[ad_1]

How much does it cost to buy hacked domain administrator access to a Fortune 500 U.S.chemical manufacturer? More than a cup of coffee but less than a high end mountain bike.
Data breaches and ransomware attacks don’t happen in a vacuum. Instead they are supported by a complex ecosystem of cybercriminals, each fulfilling a specific part of a sophisticated supply chain. This post will examine the advent of initial access brokers and their broader role within the cybercrime ecosystem.
Initial access brokers (IAB) are cybercriminals that focus on gaining privileged IT access to corporate environments, which they then auction off on specialized dark web forums.
We wanted to better understand how IABs operate, so we did the only natural thing and spent weeks painstakingly translating posts from Russian into English to conduct an in-depth analysis on the corporate access economy.
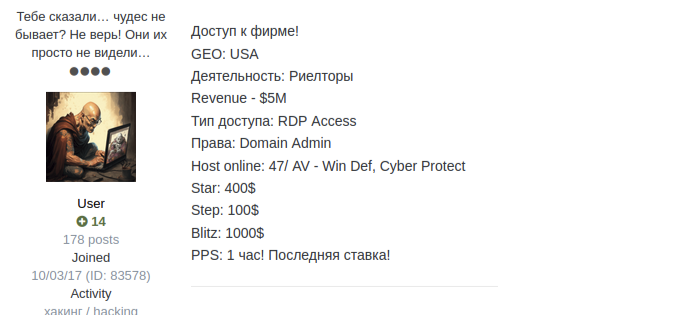
The Anatomy of an Initial Access Broker Post
Many IAB posts follow an extremely similar format, creating a consistent set of features that we can measure to better understand the IAB economy.
Source: Flare
- Access Type/Тип доступа: Describes the type of access obtained, most commonly RDP or VPN access.
- Activity/Деятельность: Describes the industry or activity of the victim company. Finance, Retail, and Manufacturing are the three most common targets.
- Rights/Права: Describes the level of privileges obtained.
- Revenue: Describes the revenue of the victim company, often obtained from U.S. based data providers publicly available online.
- Host Online: Often describes the number of hosts from the victim and sometimes includes antivirus and security systems in place.
- Start: The starting price of the auction.
- Step: The bid increments.
- Blitz: The buy it now price.
Now that we understand the basic structure of an IAB post, we can further explore our three months of data.
Access to corporate IT environments is stunningly cheap; the average price to purchase access to a corporate IT environment across all samples in our data set was $4,699.31. However, a few significant results skewed the price, so when we removed the outliers, the average price was $1,328.23.
The vast majority of IAB posts were within a narrow band with blitz prices between $1,000 and $3,000 for corporate access.
However, occasionally an extremely “high-value” listing is published with access to a uniquely valuable environment. This can lead to prices in the tens of thousands of dollars, with some listings fetching more than $100,000.
Key Takeaway: Access to compromised corporate IT environments is not expensive. Threat actors can simply purchase the level of access needed to cause a major incident for a few thousand dollars.
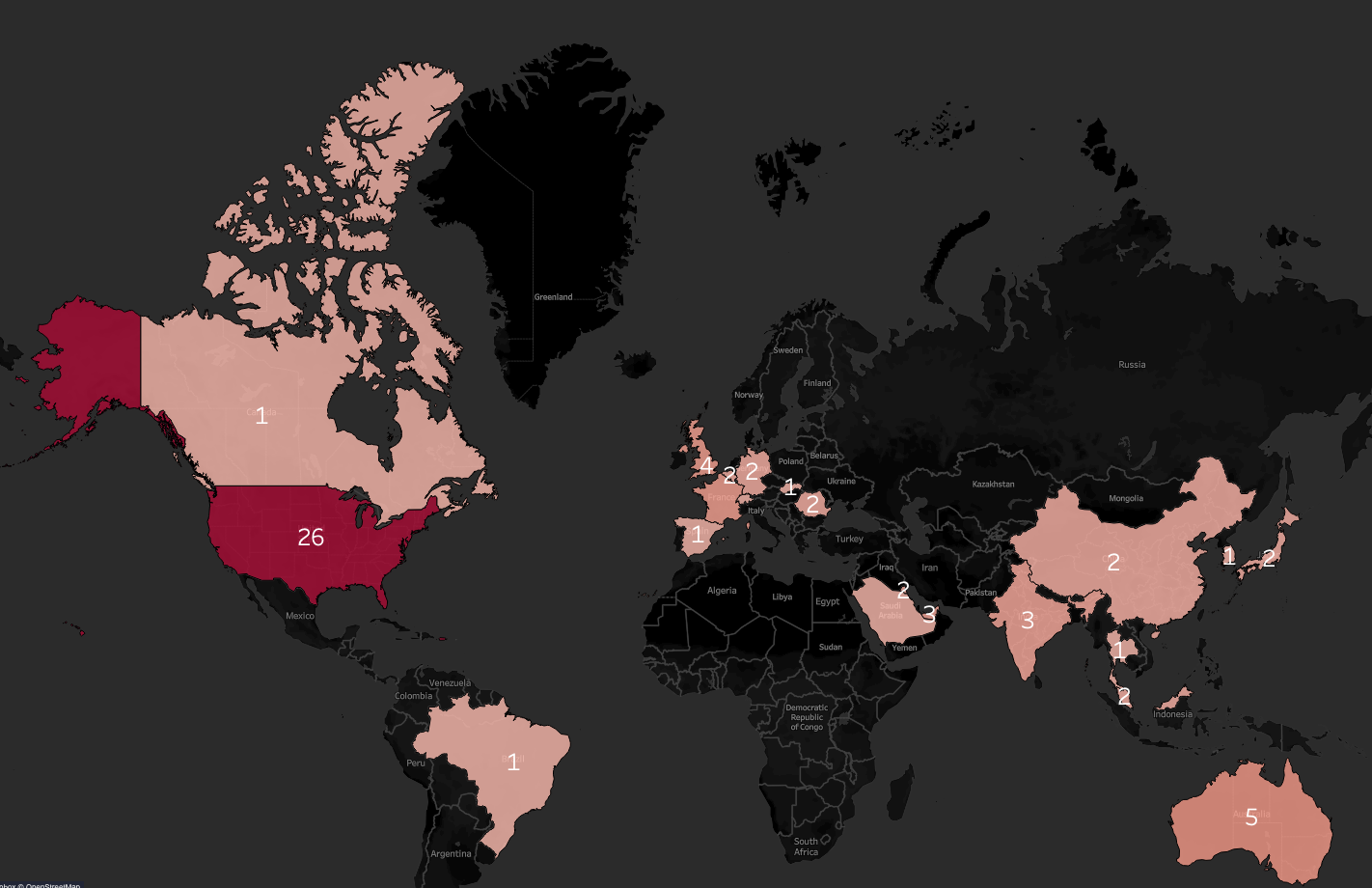
