[ad_1]

A decryption tool for a modified version of Conti ransomware could help hundreds of victims recover their files for free.
The utility works with data encrypted with a strain of the ransomware that emerged after Conti’s source code leaked last year in March [1, 2].
Hundreds of encrypted victims
Researchers from cybersecurity firm Kaspersky discovered the leak on a forum where threat actors posted a cache of 258 private keys from a modified version of Conti ransomware.
The variant has been used in attacks against various private and public organizations over the past year by a ransomware group that some researchers track as MeowCorp.
ransomware finder Amigo-A told BleepingComputer that the threat actors posted the data on a Russian-speaking forum in February 2022, which contained a link to an archive containing decryption keys, decryption executables, and decryptor source code.
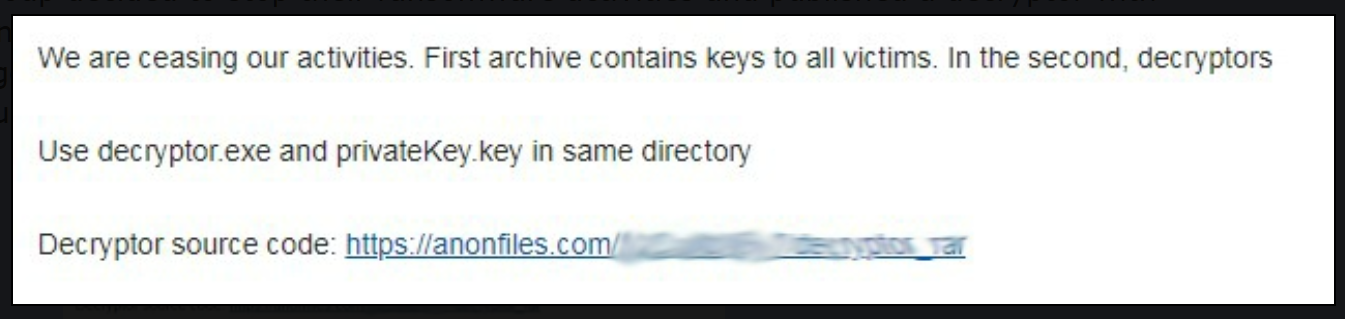
source: Amigo-A
Kaspersky analyzed the keys and found them associated with a Conti variant which they discovered in December 2022. However, the strain had been circulating since at least August.
“Leaked private keys are located in 257 folders (only one of these folders contains two keys)”, Kaspersky said in a press release today.
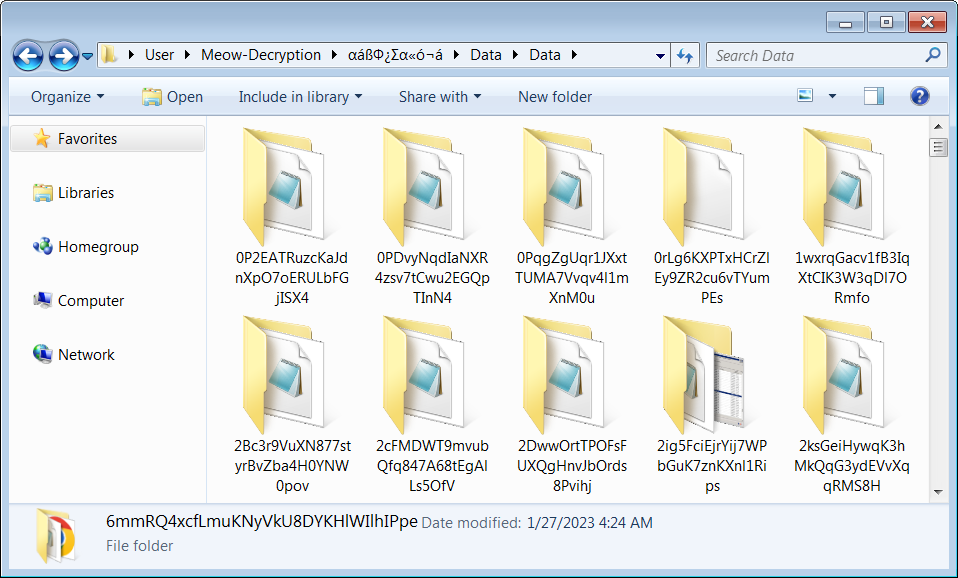
source: BleepingComputer
BleepingComputer learned that the Conti-based cipher used in these attacks specifically targeted Russian organizations.
The researchers add that some of the folders included previously generated decryptors as well as other files, i.e. photos and documents, which were probably used to show victims that the decryption works.
34 of the files contained names of private companies and government agencies, suggesting that the attacker kept separate files for each victim.
Based on this and the number of decryptors available in the leak, Kaspersky says it can be assumed that the modified Conti strain was used to encrypt 257 victims and that 14 of them paid the attackers to recover the data. locked.
Kaspersky has added the decryption code and the 258 private keys to its RakhniDecryptora tool capable of recovering files encrypted by more than two dozen ransomware strains.
According to Kaspersky, the decryptor can recover files encrypted by the modified Conti variant which used the following name pattern and extensions:
.KREMLIN .RUSSIA .PUTIN
The disappearance of Conti ransomware
For approximately three years, the Conti gang ran one of the most active and lucrative ransomware-as-a-service operations, targeting large organizations and demanding large ransoms to decrypt the data they locked.
Considered the successor of Ryuk ransomware, Operation Conti began in December 2019 and, with the help of TrickBot operators, became a dominant threat in July 2020.
The gang wreaked havoc relentlessly for a year and adopted new tactics (e.g. data theft, leak site) to force victims to pay the ransom.
In August 2021, a disgruntled Conti affiliate leaked information on certain members of the group as well as on the gang’s method of attack and training manuals.
The Russian invasion of Ukraine in February last year created more internal friction as key members sided with Russia.
This led a researcher who was spying on the operation to leak thousands of messages exchanged between Conti operators and affiliates.
The researcher’s revenge continued through March by leaking the source code of the ransomware’s encryptor, decryptor, and builder, along with the administrative panels. [1, 2].
The operation was quick to fall apart and in May 2022 Conti team leaders took the infrastructure offline and announced that the brand no longer existed.
Direction Conti in partnership with other gangs in the extortion business and the other members migrated to other ransomware operations.
The US government estimates that Conti was one of the most lucrative ransomware operations, claiming thousands of victims and amassing over $150 million in ransom payments.
The damage done to American businesses determined the US State Department to offer a reward of up to $15 million for information that identified and located Conti officers and affiliates.
[ad_2]
Source link
