[ad_1]

Attacks targeting government agencies and military bodies in several APAC countries have been attributed to what appears to be a new advanced threat actor that leverages custom malware to steal confidential information.
Security researchers call this group Dark Pink (Group-IB) or Saaiwc Group (Anheng Hunting Labs), noting that it uses uncommon tactics, techniques and procedures (TTPs).
The custom toolkit seen in the attacks can be used to steal information and distribute malware via USB drives. The actor used DLL sideloading and event-triggered execution methods to execute its payloads on compromised systems.
A report published by a cybersecurity company Group-IB says that the threat actor’s goal is to steal information from victim’s browsers, access messengers, exfiltrate documents, and capture audio from the infected device’s microphone.
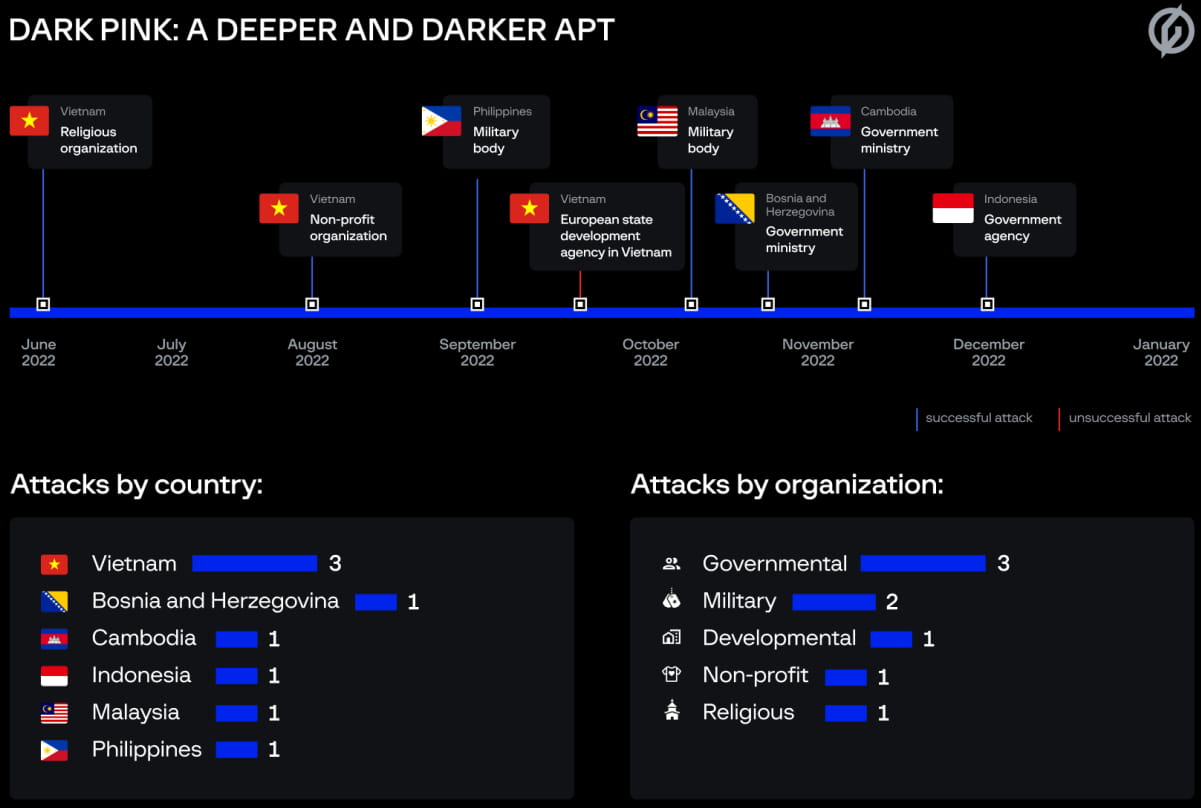
Considered an Advanced Persistent Threat (APT), Dark Pink launched at least seven successful attacks between June and December 2022.
Initial compromise
Dark Pink’s typical initial attack vector is spear phishing emails disguised as job applications, which tricked the victim into downloading a malicious ISO image file. Beyond this stage, Group-IB saw multiple variations in the attack chain.
