[ad_1]

Security researchers have noticed an increase in the number of devices infected with the TrueBot malware downloader created by a Russian-speaking hacking group known as Silence.
The Silence group is known for its major hold-ups against financial institutions and has begun to move away from phishing as the initial vehicle for compromise.
The threat actor is also using a new custom data exfiltration tool called Teleport. Analysis of Silence’s attacks over the past few months revealed that the gang delivered Clop ransomware typically deployed by TA505 hackerswhich are associated with the group FIN11.
Truebot Infections
Silence hackers planted their malware on more than 1,500 systems around the world to harvest shellcode, Cobalt Strike beacons, Grace malware, Teleport exfiltration tool and Clop ransomware.
The new campaigns were analyzed by researchers at Cisco Talos, who observed several new attack vectors in use since August 2022.
In a small number of attacks between August and September, hackers infected systems with Truebot (Silence.Downloader) after exploiting a critical vulnerability in Netwrix Auditor servers tracked as CVE-2022-31199.
In October 2022, the gang switched to using USB drives to infect computers with the Raspberry Robin worm, which often delivered IcedID, Bumblebee, and Truebot payloads.
A Microsoft report in October linked the worm to the distribution of Clop ransomware by a threat actor they track as DEV-0950, whose malicious activity overlaps that of FIN11 and TA505 (known for use Clop in extortion attacks).
