[ad_1]

The Clop ransomware gang is expected to make between $75 million and $100 million by extorting victims of their massive MOVEit data theft campaign.
In a new report released today, Coveware explains that the number of victims paying ransoms has fallen to an all-time high of 34%, forcing ransomware gangs to change strategy to make their attacks more profitable.
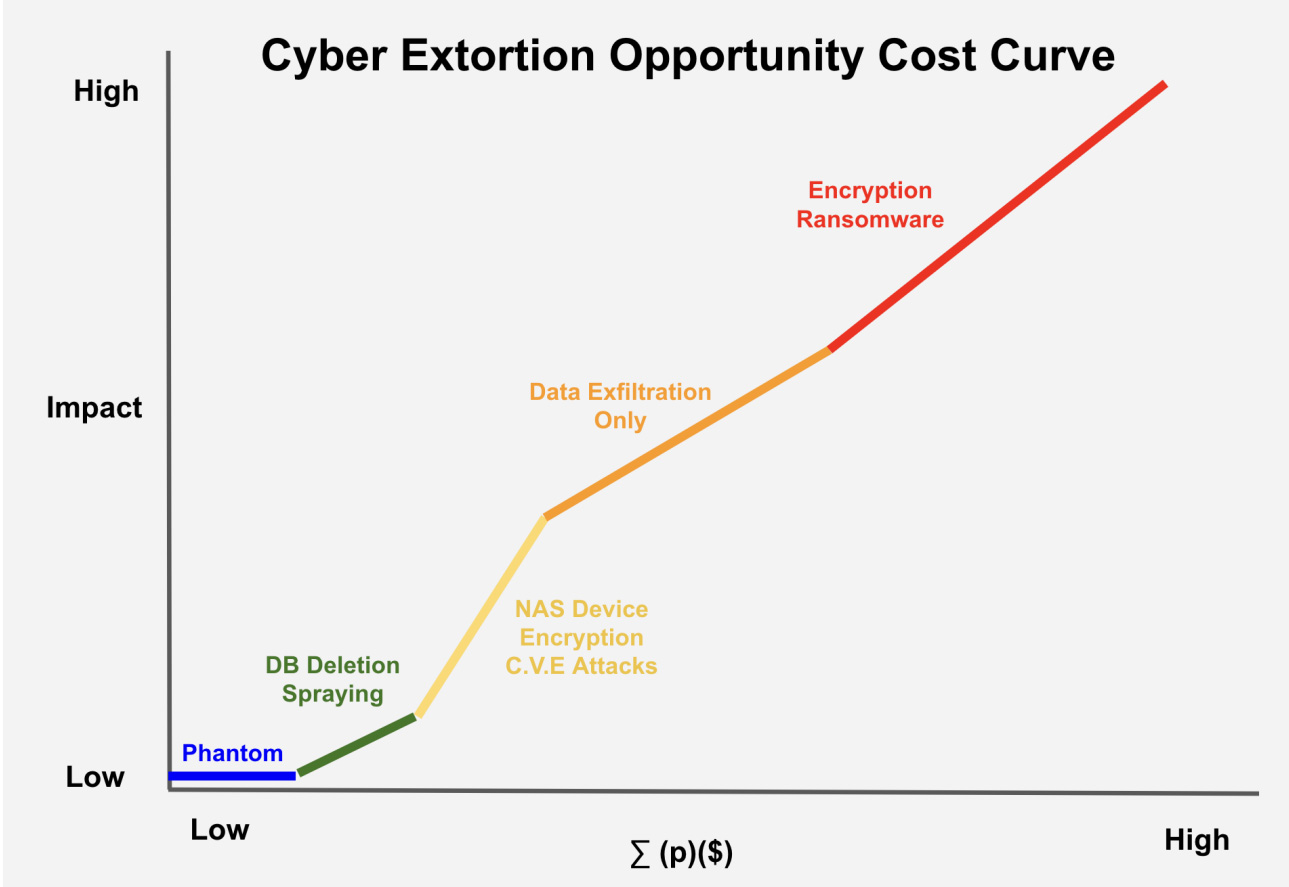
Coveware explains that different extortion attacks have varying opportunity costs reflected by the amount of effort and investment required to carry out an attack versus the expected ransom demand.
The relationship between the impact on a victim and the threat actor’s costs (time, effort and investment) to carry out the attack is illustrated in the table below. The vertical axis represents victim impact, while the horizontal axis depicts threat actor costs.
Source: BleepingComputer
The graph shows that extortion attacks with the lowest complexity and automation have the least impact on victims and cost for attackers.
This is reflected in ransom demands, with ghost attacks (social engineering), erasing the database with ransoms and NAS encryption attacks like Qlockertypically having low ransom demands due to automation and lack of attack complexity.
For attacks like these, ransom demands typically range from a few hundred dollars to thousands of dollars, with threat actors hoping that a large volume of payouts will offset low ransom prices.
However, more complicated and time-consuming attacks with greater impact generate much larger ransom demands, typically millions.
Clop changes tactics as payouts drop
On May 27, the Clop ransomware gang launched widespread data theft attacks by exploiting a zero-day vulnerability in MOVEit Transfer secure file transfer platform.
These attacks are expected to affect hundreds of businesses worldwide, many of which have already notified their affected customers in the past two months.
