[ad_1]

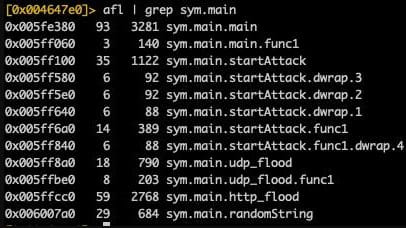
A new malicious botnet has been discovered targeting Realtek SDK, Huawei routers and Hadoop YARN servers to recruit devices into a DDoS (Distributed Denial of Service) swarm with the potential for massive attacks.
The new botnet was discovered by Akamai researchers earlier this year, who detected it on their HTTP and SSH honeypots, seen exploiting old flaws such as CVE-2014-8361 and CVE-2017 -17215.
Akamai comments that HinataBot operators initially distributed Mirai binaries, while HinataBot first appeared in mid-January 2023. It appears to be based on Mirai and is a Go-based variant of the notorious strain.
After capturing multiple samples of active campaigns as recently as March 2023, Akamai researchers concluded that the malware is under active development, with functional enhancements and anti-analysis additions.
Significant DDoS power
Malware is distributed by brute-forcing SSH endpoints or using infection scripts and RCE payloads for known vulnerabilities.
After infecting devices, the malware will run silently, waiting for commands to be executed from the command and control server.
Akamai analysts created their own C2 and interacted with simulated infections to stage HinataBot for DDoS attacks to observe the malware in action and infer its attack capabilities.
Older versions of HinataBot supported HTTP, UDP, ICMP, and TCP flooding, but newer variants only support the first two. However, even with only two attack modes, the botnet can potentially perform very powerful Distributed Denial of Service attacks.
Although HTTP and UDP attack commands differ, they both create a worker pool of 512 workers (processes) that send hard-coded data packets to targets for a set duration.
The size of HTTP packets is between 484 and 589 bytes. The UDP packets generated by HinataBot are particularly large (65,549 bytes) and consist of null bytes capable of overwhelming the target with a large volume of traffic.
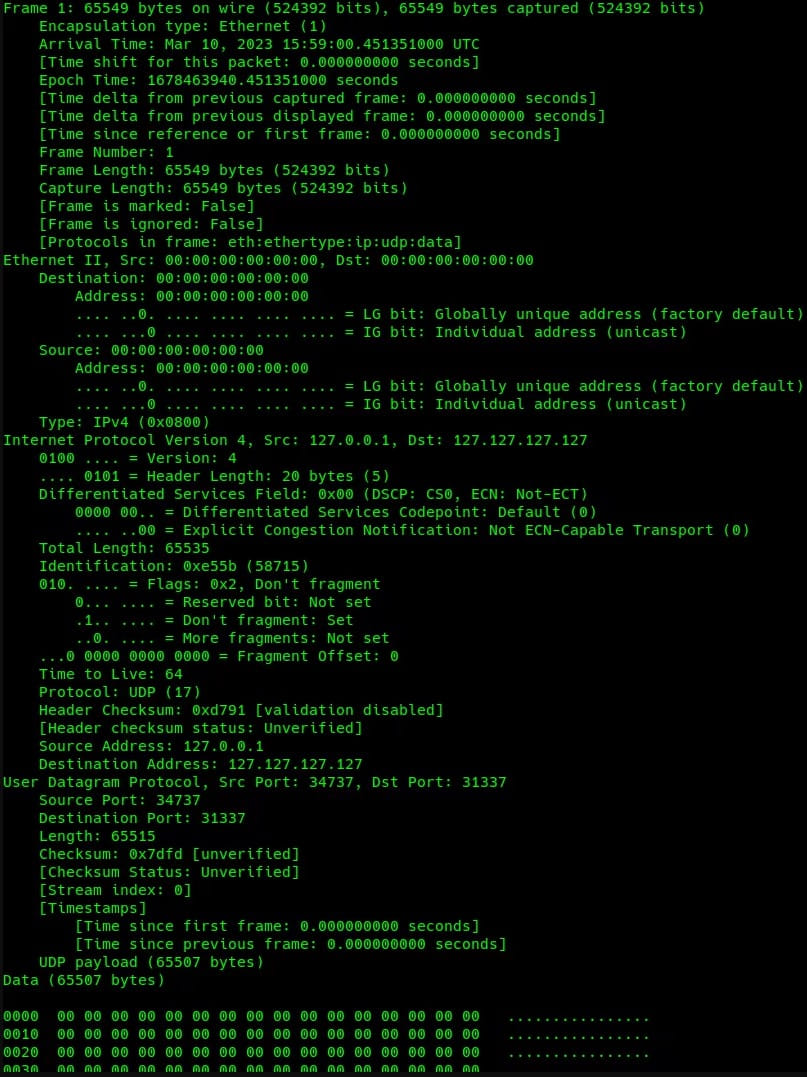
HTTP floods generate high volumes of website requests, while UDP floods send high volumes of garbage traffic to the target; therefore, the two methods attempt to achieve failure using a different approach.
Akamai evaluated the botnet in 10-second attacks for HTTP and UDP, and in the HTTP attack, the malware generated 20,430 requests for a total size of 3.4 MB. The UDP flood generated 6,733 packets totaling 421 MB of data.
The researchers estimated that with 1,000 nodes, the UDP flood could generate around 336 Gbps, while with 10,000 nodes, the attack data volume would reach 3.3 Tbps.
In the case of the HTTP flood, 1,000 trapped devices would generate 2,000,000 requests per second, while 10,000 nodes would take that number at 20,400,000 rps and 27 Gbps.
HinataBot is still under development and may implement more exploits and expand its targeting scope at any time. Moreover, the fact that its development is so active increases the likelihood that more potent versions will soon be circulating in the wild.
“These theoretical capacities obviously don’t take into account the different types of servers that would participate, their respective bandwidth and hardware capabilities, etc., but you get the picture,” warns Akamai.
“Let’s hope the authors of HinataBot turn to new hobbies before we have to deal with their full-scale botnet.”
[ad_2]
Source link