Cisco Talos notes that the Truebot gang used Raspberry Robin to infect over 1,000 hosts, including many workstations not accessible on the public web, primarily in Mexico, Brazil, and Pakistan.
In November, hackers targeted Windows servers exposing SMB, RDP, and WinRM services on the public Internet. Researchers have counted more than 500 infections, about 75% of them in the United States.
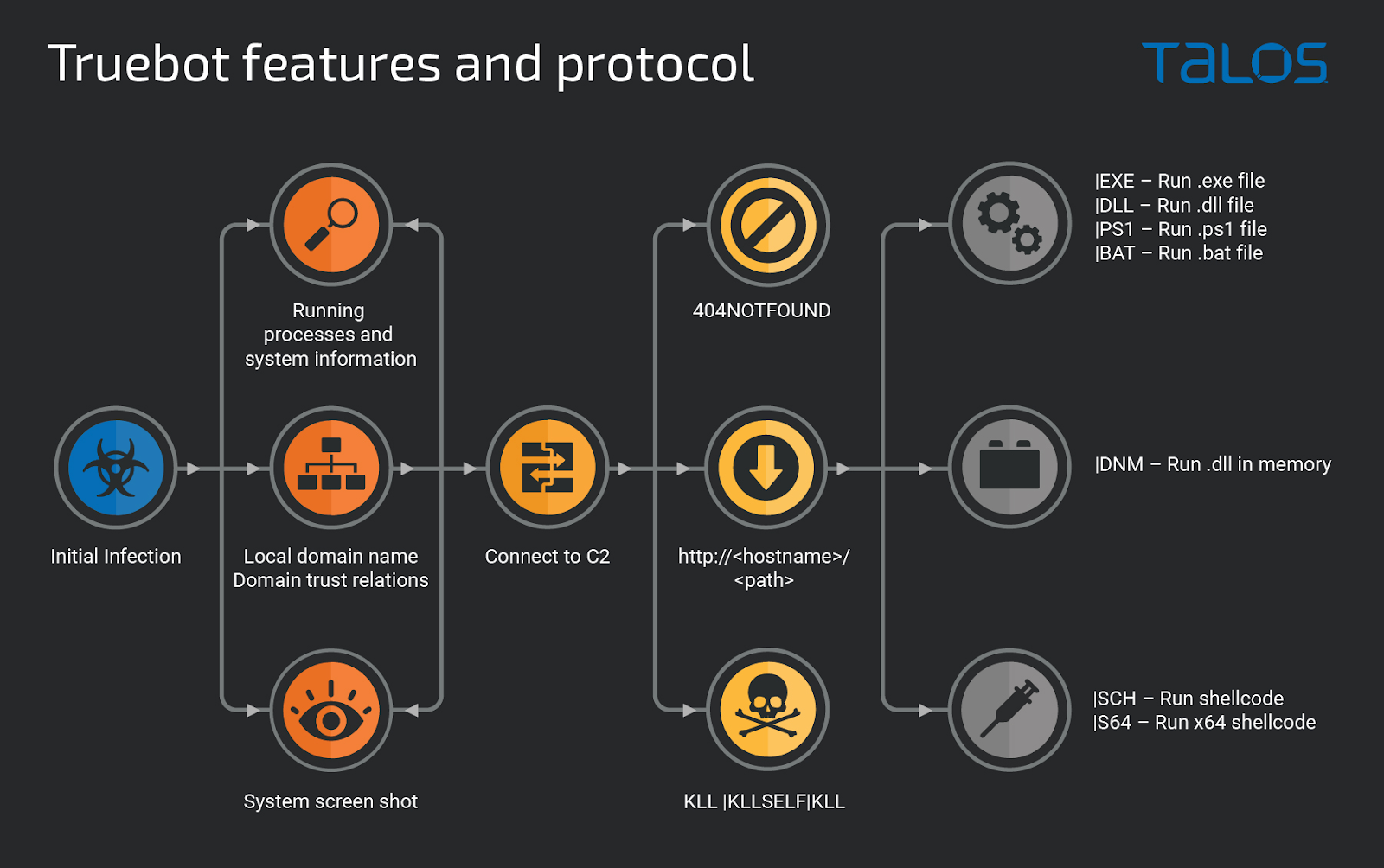
Truebot is a first stage module that can collect basic information and take screenshots. It also exfiltrates trust relationship information from Active Directory that helps the threat actor plan post-infection activity.
The command and control (C2) server can then instruct Truebot to load shellcode or DLLs into memory, run additional modules, uninstall itself, or download DLLs, EXEs, BATs, and PS1s.
New Teleport data exfiltration tool
In the post-compromise phase, hackers use Truebot to drop Cobalt Strike beacons or Grace malware (FlawedGrace, GraceWire), which has been attributed to cybercrime group TA505.
After that, intruders deploy Teleport, which Cisco describes as a new custom tool built in C++ that helps hackers steal data stealthily.
The communication channel between Teleport and the C2 server is encrypted. Operators can limit download speed, filter files by size to steal more, or remove payload. This is all designed to keep a low profile on the victimized machine.
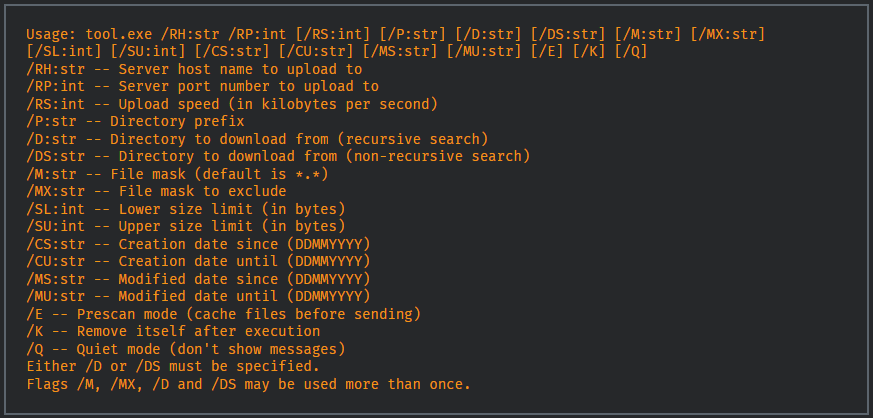
Teleport also offers options to steal files from OneDrive folders, harvest victim’s Outlook emails, or target specific file extensions.
In some cases, attackers deploy Clop ransomware after moving sideways to as many systems as possible with the help of Cobalt Strike.
