[ad_1]

Three Android apps that allow users to use devices as remote keyboards for their computers have critical vulnerabilities that could expose key presses and allow remote code execution.
The apps are PC Keyboard, Lazy Mouse and Telepad, and their vulnerable versions (free and paid) and in Google Play have a combined install count of over two million.
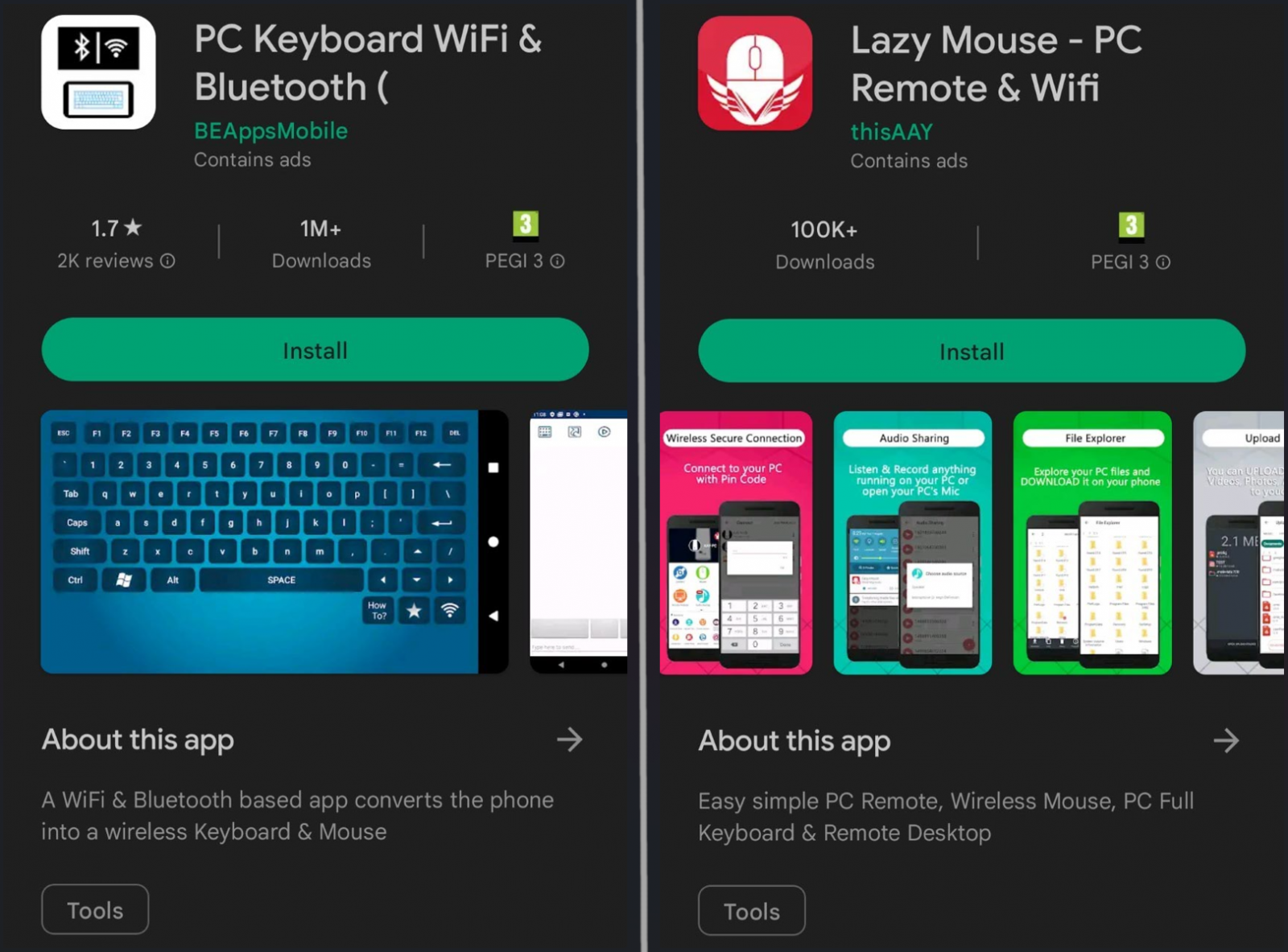
The critical weaknesses were discovered by Synopsys analysts, who notified application developers of their findings in August 2022.