Initial Access Brokers and Geography
We also found that a significant plurality of posts sold access to victims located in the United States, followed by Australia and the United Kingdom, indicating a strong bias towards attacking English-speaking countries.
Source: Flare
While it is unsurprising that the United States is one of the most targeted countries, the sheer amount of victims in the U.S. was striking. More than 36% of posts we analyzed listed a victim located in the United States.
Key Takeaway: Most initial access broker posts on the forum Exploit sell access to U.S., UK, and Australian companies.
Ransomware and Clues from Initial Access Broker Posts
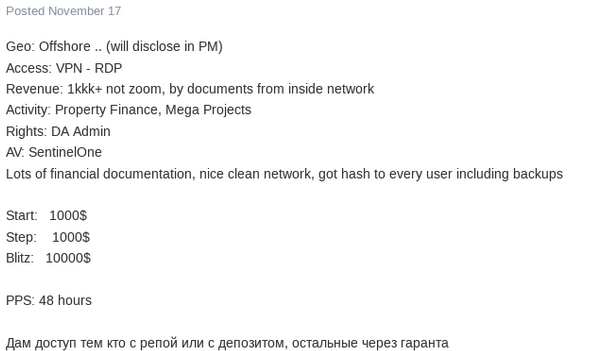
So what are threat actors using access gained from IABs for? Their posts can give us a hint. The most common type of access sold was access to Remote Desktop Protocol (RDP) with administrator privileges, a key vector for ransomware attacks.
Interestingly, some auctions actually called out that the victim organization lacked a backup and recovery solution, or that the IAB had access to the backup system as well. This is likely a key indicator that the seller expects the access to be used for ransomware.
Source: Flare
In the few posts in which we found specifically listed access to backup and recovery systems, blitz prices were significantly higher than those without.
Key Takeaway: IAB auctions are likely a key source of corporate IT access for ransomware groups and affiliates.
Takeaways for Security Teams
Initial access brokers are a significant threat for corporate information security teams. IABs have direct financial incentive to compromise devices, networks, and services in order to resell it on dedicated dark web marketplaces and forums. At Flare we recommend the following:
- Establish robust monitoring capabilities for major dark web cybercrime forums and marketplaces such as BreachForums, Exploit, XSS, and Russian Market.
- Monitor IAB forums for indications that your organization could be compromised, or that one of your third-parties may be compromised.
- Monitor for stealer logs that may contain corporate credentials and active session cookies. Flare’s research has found hundreds of thousands of stealer logs being distributed on Telegram, Russian Market, and Genesis Market containing access to corporate SaaS applications.
Monitoring the Cybercrime Ecosystem with Flare
Flare monitors illicit forums and marketplaces to detect any IAB activities concerning our customers.
Flare’s easy-to-use SaaS platform automates detecting stealer logs across the clear & dark web and illicit Telegram channels.
Sign up for a free trial to learn more about how Flare can boost your security program’s cybercrime monitoring capabilities in 30 minutes.
Sponsored and written by Flare
[ad_2]
Source link
