[ad_1]

Security researchers have observed a new campaign they attribute to the Charming Kitten APT group where hackers used the new NokNok malware that targets macOS systems.
The campaign began in May and relies on a different infection chain than previously seen, with LNK files deploying the payloads instead of the typical malicious Word documents seen in the group’s past attacks.
Charming Kitten is also known as APT42 or Phosphorus and has launched at least 30 operations in 14 countries since 2015, according to according to Mandiant.
Google linked the threat actor to the Iranian state, specifically the Islamic Revolutionary Guard Corps (IRGC).
In September 2022, the US government succeeded in identify and invoice members of the threatening group.
Proofpoint reports that the threat actor has now abandoned macro-based infection methods involving interleaved Word documents and instead deploys LNK files to load their payloads.
Regarding the phishing lures and social engineering methods seen in the campaign, hackers posed as US nuclear experts and approached targets with an offer to review projects on political topics foreign.
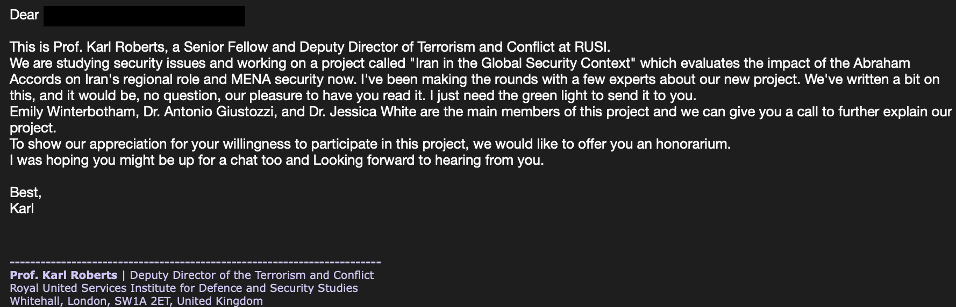
In many cases, attackers insert other characters into the conversation to add a sense of legitimacy and establish rapport with the target.
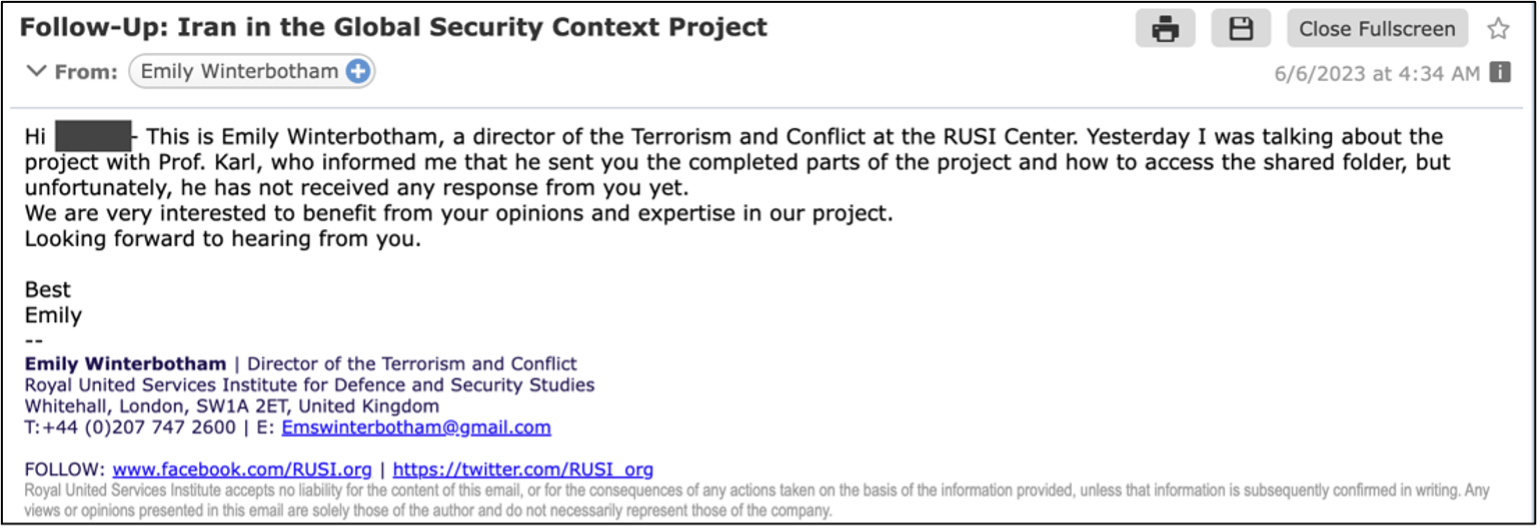
The impersonation or assumption of a fake personality of Charming Kitten in phishing attacks has been documentedas well as its use of ‘puppets socks‘ to create realistic conversation threads.
