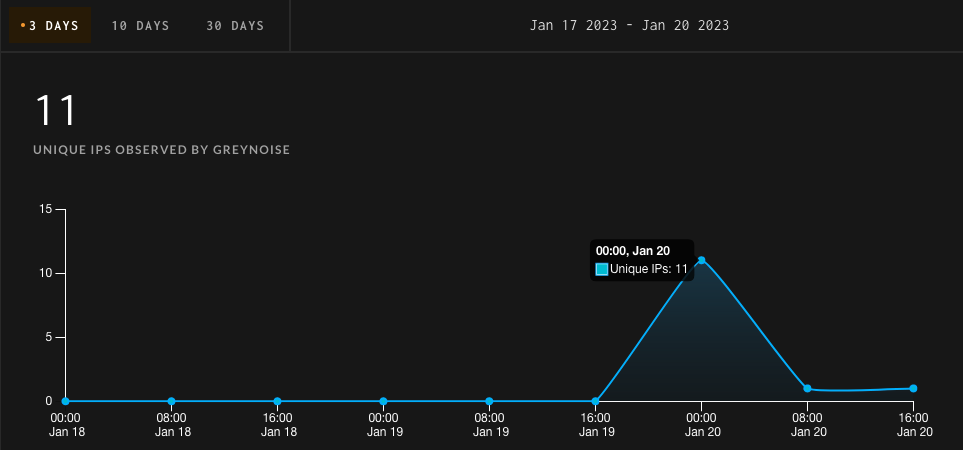
Their findings were also confirmed by threat intelligence firm GreyNoise which began tracking attempts to exploit CVE-2022-47966 last week, January 12.
GreyNoise detected 11 IP addresses targeting Internet-exposed ManageEngine instances vulnerable to CVE-2022-47966 attacks.
At least one of these IP addresses (i.e. 221.226.159.22), assigned to a Linux server on China Telecom Backbone, has previously attempted to compromise unpatched servers against the Log4shell vulnerability.
Post-Exploit Activity on Compromised Devices
While investigating attacks that compromised some of its customers’ ManageEngine instances, Rapid7 also observed post-exploit activity.
The company claims that attackers are using PowerShell scripts to disable Microsoft Defender real-time protection and add the C:\Users\Public folder to Defender’s exclusion lists.
Threat actors also deploy additional payloads, including remote access tools camouflaged as a Windows Service Host service.
One such tool, a Golang protocol tunneling tool named Chisel, similar to the Plink (PuTTY Link) command-line connection tool, is used to create a reverse ssh tunnel (capable of opening a remote shell to bypass firewalls).
In an exploit attempt seen by ShadowServer and shared with BleepingComputer, attackers used curl to download a file from a remote server (106.246.224[.]219/hlmllmo) and run it.
Unfortunately, this file no longer exists on the server, so there is no information about its malicious behavior.
However, the IP address has a the story distribute Linux backdoors to compromised devices using VMware vulnerabilities and the Log4Shell default.
“Organizations using any of the affected products listed in ManageEngine’s advisory should immediately update and examine unpatched systems for signs of compromise, as the exploit code is publicly available and the exploit has already started,” Rapid7 warned.
Horizon found more than 8,300 ServiceDesk Plus and Endpoint Central instances exposed to the Internet and warned of “spray and pray” attacks after estimating that approximately 10% of exposed instances are also vulnerable to attacks.
CISA and the FBI have previously issued joint notices (1, 2) to warn state-sponsored threat actors exploiting flaws in ManageEngine to drop web shells on the networks of organizations across multiple critical infrastructure sectors, including healthcare and financial services.
[ad_2]
Source link