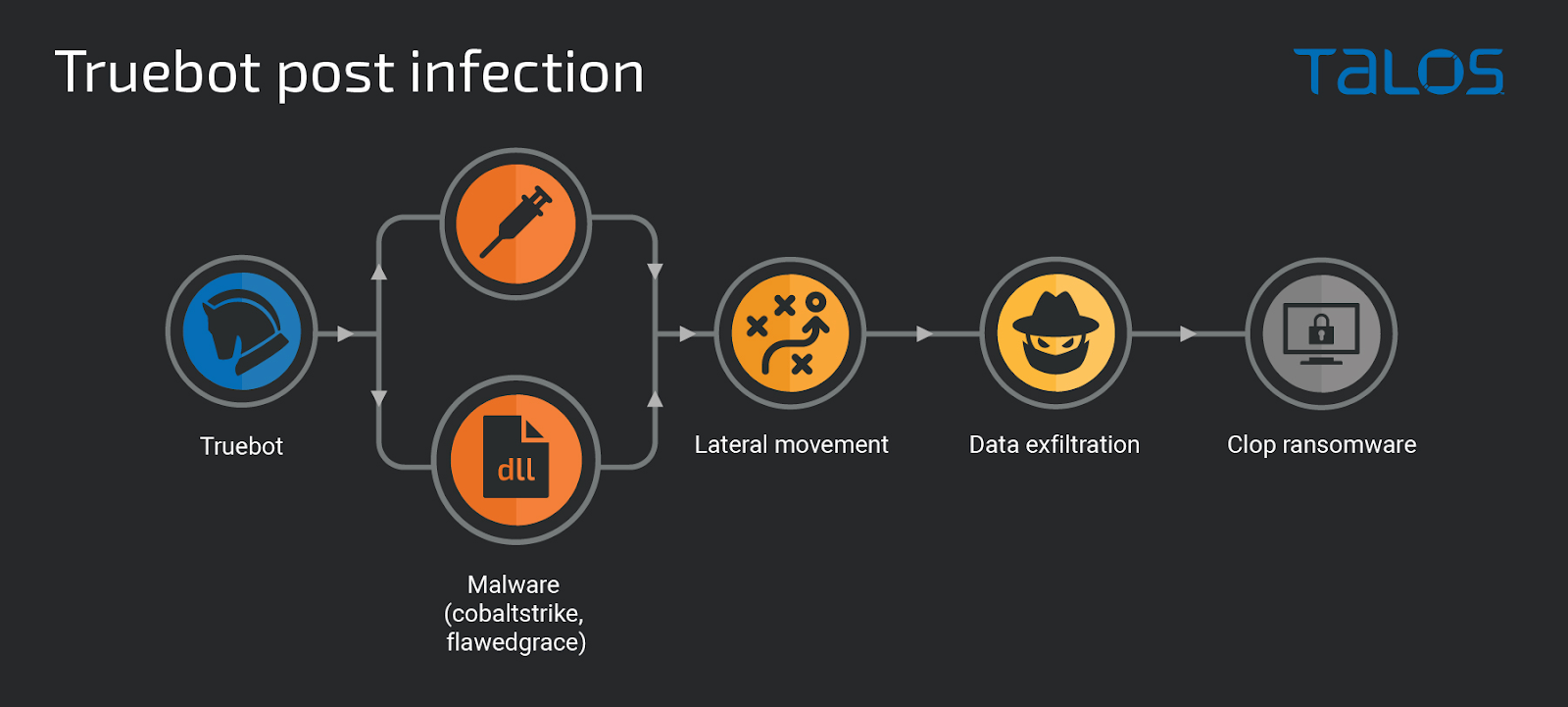
“During the exploration and lateral movement phases, the attackers browsed the main server and desktop file systems, connected to SQL databases, and collected data which was exfiltrated using the ‘Teleport tool to a server controlled by the attacker’, Cisco Talos researchers explain.
“Once enough data was collected, the attackers created scheduled tasks on a large number of systems to simultaneously start Clop ransomware execution and encrypt as much data as possible.”
