[ad_1]

Credential stuffing attacks became so prevalent in the first quarter of 2022 that traffic exceeded legitimate login attempts by normal users in some countries.
This type of attack takes advantage of “password recycling”, which involves using the same credential pairs (login name and password) across multiple sites.
After credentials are leaked or brute-forced from a site, threat actors perform a credential stuffing attack that attempts to use the same credentials disclosed on other sites to access user accounts.
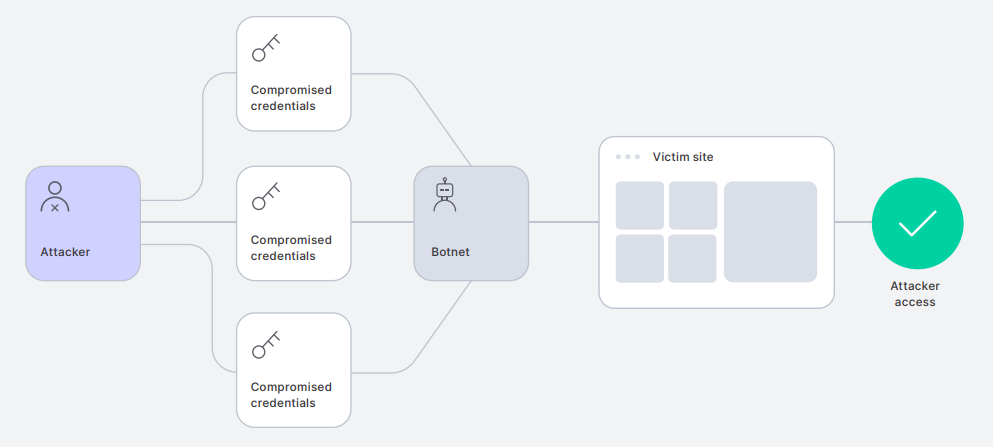
As the The FBI recently warnedthese attacks are growing in volume thanks to the readily available aggregated lists of leaked credentials and the automated tools available to cybercriminals, allowing them to test pairs against numerous sites.
Over 10 billion credential stuffing attempts
Okta reports that the situation worsened in 2022, as the identity and access management company recorded more than 10 billion credential stuffing events on its platform in the first 90 days of 2022.
This number represents approximately 34% of global authentication traffic, which means that a third of all attempts are malicious and fraudulent.
Geographically, the worst cases are Southeast Asia and the United States, where credential stuffing traffic consistently eclipsed normal login attempts throughout the first quarter of 2022.
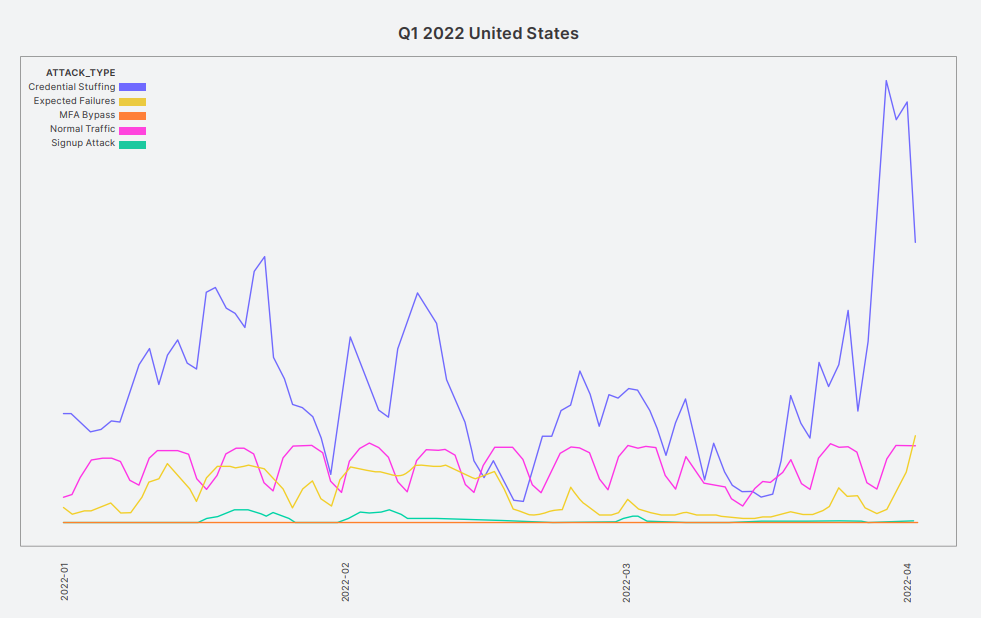
Since most of these attacks follow a “burst” approach, testing a large number of credentials in a short time, affected platforms experience sudden load spikes of up to ten times.