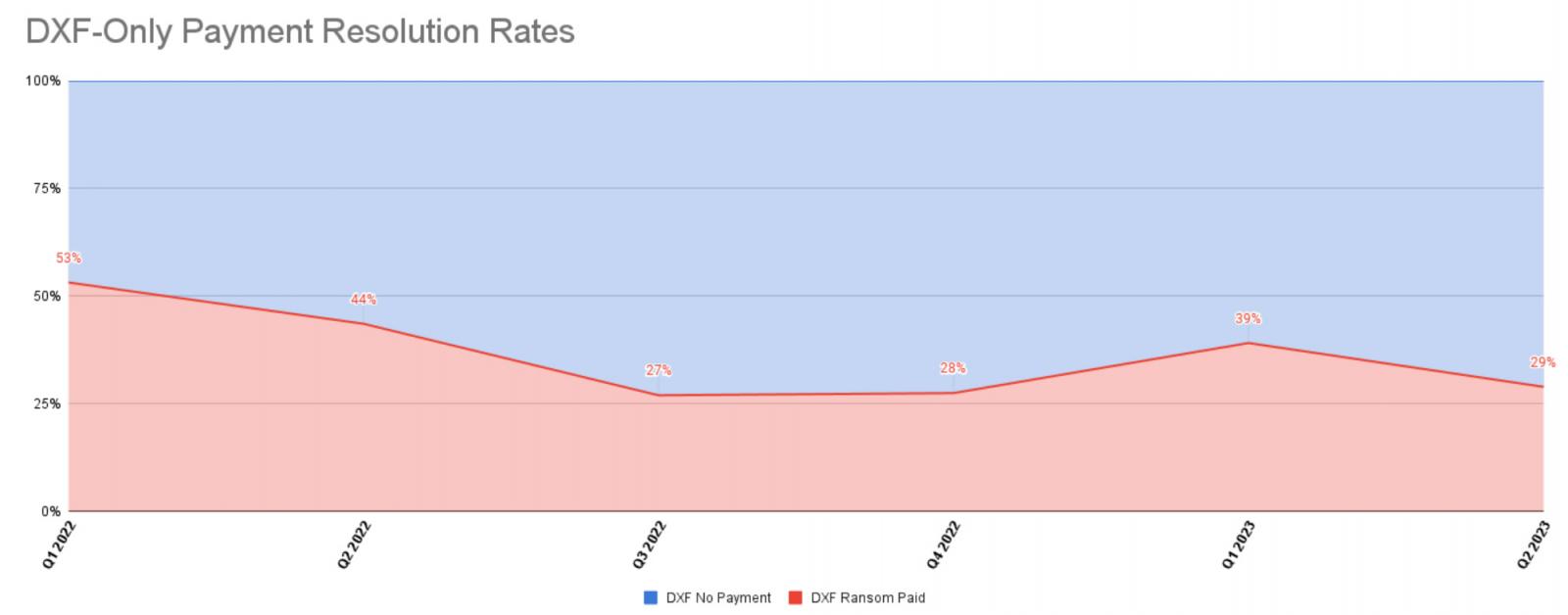
However, Coveware says extortion attacks focused solely on data theft have decreased payouts over time, with victims preferring to disclose attacks and issue data breach notifications rather than paying threat actors.
“DXF-only attacks do not cause significant business disruptions like encryption impact, but can harm brand and create notification requirements,” Coveware’s report explains.
“The probability of a ransom being paid is less than 50%, but the ($) of a ransom demand for DXF attacks alone is relatively high.”
Source: Coverware
Coveware says Clop has changed its extortion strategy to demanding much larger ransom demands than previously seen in data exfiltration attacks, hoping that a few large payouts will overcome the overall drop.
According to Coveware’s estimate, only a few victims of MOVEit data theft are likely to pay. Nonetheless, Clop is still expected to amass an impressive $75-100 million from these payouts alone, given the substantial ransom demands.
“It is likely that the CloP group could earn between $75 million and $100 million from the MOVEit campaign alone, this sum coming from a small handful of victims who succumbed to very high payments,” says Coveware.
“This is a dangerous and staggering amount of money for a relatively small group to possess.”
Coveware CEO Bill Siegel told BleepingComputer that Clop’s success in these attacks is significantly greater than their recent GoAnywhere data theft attackswhere threat actors only claimed 130 lives and received only a few ransom payments.
Siegel thinks Clop’s 2021 Accellion FTA data theft attacks succeeded because the victims were not as well educated on the pros and cons of paying to prevent data leakage. Additionally, the media has paid much more attention to individual violations in 2021, with the media now becoming impervious to these types of attacks.
“Today, victims are much better informed about the pros and cons of these situations (the cons very clearly outweigh the pros in most situations),” Siegel told BleepingComputer.
“So while Accellion was a pretty big financial hit because a higher percentage of victims were paid out of a fairly small pool of victims, GoAnywhere seemed like an almost total flop on another small pool of victims.”
“MOVEit had at least 10 times more direct victims than these two attacks, so CloP was able to focus only on the largest and most likely to consider paying, even with over 90% of victims not even caring to engage in negotiation, let alone pay.”
Ransomware affiliates turn to new operations
In addition to the evolution of data theft attack tactics, Coveware has also seen a change when it comes to ransomware encryption attacks.
Coveware claims there has been a dramatic reduction in Ransomware-as-a-Service operations targeting small businesses, as obtaining ransom payments has become much more difficult.
As a result, smaller ransomware operations such as Dharma and Phobos have seen an almost 37% decrease in attacks in 2023.
Instead, Coveware has seen a shift among more affiliates within these groups, as they transition to the new 8base ransomware operation which uses the Phobos cipher to target businesses in larger scale attacks.
A recent VMware report linked 8base to RansomHouse, a ransomware operation known to target large organizations and allow affiliates to demand larger ransoms.
[ad_2]
Source link