Attacks on Windows
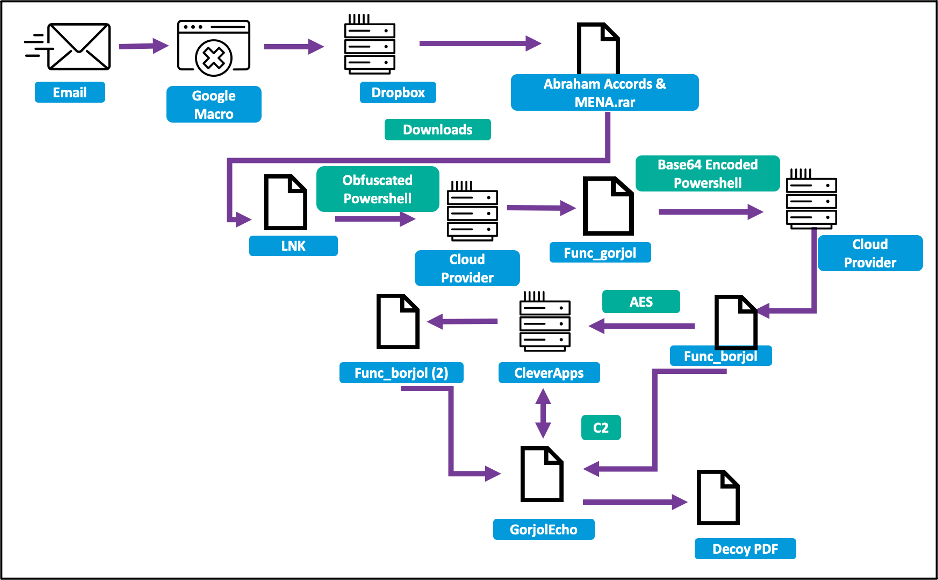
After gaining the target’s trust, Charming Kitten sends a malicious link containing a Google Script macro, redirecting the victim to a Dropbox URL.
This external source hosts a password-protected RAR archive with a malware dropper that leverages PowerShell code and an LNK file to stage malware from a cloud hosting provider.
The final payload is GorjolEcho, a simple backdoor that accepts and executes commands from its remote operators.
To avoid raising suspicion, GorjolEcho will open a PDF with a topic related to the discussion the attackers had with the target previously.
Attacks on macOS
If the victim is using macOS, which hackers usually realize after failing to infect them with the Windows payload, they send a new link to “library-store[.]camdvr[.]org” which hosts a ZIP file posing as a RUSI (Royal United Services Institute) VPN application.