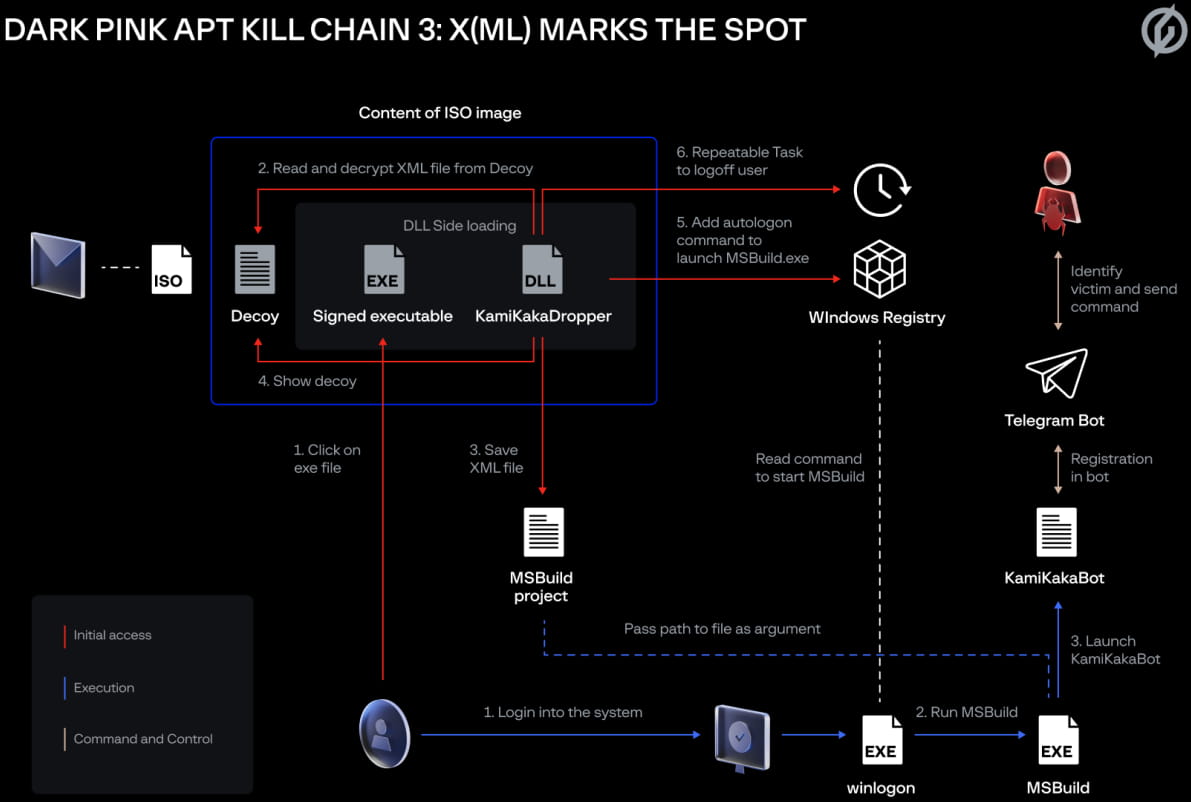
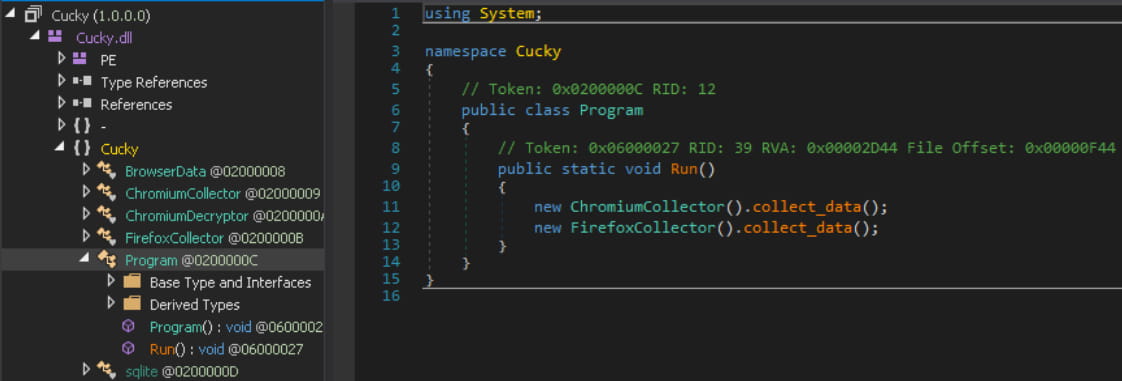
One of them used an all-inclusive ISO file storing a decoy document, a signed executable, and a malicious DLL file, which led to the deployment of one of two custom info-stealers used by the group (Ctealer or Cucky) via DLL sideloading. . In the next stage, a registry implant called TelePowerBot would be dropped.
