[ad_1]

Researchers from Korea University School of Cybersecurity in Seoul presented a new secret channel attack named CASPER that can leak data from isolated computers to a nearby smartphone at a rate of 20 bps.
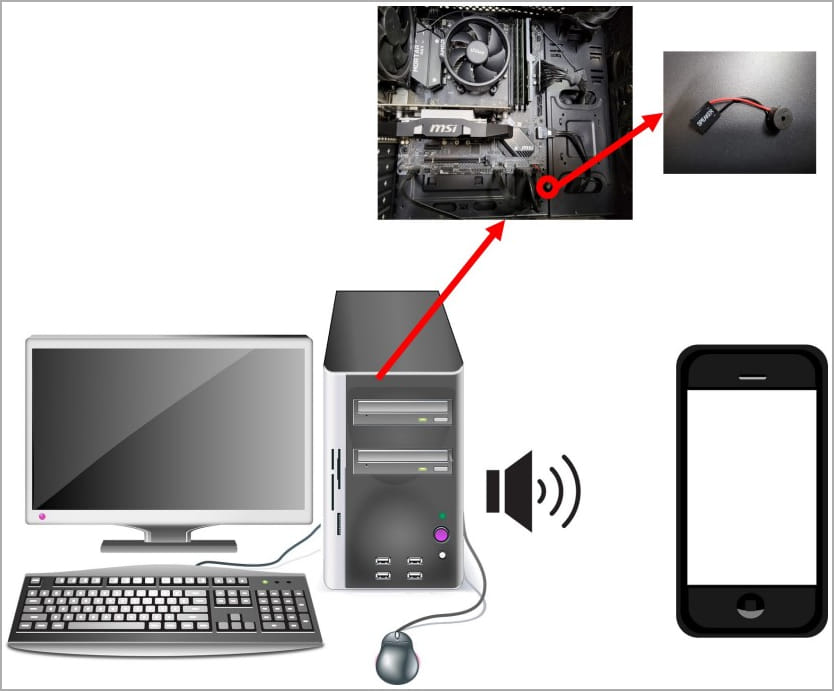
The CASPER attack exploits the internal speakers inside the target computer as a data transmission channel to transmit high frequency sound that the human ear cannot hear and transmit binary or Morse code to a microphone up to 1.5m away.
The receiving microphone can be in a smartphone recording sound in the attacker’s pocket or a laptop in the same room.
Researchers have previously developed similar attacks using external speakers. However, off-grid and off-grid systems used in critical environments, such as government networks, energy infrastructure, and weapons control systems, are unlikely to have external speakers.
On the other hand, internal speakers that provide audio feedback, such as startup beeps, are still considered necessary, so they are usually present, making them better candidates.
Infect the target
As is the case with almost all secret channel attacks targeting computers isolated from the network, a dishonest employee or stealthy intruder with physical access to the target must first infect them with malware.
While this scenario may seem impractical or even far-fetched, there have been several instances of successful attacks in the past, with notable examples like the Stuxnet worm, which targeted Iran’s uranium enrichment facility. in Natanz, the Agent.BTZ malware. which infected a US military base, and the Remsec modular backdoor, which secretly harvested information from isolated government networks for more than five years.
The malware can autonomously enumerate the target’s file system, locate files or file types that match a hard-coded list, and attempt to exfiltrate them.
More realistically, it can perform keylogging, which is more suitable for such a slow data transmission rate.
The malware will encode the data to be exfiltrated from the target in binary or Morse code and transmit it through the internal speaker using frequency modulation, obtaining an imperceptible ultrasound in the range between 17 kHz and 20 kHz.
The results
The researchers experimented with the described model using a Linux-based computer (Ubuntu 20.04) as the target and a Samsung Galaxy Z Flip 3 as the receiver, running a basic recording application with a sampling rate of up to 20 kHz. .
