[ad_1]

A ransomware operation known as Medusa began gaining momentum in 2023, targeting victimized businesses around the world with million-dollar ransom demands.
Operation Medusa began in June 2021 but had relatively low activity, with few casualties. However, in 2023, the ransomware gang increased its activity and launched a “Medusa blog” used to leak data to victims who refused to pay a ransom.
Medusa attracted media attention this week after claiming responsibility for a attack on the Minneapolis Public Schools District (MPS) and shared a video of the stolen data.
Will the real Medusa rise?
Many malware families are called Medusa, including one Mirai-based botnet with ransomware capabilities, a Medusa Android Malwareand the well known How MedusaLocker ransomware works.
Due to the commonly used name, there have been confusing reports of this ransomware family, with many believing it to be the same thing as MedusaLocker.
However, Medusa and MedusaLocker ransomware operations are entirely different.
Operation MedusaLocker launched in 2019 as Ransomware-as-a-Service, with numerous affiliates, ransom note commonly referred to as How_to_back_files.htmland a wide variety of file extensions for encrypted files.
The MedusaLocker operation uses a Tor website at qd7pcafncosqfqu3ha6fcx4h6sr7tzwagzpcdcnytiw3b6varaeqv5yd.onion for negotiation.
However, the Medusa ransomware operation was launched around June 2021 and used a ransom note named !!!READ_ME_MEDUSA!!!.txt and a static encrypted file extension of .JELLYFISH.
Operation Medusa also uses a Tor website for ransom negotiations, but this is located at medusacegu2ufmc3kx2kkqicrlcxdettsjcenhjena6uannk5f4ffuyd.onion.
How Medusa encrypts Windows devices
BleepingComputer was only able to analyze the Medusa cipher for Windows, and it’s unclear if they have one for Linux at this time.
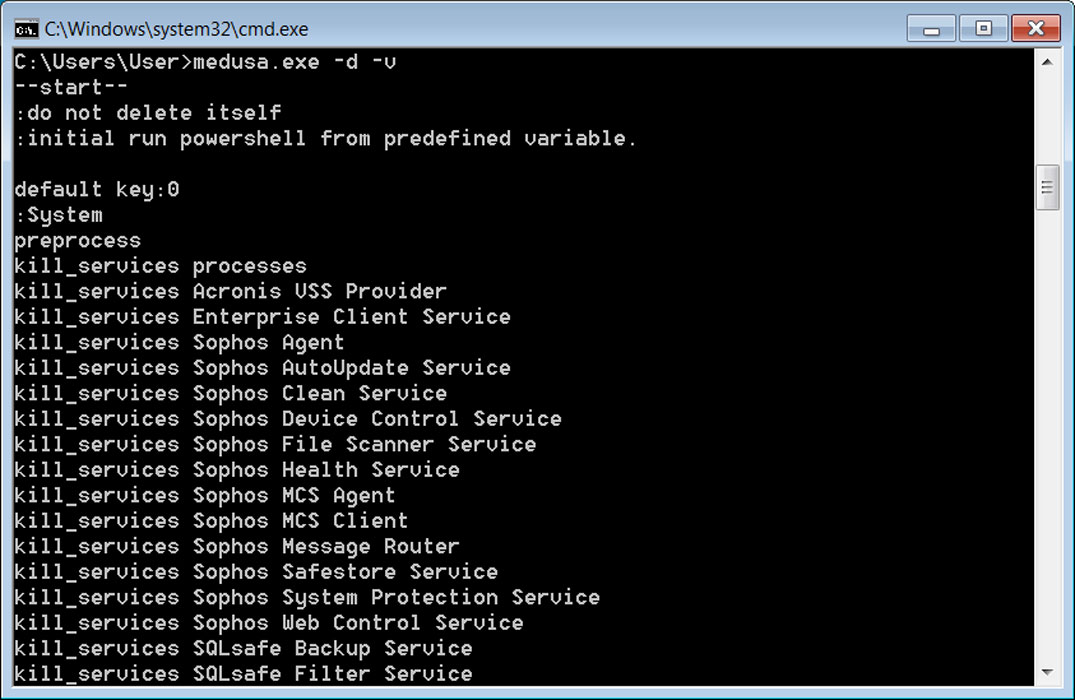
The Windows Encryptor will accept command line options that allow the threat actor to configure how files will be encrypted on the device, as shown below.