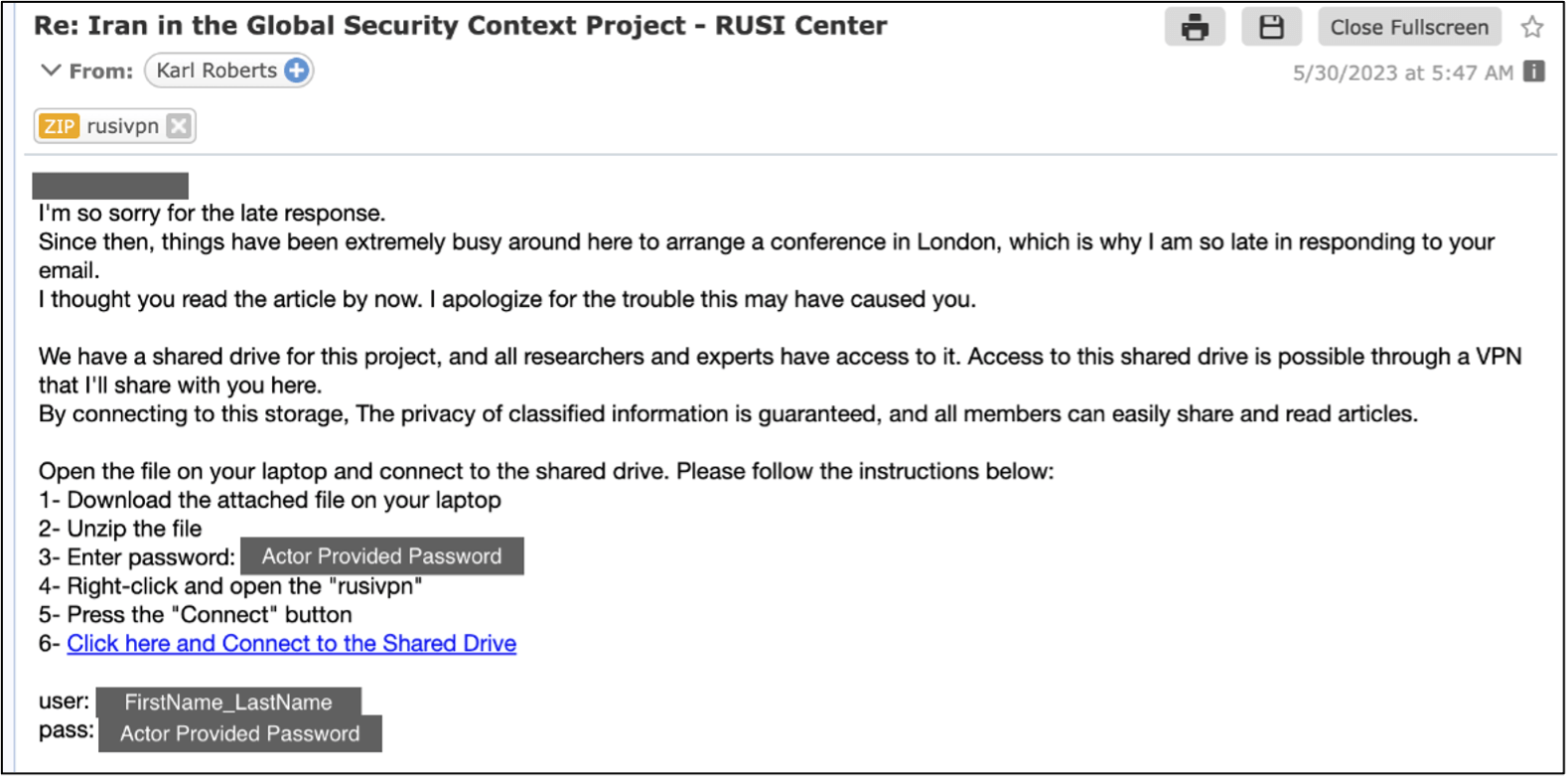
Upon execution of the Apple script file in the archive, a curl command retrieves the NokNok payload and establishes a backdoor on the victim’s system.