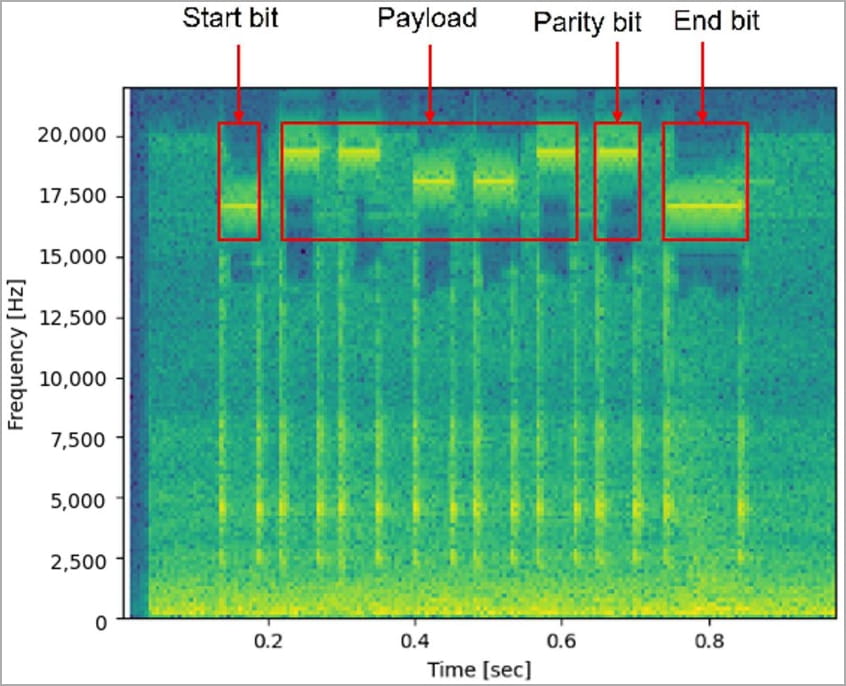
In the Morse code experiment, the researchers set the length per bit to 100 ms and used 18 kHz for the dots and 19 kHz for the dash. The smartphone was located 50 cm away and was able to decode the “secret” word sent.
In the binary data experiment, the length per bit was set to 50 ms, transferring zeros at 18 kHz and 1s at 19 kHz. A 50 ms start/stop bit was also used at 17 kHz to indicate the start of a new message.
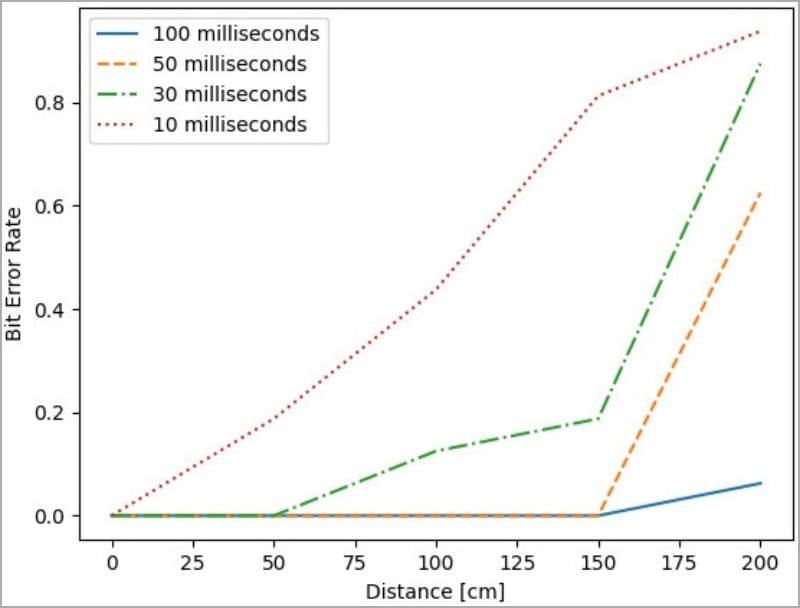
Based on the tests performed, the maximum distance from the receiver is 1.5 meters (4.9 feet), using a length per bit of 100 ms.
The overall results of the experiment, however, show that the bit length affects the bit error rate and that a maximum reliable transmission bit rate of 20 bps is achievable when the bit length is 50 ms.
At this data transfer rate, the malware could transmit a typical 8-character password in about 3 seconds and a 2048-bit RSA key in 100 seconds.
Anything above that, like a small 10KB file, for example, would take over an hour to exfiltrate from the vacuum system, even if conditions were ideal and no interruptions does not occur during transmission.
A solution to the slow data rate would be to vary the frequency band for multiple simultaneous transmissions; however, the internal speakers can only produce sound in one frequency band, so attack is virtually limited.
The researchers shared ways to defend against the CASPER attack, the easiest being to remove the internal speaker from critical computers.
If this is not possible, defenders could implement a high-pass filter to keep all generated frequencies within the audible sound spectrum, blocking ultrasonic transmissions.
If you are interested in other secret channel attacks against isolated systems, check out COVID bitwhich uses the power supply to generate electromagnetic waves that carry data.
Other examples of similar attacks are ETHERLEDwhich relies on the target network card’s LED lights to transmit Morse code signals, and a named Satanwhich uses SATA cables as wireless antennas.
[ad_2]
Source link