Silence gang activity
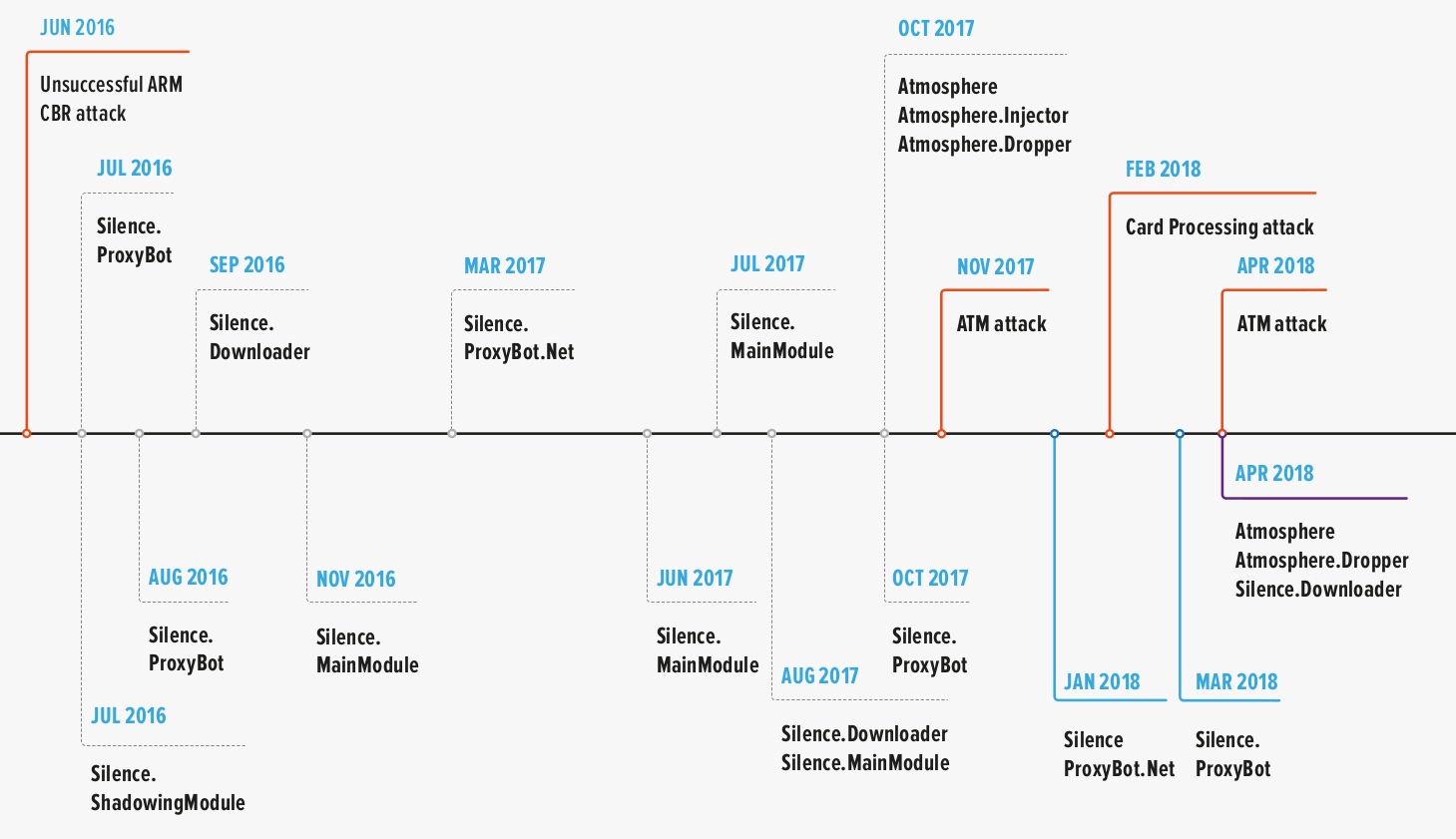
Researchers in a cybersecurity company Group-IB follows Silence/Truebot activity since 2016 when hackers sneaked into a bank but failed to steal money due to a problem with a payment order.
The attacker hit the same target again and started monitoring the banking operator’s activity by taking screenshots and streaming videos from the infected system to find out how the money transfer procedure works. silver.
In 2017, they pulled off their first successful robbery, according to Group-IB’s knowledge, attacking ATM systems and stealing over $100,000 in one night.
Silence continued its attacks and in three years between 2016 and 2019 they stole at least $4.2 million from banks in the former Soviet Union, Europe, Latin America and Asia,
source: IB-Group
Group-IB researchers describe Silence hackers as highly skilled, able to reverse engineer malware to modify it for their own purposes or adapt at the level of assembler instructions an exploit used by the state-owned group Fancy Bear. They are also able to develop their own tools.
Initially, the attacker only targeted organizations in Russia, but Silence has expanded its reach globally over the past few years.
[ad_2]
Source link
