[ad_1]

Hackers are deploying new Linux malware variants in cyber espionage attacks, such as a new PingPull variant and a previously undocumented backdoor tracked as “Sword2033”.
PingPull is a RAT (Remote Access Trojan) first documented by Unit 42 last summer in espionage attacks carried out by the Chinese state-sponsored group Gallium, also known as Alloy Taurus. The attacks targeted government and financial organizations in Australia, Russia, Belgium, Malaysia, Vietnam and the Philippines.
Unit 42 continued to monitor these spy campaigns and today’s reports that the Chinese threat actor is using new malware variants against targets in South Africa and Nepal.
PingPull on Linux
The Linux variant of PingPull is an ELF file that only 3 of 62 antivirus vendors currently report as malicious.
Unit 42 was able to determine that this was a port of known Windows malware by noticing similarities in the HTTP communication structure, POST parameters, AES key, and commands it receives from the C2 server of the menacing actor.
The commands that the C2 sends to the malware are indicated by a single uppercase character in the HTTP parameter, and the payload sends the results back to the server via a base64-encoded request.
The parameters and corresponding commands are:
- A – Get the current directory
- B – List Folder
- C – Read text file
- D – Write a text file
- E – Delete a file or folder
- F – Read binary file, convert to hex
- G – Write binary file, convert to hex
- H – Copy file or folder
- I – Rename a file
- J – Create directory
- K – Timestamp file with a timestamp specified in the format “%04d-%d-%d %d:%d:%d”
- M – Execute Command
Unit 42 comments that the command handlers used in PingPull match those seen in another malware named ‘China chopper,’ a web shell widely used in attacks against Microsoft Exchange servers.
Details of Sword2023
Unit 42 also found a new ELF backdoor that communicated with the same command and control (C2) server as PingPull.
It is a simpler tool with more basic functions such as downloading files to the hacked system, exfiltrating files and running a command with “; echo
The echo command adds random data to the execution log, possibly to make parsing more difficult or obfuscate its activity.
Unit 42 discovered a second Sword2023 sample associated with a different C2 address posing as the South African military.
The same sample was tied to a Soft Ether VPN address, a product Gallium is known to use in its operations.
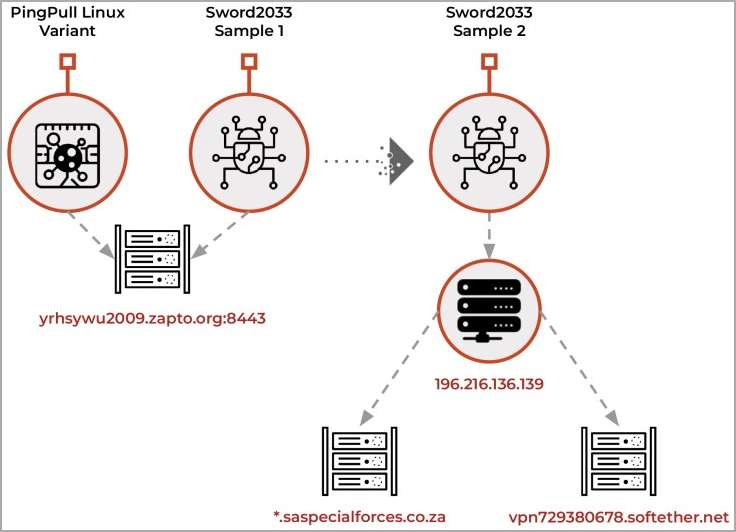
The cybersecurity firm clarifies that this is not a random choice, as in February 2023, South Africa participated in joint military exercises with Russia and China.
In conclusion, Gallium continues to refine its arsenal and expand its range of targets using the new Linux variants of PingPull and the newly discovered Sword2023 backdoor.
Organizations must adopt a comprehensive security strategy to effectively counter this sophisticated threat rather than relying solely on static detection methods.
[ad_2]
Source link
