[ad_1]

Today, CISA ordered federal agencies to patch recently patched security vulnerabilities exploited as zero days to deploy triangulation spyware to iPhones via no-click iMessage exploits.
The warning comes after Kaspersky released a report detailing a Malicious triangulation component used in a campaign, it follows as “Operation Triangulation.”
Kaspersky says it found the spyware on iPhones belonging to employees of its Moscow office and other countries. The attacks began in 2019 and are still ongoing, according to the company, and they use zero-click iMessage exploits that exploit now-patched zero-day iOS bugs.
Russian intelligence agency FSB also claimed that Apple collaborated with the NSA to create a backdoor, facilitating the infiltration of iPhones into Russia. The FSB also said it found thousands of infected iPhones belonging to Russian government officials and embassy staff in Israel, China and NATO member countries.
“We have never worked with a government to insert a backdoor into an Apple product and we never will,” an Apple spokesperson told BleepingComputer.
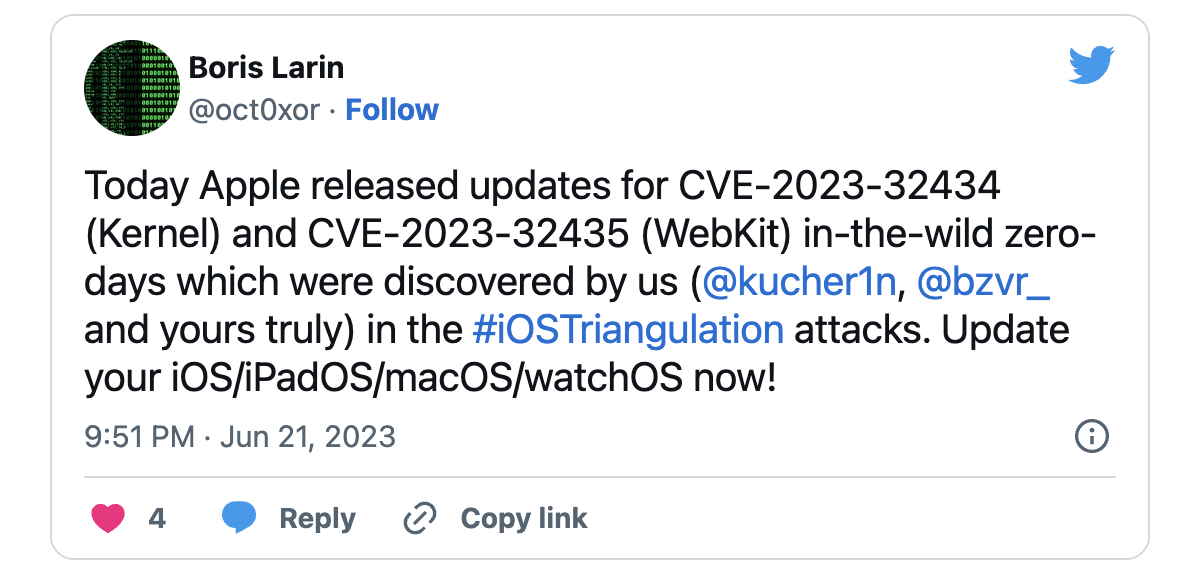
“Apple is aware of a report that this issue may have been actively exploited against versions of iOS released prior to iOS 15.7,” the company said. said wednesday when describing the two Kernel and WebKit vulnerabilities (CVE-2023-32434 And CVE-2023-32435) exploited in the attacks.
The company also patched a zero-day WebKit (CVE-2023-32439) this week that may allow attackers to obtain execution of arbitrary code on unpatched devices. This was also labeled by CISA Today as an actively exploited flaw.
The list of affected devices is long, as day zero affects both older and newer models, and includes:
- iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, iPad mini 5th generation and later
- iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation) and iPod touch (7th generation)
- Mac running macOS Big Sur, Monterey, and Ventura
- Apple Watch Series 4 and later, Apple Watch Series 3, Series 4, Series 5, Series 6, Series 7 and SE
On Thursday, Apple sent another round of threat notifications alerting customers that they were the target of state-sponsored attacks, a day after patching zero-days exploited to deploy the Triangulation spyware. However, it is not clear which incidents these new warnings are related to, according to CNN reporter Chris Bing.
Federal agencies ordered to patch by July 14
Another vulnerability that CISA added to its Known Exploited Vulnerabilities (KEV) list today is a critical pre-authentication command injection bug (CVE-2023-27992) that can allow unauthenticated attackers to execute operating system commands on unpatched, internet-facing network-attached storage (NAS) devices.
Zyxel warned customers Tuesday to secure their NAS devices “for optimal protection,” weeks after Mirai-based botnets targeted Zyxel firewalls and VPN products in a massive wave of attacks.
CISA also included a VMware ESXi vulnerability (CVE-2023-20867) in its KEV catalog. This bug was abused by a China-backed hacking group (UNC3886) to thwart Windows and Linux virtual machines during data theft attacks.
US Federal Civilian Executive Branch (FCEB) agencies must patch all security vulnerabilities added to CISA’s KEV catalog within a specified timeframe, according to a Binding Operational Directive (BOD 22-01) released in November 2022.
Following the latest update, federal agencies have been tasked with securing vulnerable devices against the vulnerabilities included today by June 14, 2023.
Although BOD 22-01 is primarily focused on US federal agencies, private companies are strongly recommended to also prioritize the vulnerabilities described in CISA’s KEV list, which includes bugs known to be exploited in attacks.
[ad_2]
Source link