[ad_1]

Pwn2Own Vancouver 2023 ended with contestants winning $1,035,000 and a Tesla Model 3 car for 27 zero-days (and multiple bug crashes) run between March 22-24.
During the hacking contestSecurity researchers targeted devices in the enterprise applications and communications, local escalation of privilege (EoP), virtualization, server, and automotive categories, all up-to-date and in their default configuration.
The total prize pool for Pwn2Own Vancouver 2023 was over $1,000,000 in cash and a Tesla Model 3, which The Synacktiv team won.
Hackers managed to elevate privileges and gain code execution on fully patched systems after hacking Windows 11, Microsoft Teams, Microsoft SharePoint, macOS, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox and, of course, the Tesla Model 3.
After zero-day vulnerabilities are exploited and reported during Pwn2Own, vendors have 90 days to release security patches before TrendMicro’s Zero Day initiative releases them publicly.
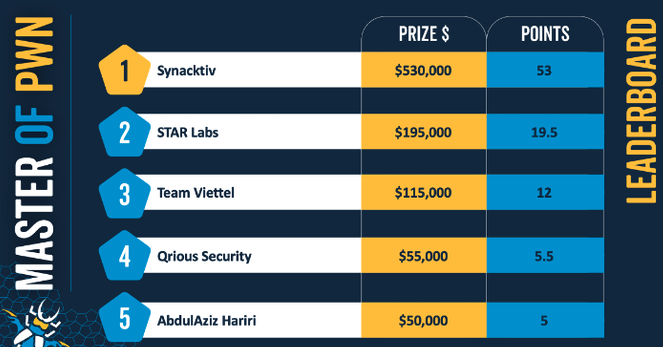
Competition dominated by Team Synacktiv
Team Synacktiv won the contest with 53 Master of Pwn points and $530,000 earned in total over the three days of the contest.
Day one of Pwn2Own Vancouver, Synacktiv hackers received $100,000 and a Tesla Model 3 after executing a time-of-check to time-of-use (TOCTOU) attack against the Tesla – Gateway in the automotive category. They also exploited a TOCTOU zero-day bug to increase privileges on Apple macOS and earn $40,000.
The second day of the competitionSynacktiv members’ hacking exploits were also the highlight of the show, with a $250,000 prize for David Berard (@_p0ly_) and Vincent Dehors (@voutside) after demonstrating a heap overflow and OOB write zero-day exploit chain against Tesla – Infotainment Unconfined Root.
Thomas Imbert of Synacktiv (@masthoon) and Thomas Bouzerar (@MajorTomSec) also demonstrated a chain of three bugs to elevate privileges on an Oracle VirtualBox host and won $80,000, while Tanguy Dubroca (@SidewayRE) received a $30,000 reward for an incorrect zero-day scaling pointer resulting in privilege escalation on Ubuntu Desktop.
The third and last day of the competitionThomas Imbert of Synacktiv (@masthoon) retired a fully patched Windows 11 system to earn $30,000 for Zero Day Use-After-Free (UAF).
THE STAR Labs Team also won $195,000 for zero-days in Microsoft SharePoint and VMWare Workstation and a collision with Ubuntu Desktop, while The Viettel team received $115,000 after hacking Microsoft Teams and Oracle VirtualBox.
Last year Pwn2Own Vancouver hacking contest, in May 2022, researchers won $1,155,000 and a car after hacking the Tesla Model 3 infotainment system and removing Windows 11, Ubuntu Desktop, Microsoft Teams, etc., using several bugs and zero-day exploit chains.
[ad_2]
Source link
