[ad_1]

A new APT hacking group dubbed Lancefly is using custom backdoor malware “Merdoor” to target government, aviation and telecom organizations in South and Southeast Asia.
Symantec Threat Labs today revealed that Lancefly has been deploying the stealthy Merdoor backdoor in highly targeted attacks since 2018 to establish persistence, execute commands, and perform keystroke logging on corporate networks.
“Lancefly’s custom malware, which we’ve dubbed Merdoor, is a powerful backdoor that appears to have been around since 2018,” reveals the new Symantec report.
“Symantec researchers observed it being used in some activities in 2020 and 2021, as well as in this more recent campaign, which continued through the first quarter of 2023. The motivation behind these two campaigns is believed to be intelligence gathering.”
Lancefly is believed to focus on cyber espionage, aiming to gather intelligence from its victims’ networks over long periods of time.
A wide chain of attack
Symantec did not discover the initial infection vector used by Lancefly. However, he found evidence that the threat group has used phishing emails, brute forcing SSH credentials and exploiting vulnerabilities in public servers for unauthorized access over the years.
Once the attackers establish a presence on the target’s system, they inject the Merdoor backdoor via DLL sideloading into “perfhost.exe” or “svchost.exe”, two legitimate Windows processes that help the malware to escape detection.
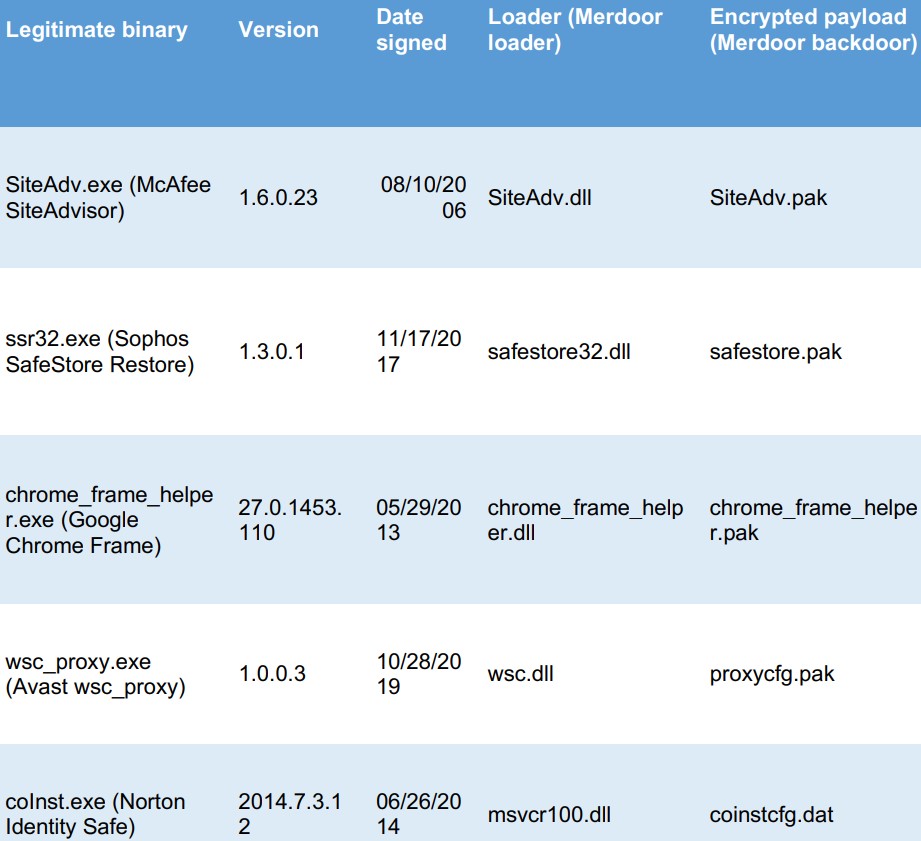
Merdoor helps Lancefly maintain its access and hold over the victim’s system, installing itself as a service that persists between reboots.
Merdoor then establishes communications with the C2 server using one of several supported communication protocols (HTTP, HTTPS, DNS, UDP, and TCP) and waits for instructions.
Besides supporting data exchange with C2 server, Merdoor can also accept commands by listening to local ports; however, Symantec analysts did not provide any specific examples.
The backdoor also logs user keystrokes to capture potentially valuable information such as usernames, passwords, or other secrets.
Lancefly has also been observed using the “Atexec” feature of Impacket to immediately run a scheduled task on a remote machine via SMB. Threat actors are believed to use this feature to laterally spread to other devices on the network or delete output files created from other commands.
Attackers attempt to steal credentials by dumping LSASS process memory or stealing SAM and SYSTEM registry hives.
Finally, Lancefly encrypts the stolen files using a cloaked version of the WinRAR archiving tool, then exfiltrates the data, most likely using Merdoor.
ZXShell Rootkit
The use of a newer, lighter, and more feature-rich version of the ZXShell rootkit has also been observed in Lancefly attacks.
The rootkit loader, “FormDII.dll”, exports functions that can be used to drop payloads matching the host’s system architecture, read and execute shellcode from a file, kill processes, etc
The rootkit also uses an install and update utility that shares common code with the Merdoor loader, indicating that Lancefly uses a shared codebase for its tools.
ZXShell’s installer feature supports building, hacking and launching services, modifying the registry and compressing a copy of its own executable for evasion and resilience.
Links to China
The ZXShell rootkit loosely connects Lancefly with other Chinese APT groups that have used the tool in attacks, including APT17 and APT41.
However, the link is weak because the source code of the rootkit has been publicly available for several years.
Lancefly’s name “formdll.dll” for the rootkit loader was previously reported in a campaign by APT27, aka “Budworm”.
However, it is unclear whether this was a deliberate choice to mislead analysts and make attribution more difficult.
An element that further supports the hypothesis that Lancefly is of Chinese origin is the observed use of the PlugX And ShadowPad RATs (Remote Access Trojans), which are shared among several Chinese APT groups.
[ad_2]
Source link