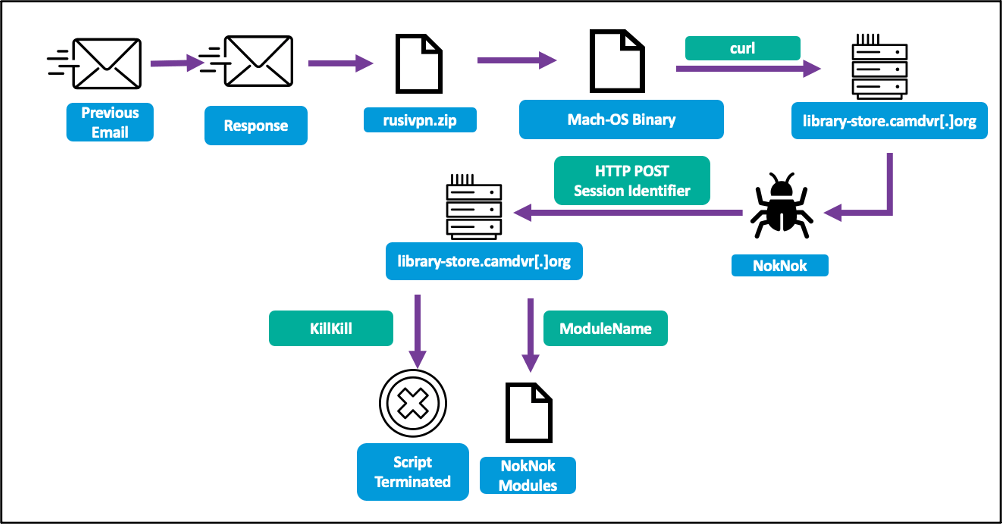
NokNok generates a system identifier, then uses four bash script modules to set persistence, establish communication with the command and control (C2) server, and then begin exfiltrating data to it.
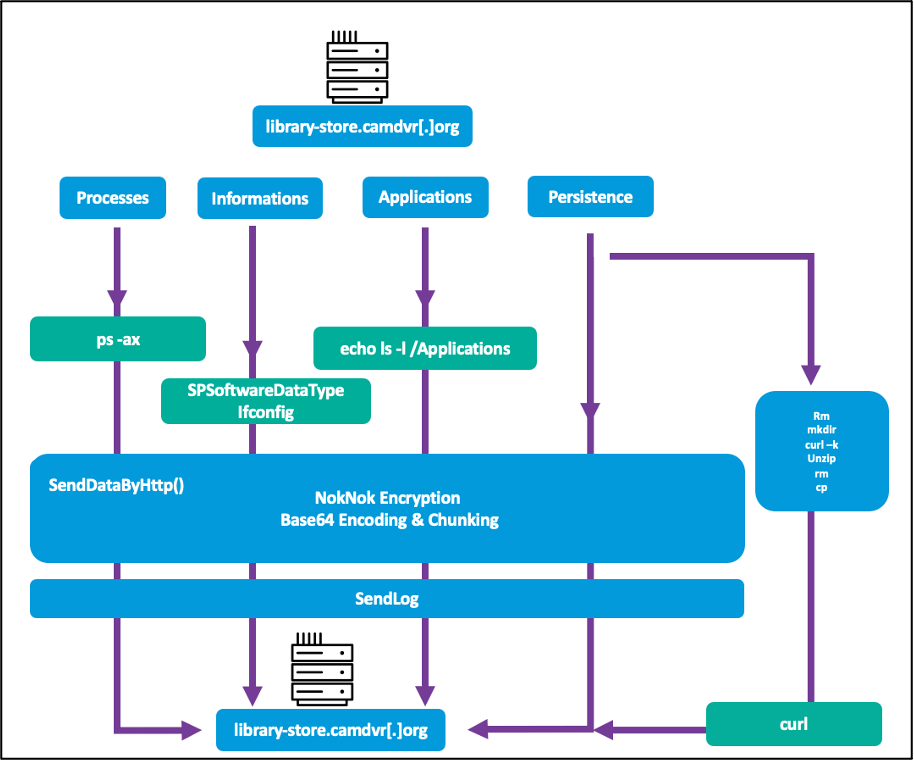
NokNok malware gathers system information which includes operating system version, running processes and installed applications.
NokNok encrypts all collected data, encodes it in base64 format and exfiltrates it.
Proofpoint also mentions that NokNok might offer more specific features related to spying through other invisible modules.
The suspicion is based on code similarities to GhostEcho, previously analyzed by Check Point.
This backdoor had modules that allowed taking screenshots, executing commands and cleaning the infection trail. It is likely that NokNok also has these functions.
Overall, this campaign shows that Charming Kitten has a high degree of adaptability, is able to target macOS systems if necessary, and highlights the growing threat of sophisticated malware campaigns to macOS users.
[ad_2]
Source link