Another attack chain uses a Microsoft Office document (.DOC) in an ISO file. When the victim opens the file, a template with a malicious macro is extracted from GitHub, responsible for loading TelePowerBot and making changes to the Windows registry.
A third chain of attacks observed in December 2022 was identical to the first. However, instead of loading TelePowerBot, the malicious ISO file and DLL sideloading technique loads another custom malware that researchers call KamiKakaBot, which is designed to read and execute commands.
Custom malware
Cucky and Ctealer are custom infostealers written in .NET and C++ respectively. Both attempt to locate and extract passwords, browsing history, saved logins and cookies from a long list of web browsers: Chrome, Microsoft Edge, CocCoc, Chromium, Brave, Atom, Uran, Sputnik, Slimjet, Epic Privacy, Amigo, Vivaldi, Kometa, Nichrome, Maxthon, Comodo Dragon, Avast Secure Browser and Yandex Browser.
TelePowerBot is a registry implant that launches via a script at system startup and connects to a Telegram channel from which it receives PowerShell commands to execute.
“During infection, threat actors run several standard commands (e.g. net share, Get-SmbShare) to determine what network resources are connected to the infected device. If network disk usage is found, they will start exploring this disk to find files that might interest them and possibly exfiltrate them” – Group-IB
In general, commands can start simple console tools or complex PowerShell scripts that allow lateral movement through USB removable drives.
KamiKakaBot is the .NET version of TelePowerBot, which also comes with information theft capabilities, targeting data stored in Chrome and Firefox browsers.
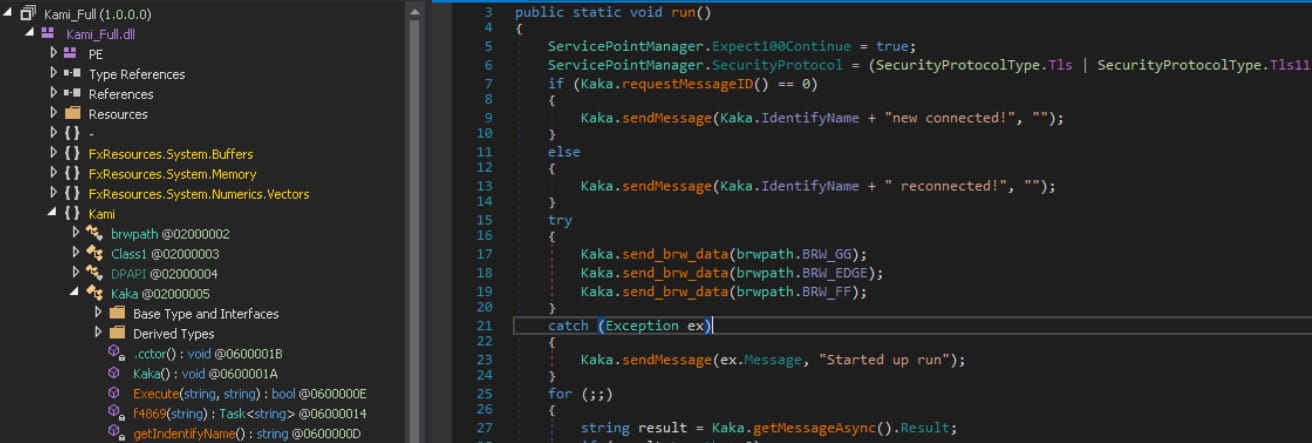
In addition to these tools, Dark Pink also uses a script to record sound through the microphone every minute. The data is saved as a ZIP archive in the Windows temporary folder before being exfiltrated to the Telegram bot.
Also, the threat actor uses a special mail exfiltration utility named ZMsg, downloaded from GitHub. The utility steals communications from Viber, Telegram and Zalo and stores them on “%TEMP%\KoVosRLvmU\” until they are exfiltrated.
A previous report from Chinese cybersecurity firm Anheng Hunting Labs, which tracks Dark Pink as a Saaiwc group, describes some attack chains and notes that in one of them, the actor used a Microsoft Office template with malicious macro code to exploit an old high-severity vulnerability identified as CVE-2017-0199.
Although Group-IB confirms with high confidence that Dark Pink is responsible for seven attacks, the researchers note that the number could be higher.
The company has notified all seven organizations of the threat actor’s compromised activity and will continue to monitor Dark Pink’s operations.
[ad_2]
Source link