# Command Line
Option | Description
---------------------
-V | Get version
-d | Do not delete self
-f | Exclude system folder
-i | In path
-k | Key file path
-n | Use network
-p | Do not preprocess (preprocess = kill services and shadow copies)
-s | Exclude system drive
-t | Note file path
-v | Show console window
-w | Initial run powershell path (powershell -executionpolicy bypass -File %s)
For example, the -v command line argument will cause the ransomware to display a console, displaying status messages as it encrypts a device.
Source: BleepingComputer
When run regularly, without command line arguments, Medusa ransomware will terminate over 280 Windows services and processes for programs that may be preventing file encryption. These include Windows services for mail servers, database servers, backup servers, and security software.
The ransomware will then delete Windows Volume Shadow Copies to prevent them from being used to recover files.
deletes shadow volume copies
vssadmin Delete Shadows /all /quiet
vssadmin resize shadowstorage /for=%s /on=%s /maxsize=unbounded
Ransomware Expert Michael Gillespie also analyzed the encryptor and told BleepingComputer that it encrypts files using AES-256 + RSA-2048 encryption using the BCrypt library.
Gillespie further confirmed that the encryption method used in Medusa is different from that used in MedusaLocker.
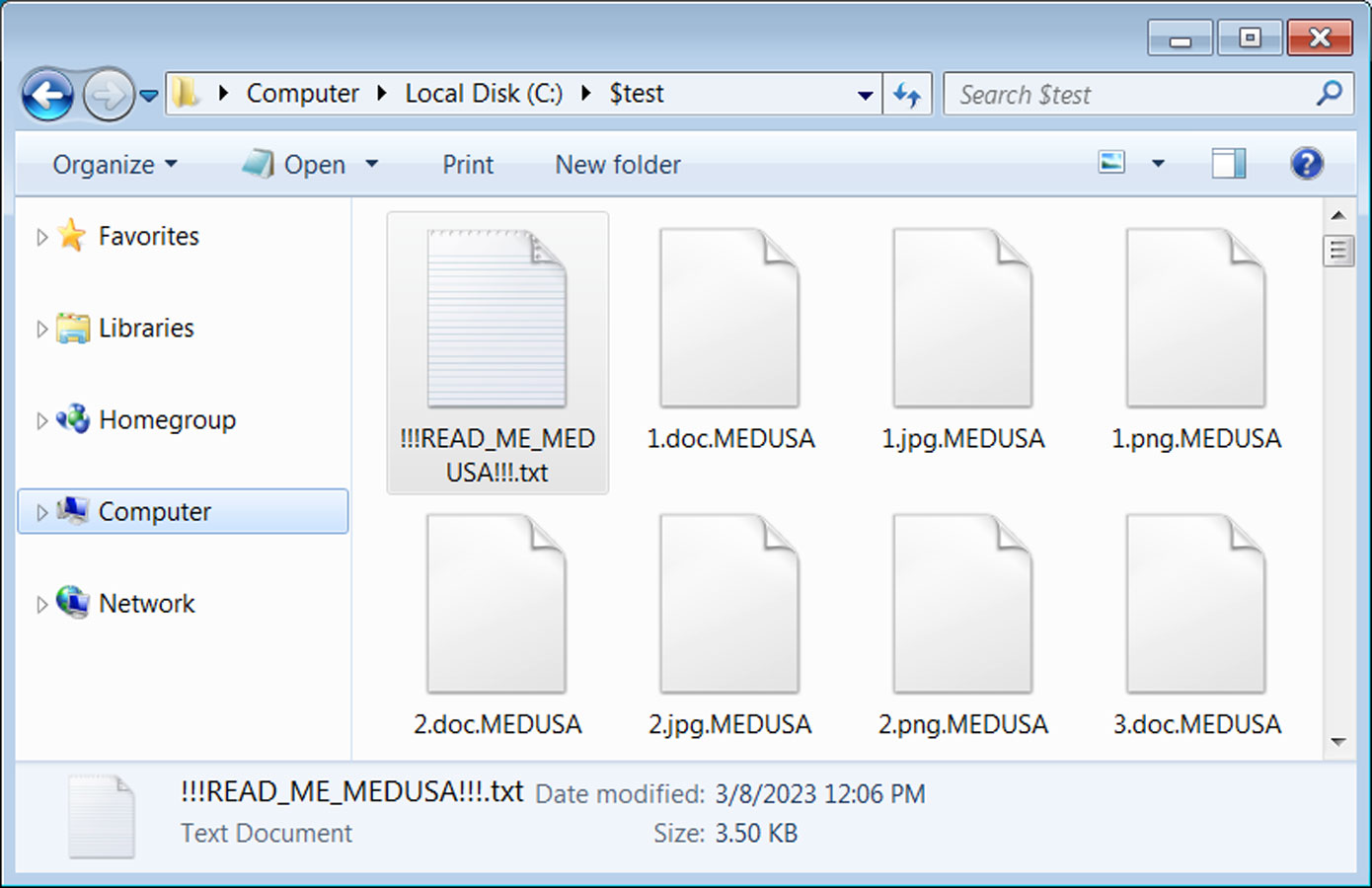
While encrypting files, the ransomware will append the .JELLYFISH extension to encrypted filenames as shown below. For example, 1.doc would be encrypted and renamed to 1.doc.MEDUSA.
Source: BleepingComputer
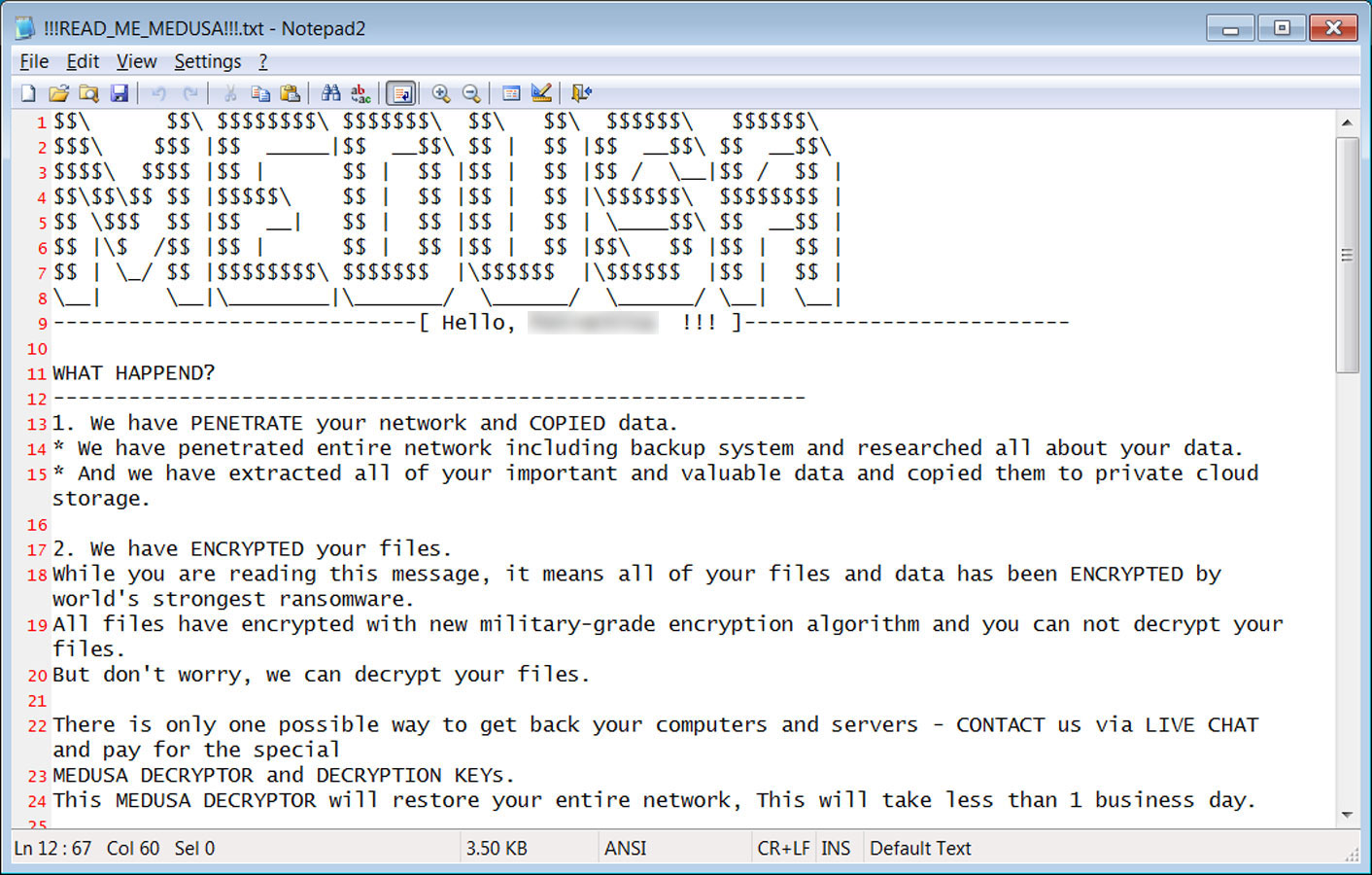
In each folder, the ransomware will create a ransom note named !!!READ_ME_MEDUSA!!!.txt which contains information about what happened to the victim’s files.
