[ad_1]

Google has announced new cellular security features for its upcoming Android 14, expected later this month, that aim to protect business data and communications.
Android 14 will allow consumers and enterprises to turn off support for 2G on their devices or a managed device fleet and disable support for null-cipher (unencrypted) cellular connectivity at the modem level.
“Android is the first mobile operating system to introduce advanced cellular security mitigations for both consumers and enterprises,” reads Google’s announcement
“Android 14 introduces support for IT administrators to disable 2G support in their managed device fleet [and] also introduces a feature that disables support for null-ciphered cellular connectivity.”
Enterprise Stingray protection
Google’s announcement highlights the risks of false base stations and “Stingray” attacks that can intercept users’ data, voice, and SMS by eavesdropping on network traffic.
Stingrays are cell-site simulators that mimic cell towers to trick in-range devices to connect to them. This allows for intercepting sensitive personal data such as call metadata, SMS and voice call content, data usage and browsing history, and device IMSI.
Stingray attacks have been largely mitigated in 4G. However, since downgrading connections to 2G remains possible, rogue cell stations can still perform these powerful man-in-the-middle attacks.
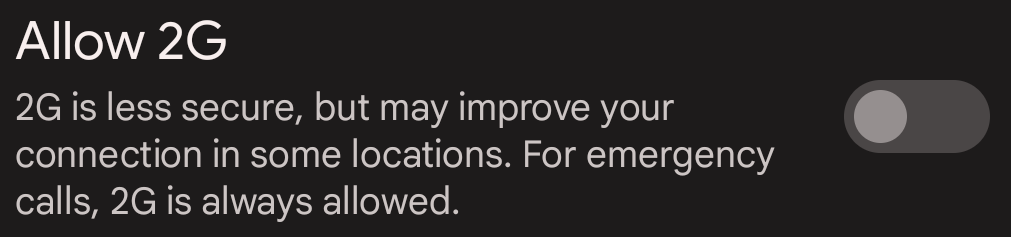
Google first offered the option to turn off 2G connectivity on Android 12 by going through ‘Settings → Network & Internet → SIMs → Allow 2G’.
In Android 13, that option is to be found on ‘Settings → Network & Internet → SIMs → [select SIM] → Allow 2G.’
Source: BleepingComputer
Starting in Android 14, those managing device fleets, such as government agencies, enterprise entities, or other organizations, can restrict 2G connectivity downgrades on all devices under their control.
This option is added on top of over 200 controls available in Android Enterprise, including the ability to disable WiFi, Bluetooth, and data signaling over USB.
Stingray attacks have become more common over the past couple of years, with law enforcement and surveillance firms utilizing them to spy on cell phones, so this feature comes as a welcome addition to enterprise security.
Blocking unencrypted networks
While all IP-based user traffic on Android is end-to-end encrypted, ensuring that any interceptions won’t result in data breaches, Google warns that certain communication types, such as circuit-switched voice calls and SMS messages, can still be exposed on cellular networks.
The exposed data is typically protected by the cellular link layer cipher, which the users have no control or visibility over, so its strength and reliability are doubtful.
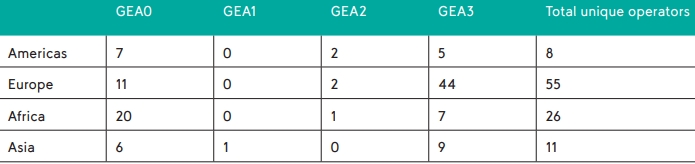
Moreover, recent reports have shown that null ciphers (no encryption) are not uncommon in commercial networks, exposing the mentioned data in cleartext and easily readable form to those who can intercept it.
Source: umlaut.com
To mitigate this risk, Android 14 introduces a feature that allows users to turn off support for null-cipher connections at the modem level for devices that adopt the latest radio hardware abstraction layer (HAL).
Like in the 2G disabling feature, emergency calls can still downgrade to null-cipher connections to avoid jeopardizing users’ safety.
[ad_2]
Source link