An example in Okta’s report is an attack that lasted nearly two months, peaking in January 2022.
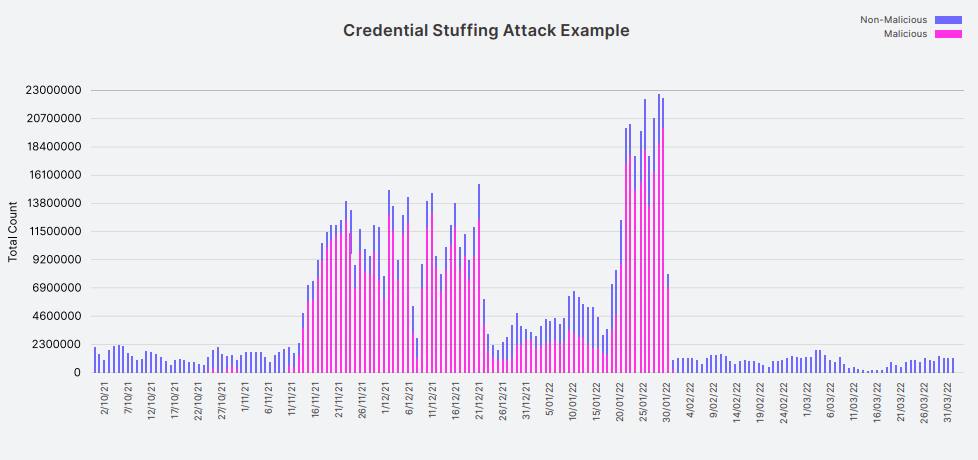
The load diagram is characteristic of how these attacks can be disruptive to online platforms, putting significant strain on their identity management infrastructure, causing latency and degrading the experience for regular users.
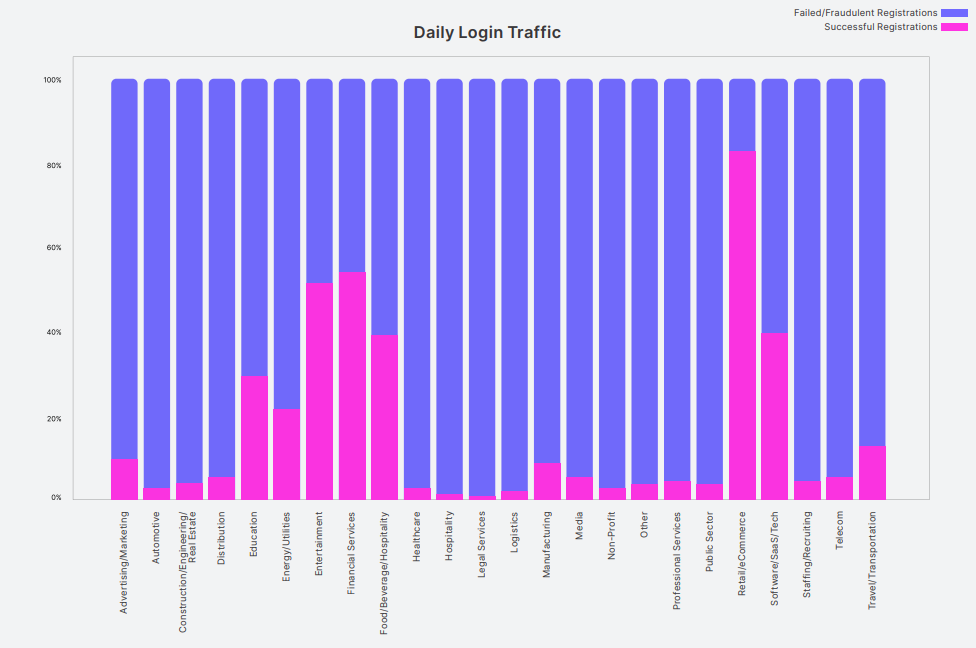
As for the most targeted industries, Okta reports that most attempts were directed at retail/e-commerce. Significant attack volumes were also recorded against education, energy, financial services, and software/SaaS.
A recent example of a credential stuffing attack against an e-commerce platform is that against North Face customers, compromising approximately 200,000 accounts in the brand’s online store.
Protection against credential stuffing attacks is primarily the responsibility of online platforms that must use fingerprint checks, engage in proactive credential verification, use proxy discovery systems, and implement implements “shadow ban” on suspicious accounts.
From a user’s perspective, using multi-factor authentication and setting unique, strong passwords for all your online accounts provides adequate protection against most such threats.
However, as shown by recent MFA Fatigue Attacks, threat actors have found ways to circumvent MFA through social engineering. Therefore, it is important for organizations to properly secure MFA with thresholds for matching numbers and authentication attempts.
[ad_2]
Source link