The ransom note will also include extension contact information including Tor data leak site, Tor trading site, Telegram channel, Tox ID and email address key.medusa.serviceteam@ protonmail.com.
The Tor trading site is at http://medusacegu2ufmc3kx2kkqicrlcxdettsjcenhjena6uannk5f4ffuyd.onion.
Source: BleepingComputer
As an additional step to prevent file restoration from backups, Medusa ransomware will run the following command to delete locally stored files associated with backup programs, like Windows Backup. This command will also delete virtual disk hard disks (VHDs) used by virtual machines.
del /s /f /q %s*.VHD %s*.bac %s*.bak %s*.wbcat %s*.bkf %sBackup*.* %sbackup*.* %s*.set %s*.win %s*.dsk
The Tor trading site is called “Secure Chat”, where each victim has a unique ID that can be used to communicate with the ransomware gang.
Source: BleepingComputer
Like most ransomware operations targeting businesses, Medusa has a data leak site called “Medusa Blog”. This site is used as part of the gang’s double extortion strategy, where they leak data for victims who refuse to pay a ransom.
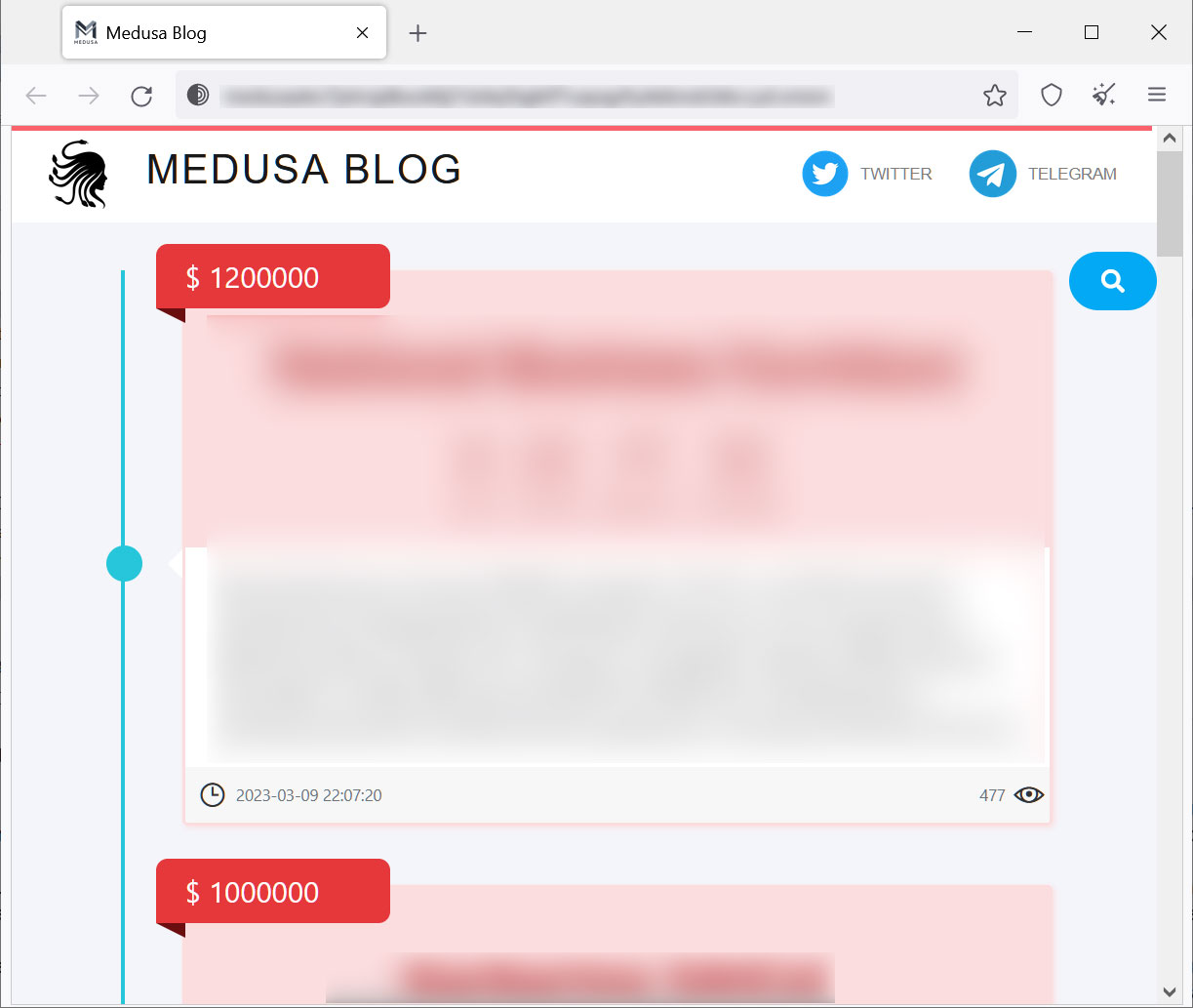
Source: BleepingComputer
When a victim is added to the data leak, their data is not immediately released. Instead, threat actors offer victims paid options to extend the countdown to release data, delete data, or download all data. Each of these options has different prices as shown below.
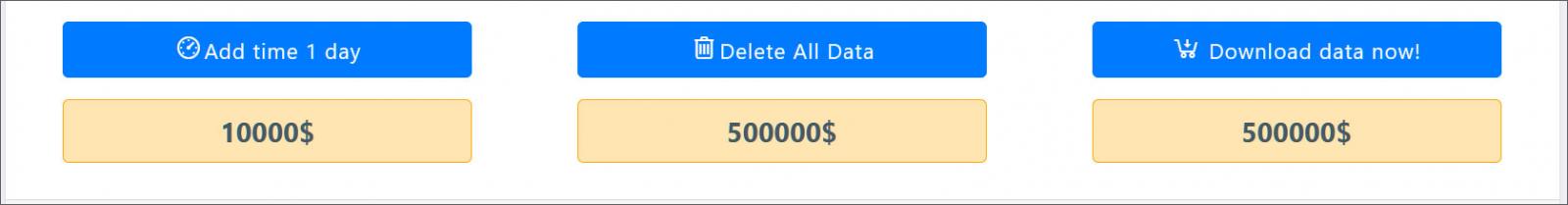
Source: BleepingComputer
These three options are made to apply extra pressure on victim to scare them and make them pay ransom.
Unfortunately, there are no known weaknesses in the Medusa Ransomware encryption that allow victims to recover their files for free.
Researchers will continue to analyze the encryptor, and if a weakness is discovered, we will report it to BleepingComputer.
[ad_2]
Source link
