[ad_1]
Hackers have targeted gaming and online gaming companies with what appears to be a never-before-seen backdoor that researchers have named IceBreaker.
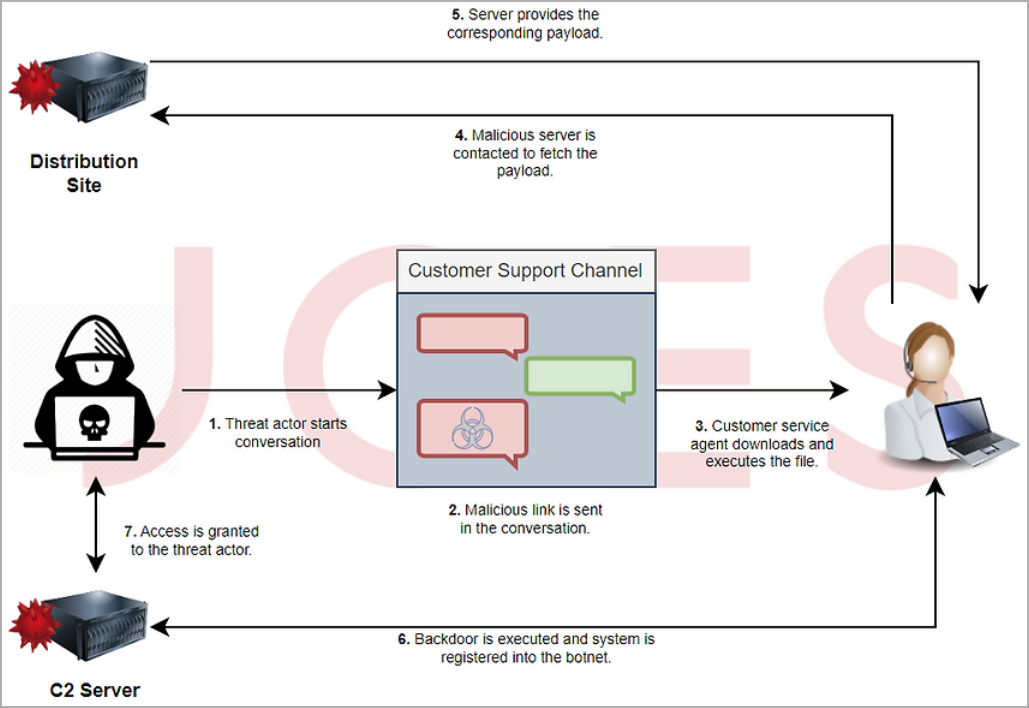
The compromise method involves tricking customer service agents into opening malicious screenshots that the malicious actor sends under the guise of a user experiencing a problem.
Such attacks have been occurring since at least September 2022. The group behind them remains unknown, with indistinct clues pointing to their origin.
Researchers from incident response firm Security Joes believe the IceBreaker backdoor is the work of a new advanced threat actor that uses “a very specific social engineering technique”, which could lead to a more clear who they are.
After analyzing data from one incident in September, Security Joes was able to respond to three more attacks before hackers could compromise their targets.
Researchers say the only public evidence of threat actor IceBreaker they could find was a tweet from MalwareHunterTeam in October.
Fool customer service
To deliver the backdoor, the threat actor contacts the target company’s customer support pretending to be a user having problems logging in or registering for the online service.
The hackers convince the support agent to upload an image that describes the problem better than they can explain it. The researchers say the image is usually hosted on a fake website posing as a legitimate service, although they’ve also seen it delivered from Dropbox storage.
