[ad_1]

British outsourcing service provider Capita announced today that a cyber attack prevented access to its internal Microsoft Office 365 applications on Friday.
Capita, based in London, employs 50,000 specialists and offers a wide range of services to clients in finance, IT, healthcare, education and government.
Its customers include critical infrastructure organizations in the UK such as the National Health Service (NHS), the British Army and the Department for Work and Pensions, as well as leading companies such as O2, Vodafone and the Royal Bank of Scotland.
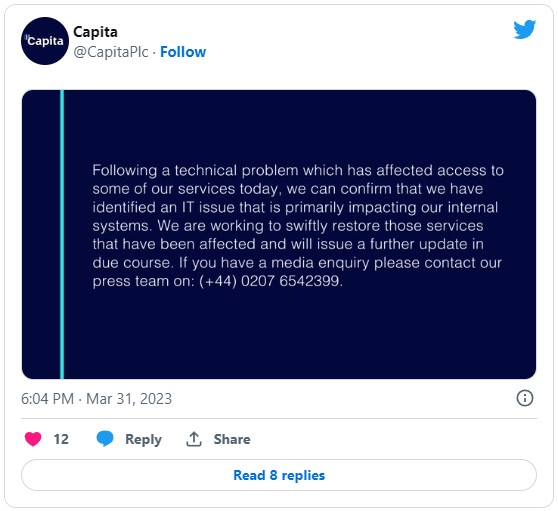
The cyber incident prompted Capita on March 31 to announce a computer issue that impacted its internal systems. However, the company did not provide any further details on the causes of the incident.
In a short press release today, Capita acknowledges that the outage was caused by a cyberattack. The incident happened at 4am on Friday and was discovered three hours later when staff tried to log into the system.
The company said its immediate response succeeded in isolating and containing the security issue.
The disclosure informs that the attack affected limited parts of the network and that the investigation found no indication that data belonging to its customers, suppliers or employees was exposed during the intrusion.
Capita says the disruption only affected some services provided to individual customers, while most of its customer base was not negatively impacted. The company did not provide any details about the parties affected by the cyberattack.
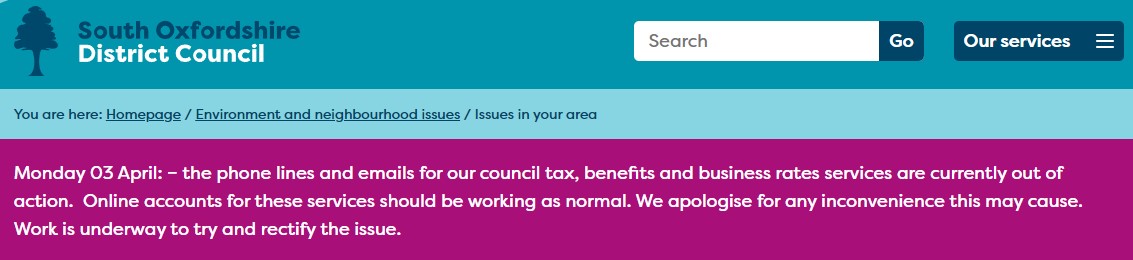
However, there are indications that the boroughs of Barnet, Dagenham, Barking and South Oxfordshire Council – all Capita customers – have been affected as they posted notices on their websites that phone servers and messaging were not available.
Currently, Capita is working to fully restore access to Microsoft Office 365 and other customer services and reports progress in this endeavor.
BleepingComputer contacted Capita to learn more about the cyberattack and its impact, but received no response.
[ad_2]
Source link