[ad_1]
Hackers exploited critical remote code execution vulnerability in Realtek Jungle SDK 134 million attacks attempting to infect smart devices in the second half of 2022.
Exploited by multiple threat actors, the vulnerability is identified as CVE-2021-35394 and is associated with a severity score of 9.8 out of 10.
Between August and October of last year, Palo Alto Networks sensors observed significant exploit activity for this security issue, accounting for over 40% of the total number of incidents.
High levels of exploitation
Starting from September 2022, a new sizable botnet malware named “RedGoBot” appeared in the wild targeting IoT devices vulnerable to CVE-2021-35394.
Researchers from Unit 42, Palo Alto Network’s threat intelligence team, noticed that exploitation of the flaw continued throughout December.
Three different payloads were delivered as a result of these attacks:
- a script that executes a shell command on the target server to download malware
- an injected command that writes a binary payload to a file and executes it
- an injected command that restarts the server
Most of these attacks come from botnet malware families like Mirai, Gafgyt, Mozi and their derivatives. In April 2022, the Fodcha botnet was spotted exploiting CVE-2021-35394 for Distributed Denial of Service (DDoS) operations.
The RedGoBot also used the vulnerability for DDoS purposes in attacks in September. The botnet can perform DDoS attacks on HTTP, ICMP, TCP, UDP, VSE, and OpenVPN protocols and supports various flooding methods.
Unit 42 recorded activity exploiting CVE-2021-35394 worldwide, but nearly half of the attacks originated from the United States.
However, the use of VPNs and proxies can obscure the real source, as threat actors prefer to use US-based IP addresses to evade blocklists.
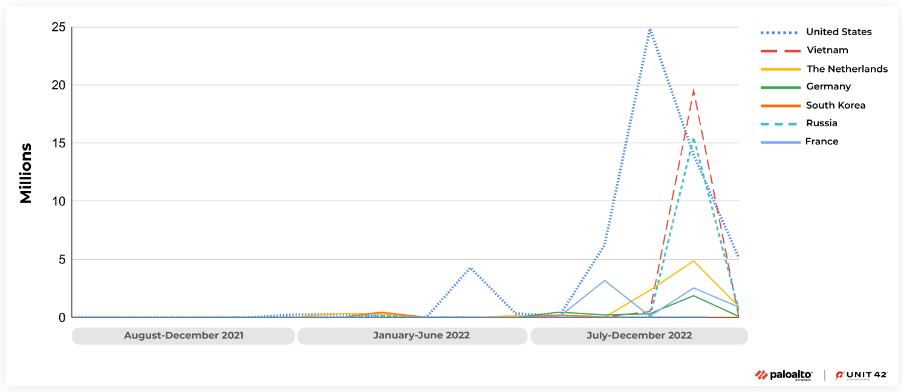
“From August 2021 to December 2022, we observed 134 million total exploit attempts targeting CVE-2021-35394, with 97% of these attacks occurring after the start of August 2022,” reads the Unit 42 report.
Realtek SDK Flaw Details
CVE-2021-35394 is a critical vulnerability (CVSS v3:9.8) in Realtek Jungle SDK version 2.x through 3.4.14B, caused by multiple memory corruption flaws that allow unauthenticated remote attackers to perform arbitrary command injection.
Realtek fixed the flaw on August 15, 2021as well as other critical-severity flaws such as CVE-2021-35395, which was widely targeted by botnets that incorporated Exploits simple days after disclosureand as recently as last december.
Realtek chipsets are ubiquitous in the IoT world, and even as the Taiwanese chipmaker pushes security updates to quickly fix issues in its products, supply chain complexities delay their delivery to users. final.
Additionally, users often overlook firmware updates, even when available from their device vendors, and many treat IoT devices with an “install and forget” mindset.
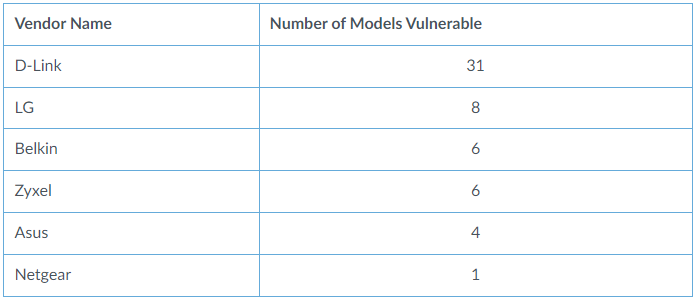
An increase in exploitation of CVE-2021-35394 almost more than a year after Realtek released security patches indicates that remediation efforts are lagging behind and the responsibility is shared between vendors and the final user.
Some of the vulnerable devices may no longer be supported. In some cases, vendors may have released an update with a fix, but users failed to install it. Users should check if their devices are affected and if there are security patches available that fix CVE-2021-35394.
If your device has been infected before, it is recommended to perform a factory reset, set a strong administrator password, and then apply all available firmware updates.
Exploitation of CVE-2021-35394 is expected to remain at elevated levels in the first half of 2023 due to the complexity of supply chain patches that are causing massive delays in handling the security issue.
[ad_2]
Source link