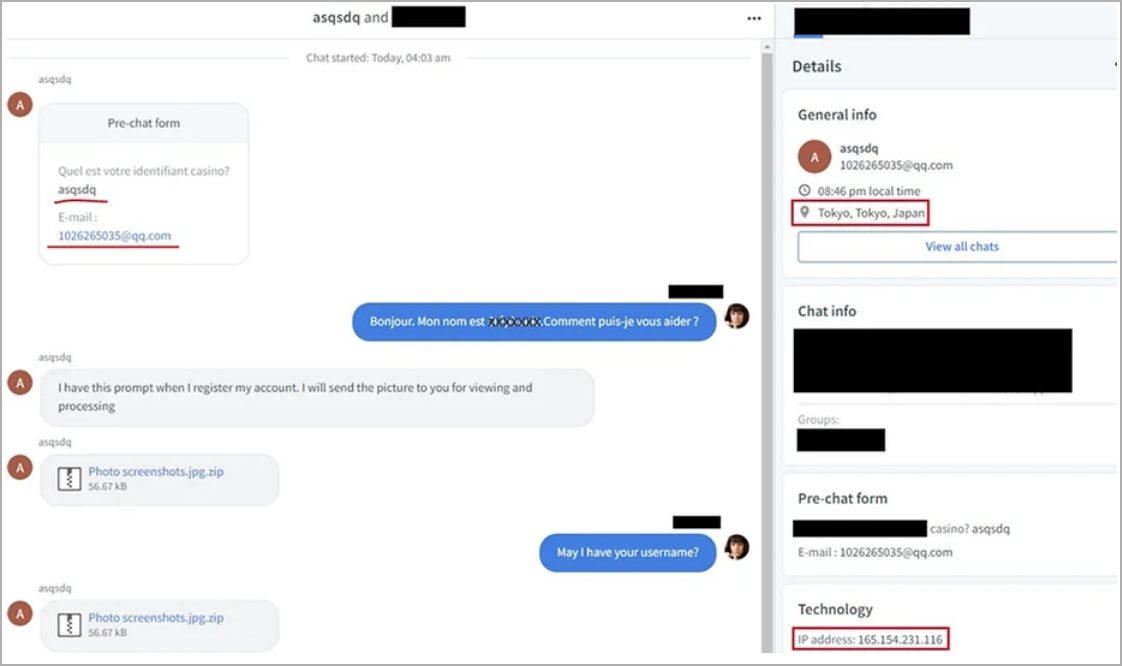
SecurityJoes says dialogues it has reviewed between the threat actor and support agents indicate that IceBreaker is not a native English speaker and is deliberately asking to speak with Spanish-speaking agents. However, they have also been seen speaking other languages.
Links delivered this way lead to a ZIP archive containing a malicious LNK file that fetches the IceBreaker backdoor, or a Visual Basic script that downloads the Houdini RAT which has been active since at least 2013.
As shown in the image below, the Windows shortcut file icon has been changed to make it harmless. The shortcut contains a command to download an MSI payload from the attacker’s server, install it without user interaction, and run it without a user interface.
Security Joes researchers claim that the downloaded malware is “a very complex compiled JavaScript file” that can discover running processes, steal passwords, cookies and files, open a proxy tunnel for the attacker, as well as running scripts fetched from the attackers’ server. .
The IceBreaker Backdoor
The malicious LNK is the primary first-stage payload delivering the IceBreaker malware, while the VBS file is used as a backup, in case the customer support operator is unable to run the shortcut.
The malicious shortcut file comes as a JPG image and its extension is changed accordingly. The MSI payload it downloads has a very low detection rate on Virus Total, returning only 4 positives out of 60 scans.
The MSI package includes a large number of decoy files to evade detection tools and signature-based scanning engines. The final layer is an extracted CAB archive in the victim’s temporary folder, removing the “Port.exe” payload.
Security Joes says it’s a 64-bit C++ executable with an unusual overlay, retaining some of the appended data at the end of the file. Analysts believe this is a way to hide additional resources from security products.
After further analysis, Security Joes concluded that the sample was a previously unreleased module backdoor written in Node.js, providing threat actors with the following capabilities:
- Customization via plugins that extend the malware’s built-in functionality.
- Process discovery.
- Steal passwords and cookies from local storage, especially Google Chrome.
- Enable a Socks5 reverse proxy server.
- Establish persistence by creating a new LNK file (WINN.lnk) in the Windows startup folder.
- Exfiltrate files to the remote server via web sockets.
- Run custom VBS scripts.
- Take screenshots.
- Generate remote shell sessions.
If the targeted entity has not outsourced customer support services to an external vendor, threat actors can use the backdoor to steal account credentials, move laterally in the network and expand their intrusion .
At this time, not much is known about the IceBreaker group, but Security Joes has decided to publish a report on their findings and share all captured IoCs (indicators of compromise) to help defenders detect and combat this threat.
The researchers published a technical report describing the threat actor’s modus operandi and how their backdoor works. YARA rules have also been released to help organizations detect malware.
Additionally, Security Joes recommends companies that suspect a breach with IceBreaker to search for created shortcut files in the Startup folder and check for unauthorized execution of the open source tool. tsocks.exe.
Follow-up of the creation of msiexec.exe processes that receive URLs as parameters can also be an indication of compromise, as can running VBS scripts and LNK files from the temporary folder.
[ad_2]
Source link
