[ad_1]

South African threat actors known as “Automated Libra” have improved their techniques to make profit by utilizing cloud platform resources for cryptocurrency mining.
According to Palo Alto Networks Unit 42, threat actors are using a new CAPTCHA resolution system, tracking more aggressive use of CPU resources for mining, and mixing “freejacking” with the “Play and Run” technique to abuse free cloud resources.
The “Automated Libra” was first unveiled by Sysdig analysts in October 2022who named the malicious activity group “PurpleUrchin” and believed the group was dedicated to freejacking operations.
Unit 42 dove deeper into this operation, analyzing over 250GB of collected data and uncovering much more about the threat actor’s infrastructure, history and techniques.
Introducing Automated Libra
The malicious actor runs automated campaigns by abusing continuous integration and deployment (CI/CD) service providers, such as GitHub, Heroku, Buddy.works, and Togglebox, to create new accounts on the platforms and run cryptocurrency miners in containers.
While Sysdig has identified 3,200 malicious accounts belonging to “PurpleUrchin”, Unit 42 now reports that the malicious actor has created and used more than 130,000 accounts on the platforms since August 2019, when the first signs of its activities can be traced.
Additionally, Unit 42 discovered that the threat actor not only used containerized components for mining, but also to trade the mined cryptocurrency on various exchanges including ExchangeMarket, crex24 , Luno and CRATEX.
New gameplay and racing tactics
Sysdig has noticed that threat actors engage in “freejacking”, attempting to exploit all available resources allocated to free accounts, trying to make significant profits by ramping up its operations.
Unit 42 confirms that freejacking is an important aspect of PurpleUrchin’s operations, but reports that the “Play and Run” strategy is also heavily involved.
Play and Run is a term for threat actors using paid resources for profit, in this case cryptomining, and refusing to pay the bills until their accounts are frozen. At that point, they abandon them and move on.
Typically, PurpleUrchin uses stolen PII and credit card data to create premium accounts on various VPS and CSP platforms, so that no one can track them down when they leave unpaid debts.
“The actor also seemed to reserve a full server or cloud instances and they sometimes used CSP services like AHPs,” explains the Unit 42 report.
“They did this in order to facilitate the hosting of web servers needed to monitor and track their large-scale mining operations.”
In these cases, the threat actor uses as much CPU resources as possible before losing access to them.
This contrasts with the tactics followed in freejacking campaigns, where the miner only uses a tiny fraction of the CPU power of the server.
GitHub CAPTCHA Resolution
One notable technique employed by Automated Libra is a CAPTCHA solving system that helps them create numerous accounts on GitHub without requiring manual intervention.
Threat actors use ImageMagic’s “convert” tool to convert CAPTCHA images to their RGB equivalents, then use the “identify” tool to extract the red channel asymmetry for each image.
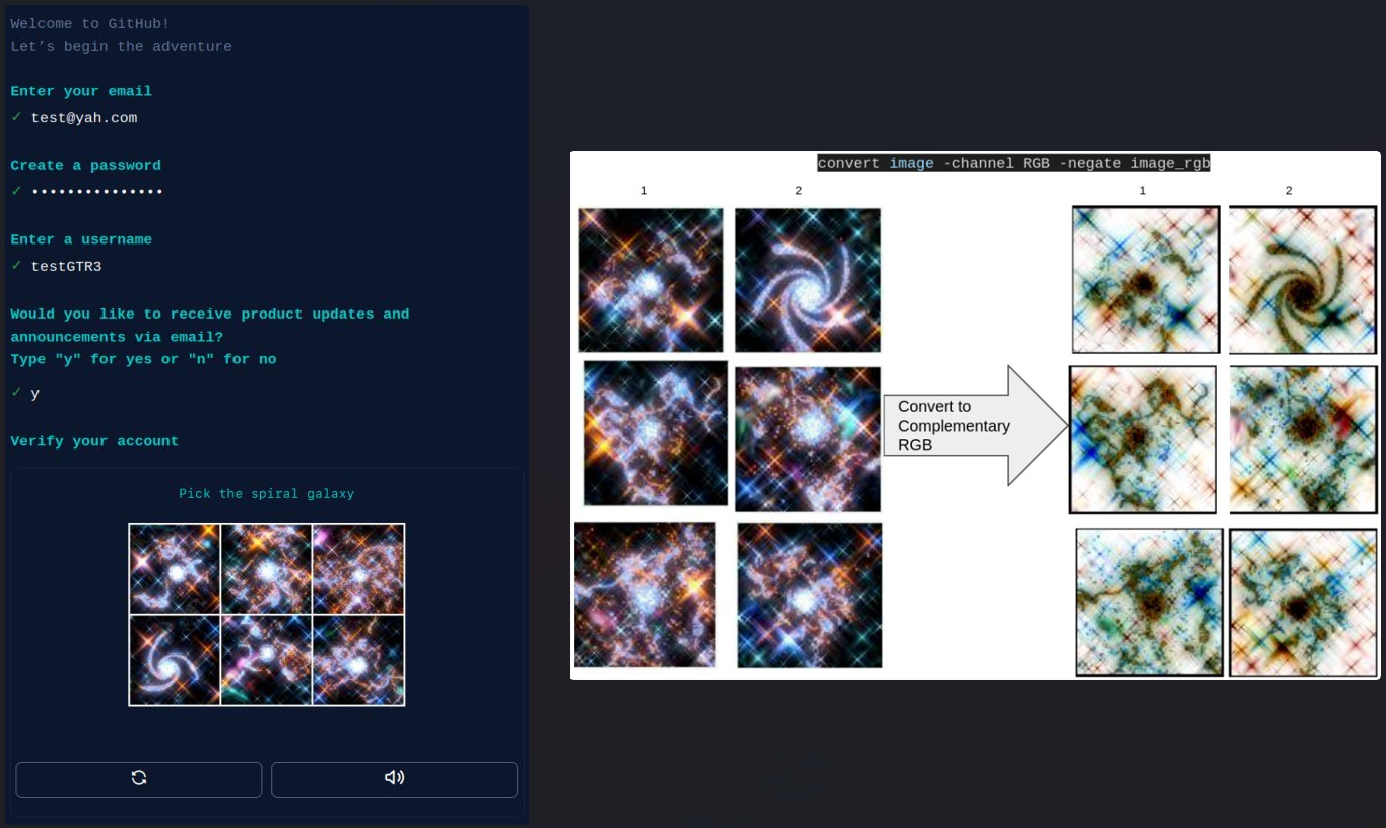
.png)
The value provided by the “Identify” tool is used to classify the images in ascending order. Finally, the automated tool uses the array to select the image at the top of the list, which is usually the correct one.
This system highlights Automated Libra’s determination to achieve greater operational efficiency by increasing the number of accounts per minute they can create on GitHub.
[ad_2]
Source link