The researchers issued a security advisory today, after attempting to contact the software vendors again in October 2022 without getting a response.
“CyRC’s research revealed weak or missing authentication mechanisms, missing permissions, and insecure communication vulnerabilities in all three apps,” read the review.
“Although the vulnerabilities are all related to authentication, authorization, and forwarding implementations, each application’s failure mechanism is different” – Synopsys
The vulnerabilities impacting each application are as follows:
- CVE-2022-45477 (Severity Rating 9.8) – Flaw in Telepad, allowing an unauthenticated remote user to send instructions to the server to execute arbitrary code without requiring authorization or authentication.
- CVE-2022-45478 (severity rating 5.1) – Telepad defect allowing an attacker to perform a man-in-the-middle (MITM) attack and read all key presses in clear text.
- CVE-2022-45479 (severity rating 9.8) – PC keyboard flow allowing an unauthenticated remote user to send instructions to the server to execute arbitrary code without requiring authorization or authentication.
- CVE-2022-45480 (severity rating 5.1) – PC keyboard flaw allowing an attacker to perform a man-in-the-middle (MITM) attack and read all key presses in clear text.
- CVE-2022-45481 (Severity Rating 9.8) – Lazy Mouse’s default configuration does not require a password, allowing unauthenticated remote users to execute arbitrary code without requiring authorization or authentication.
- CVE-2022-45482 (Severity Rating 9.8) – Lazy Mouse server weakness enforces weak password requirements without implementing rate limiting, allowing unauthenticated attackers to brute force the PIN and execute arbitrary commands.
- CVE-2022-45483 (severity rating 5.1) – Lazy Mouse flaw allowing an attacker to perform a man-in-the-middle (MITM) attack and read all key presses in clear text.
The three applications are no longer maintained or supported by their developers, so they meet the criteria for defining “abandonware”.
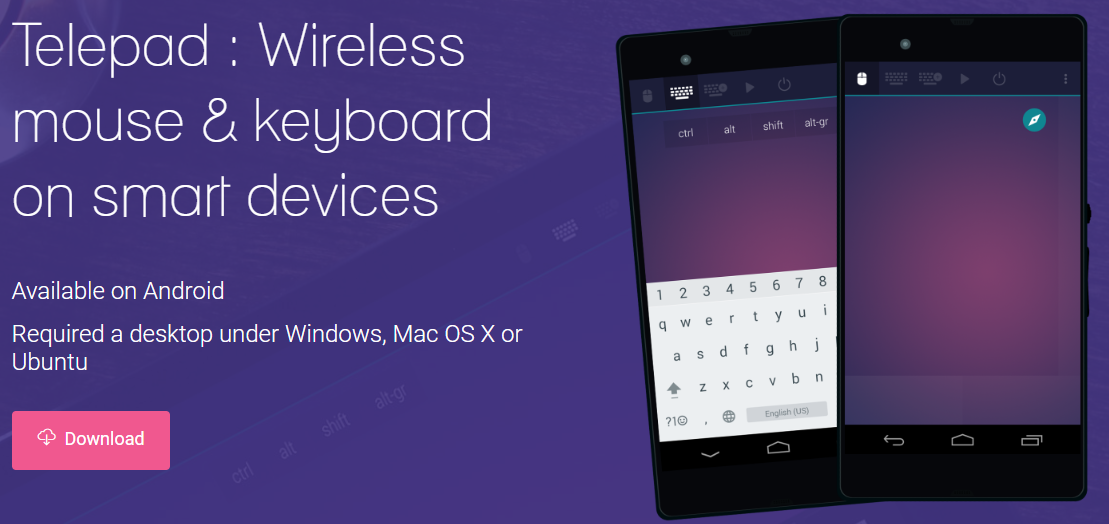
Continuing to use the apps carries a significant risk of exposing sensitive information. A successful exploit could also allow remote attackers to execute arbitrary code on the device.
If you are looking for a remote keyboard app, there are several actively maintained projects on Google Play, many of which have positive user ratings.
Before installing any alternative app, be sure to check user reviews, carefully read the project’s privacy policy, and check the date of the last update. If possible, users should try to confirm that data in transit is encrypted.
[ad_2]
Source link
