[ad_1]

Security researchers have observed a hacking group targeting companies in the materials research industry with a unique toolset that includes a custom remote access Trojan (RAT) called Atharvan.
The threat actor is being tracked as Clasiopa by Symantec, a Broadcom company, whose analysts have found a clue pointing to an Indian threat actor. However, the attribution remains unclear as there is little evidence to support a theory.
Clasiopa attack details
Although there is no solid data to point to a particular initial infection vector, Symantec researchers have found clues to suggest that Clasiopa uses brute force to gain access to public servers.
Symantec Reports that attackers take various actions after the compromise, including:
- check IP address of hacked system
- disabling endpoint protection products by stopping their services
- deploy malware capable of searching for specific files and exfiltrating them as ZIP archives
- clear Sysmon logs and event logs to erase traces of malicious activity
- creating a scheduled task (“network service”) to list filenames
Symantec’s investigation revealed that in addition to its backdoor, Clasiopa also uses legitimate software such as Agile DGS and Agile FD, signed with old certificates.
The hackers relied on two backdoors for their attack: the custom Atharvan and the open-source Lilith RAT. The latter can be used to execute commands, execute PowerShell scripts and manipulate processes on the hacked system.
Clasiopa also used a custom proxy tool and “Thumbsender”, a utility that lists files on the host and saves them locally to a database that can later be exfiltrated to a specified IP address.
Atharvan Abilities
Atharvan is the most interesting of the tools used by Clasiopa because it is a custom backdoor not seen in any other attack in the wild.
When running, it creates a mutex to prevent multiple processes from running, then contacts a hard-coded command and control (C2) address in an unusual location, the Amazon Web Services infrastructure in Seoul, Korea from South.
Below is an example of the backdoor communicating with the C2 server, formatted as HTTP POST requests to a supposedly legitimate host, Microsoft’s update server.
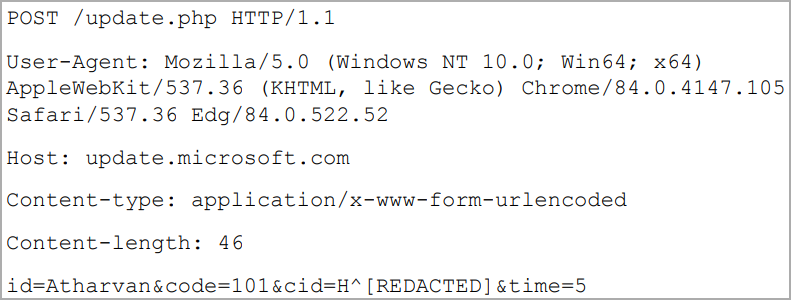
Another unusual feature is that it can be configured for scheduled communication with the C2 and can even be configured to attempt connections during specific days of the week or month.
In terms of capabilities, Atharvan downloads files to the compromised computer, runs executables, executes commands, and returns their output.
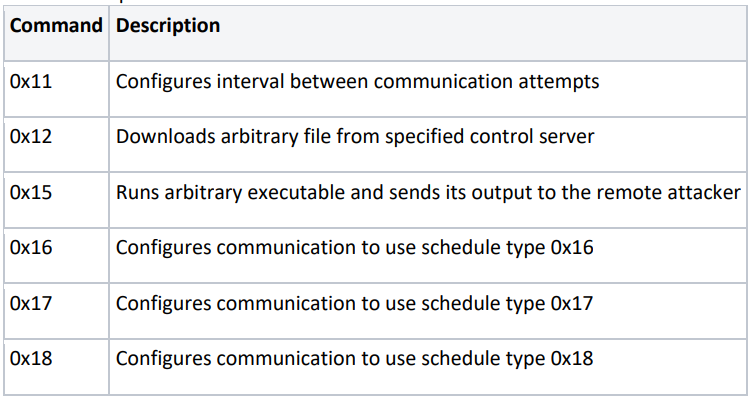
The researchers note that Atharvan’s communications with C2 are protected using a simple algorithm to XOR each byte of the plaintext with the value “2” to produce the ciphertext. This does not achieve a strong encryption result, but can still help malware evade some network traffic monitoring tools.

The clue pointing to a threat actor in India is a Hindi mutex that researchers discovered in the custom backdoor: “SAPTARISHI-ATHARVAN-101”, Atharvan referring to a legendary priest in Vedic mythology, the son of Brahmā , the creator. Another clue is a password used by the attacker for a ZIP archive, which was “iloveindea1998 ^_^”.
Both clues, however, could very well be a false flag planted for misattribution.
The Atharvan backdoor is largely undetected at this time. There is only one sample available on the VirusTotal scanning platform and it is marked as a threat by only two antivirus engines.
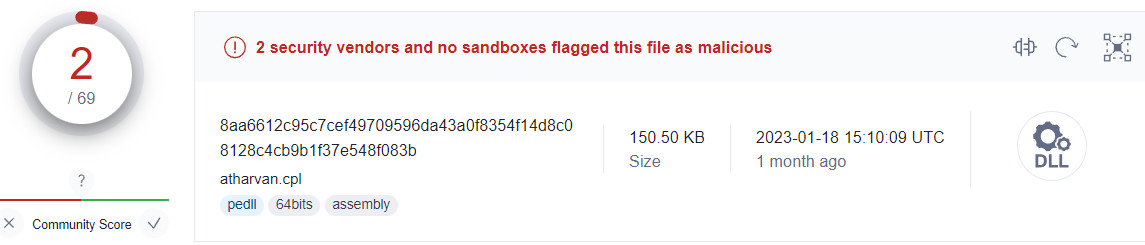
Clasiopa’s goals remain unclear at this time, but cyber espionage appears to be the motivation behind the attacks. Researchers say the threat actor targeted victims in Asia.
Symantec’s report provides a set of hashes for malware discovered in malicious campaigns attributed to Clasiopa.
Indicators of compromise include the hashes for the two backdoors (Atharvan and Lilith) as well as the tools used by the malicious actor during the attacks.
[ad_2]
Source link
