[ad_1]

The first known cryptojacking operation exploiting the Dero coin was discovered targeting a vulnerable Kubernetes container orchestrator infrastructure with exposed APIs.
Dero is a privacy coin promoted as an alternative to Monero with even more robust anonymity protection.
Compared to Monero or other cryptocurrencies, Dero promises faster and higher monetary mining rewards, which is probably why it has caught the attention of threat actors.
In a new report from CrowdStrike, researchers explain how the ongoing campaign was uncovered in February 2023 after discovering unusual behavior while monitoring customer Kubernetes clusters.
Analyze Kubernetes
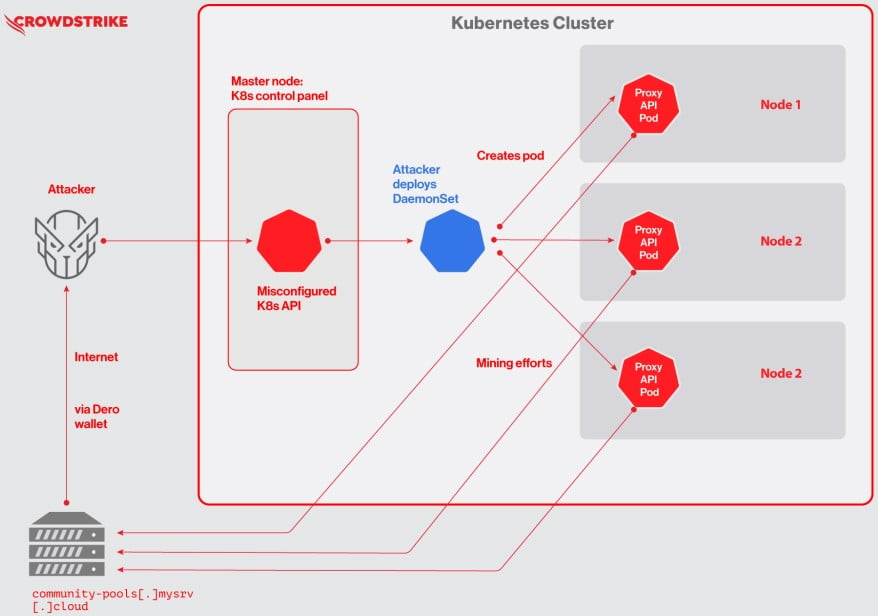
The researchers say the attacks begin with threat actors scanning exposed and vulnerable Kubernetes clusters with authentication set to –anonymous-auth=true, allowing anyone to access the Kubernetes API anonymously.
After gaining access to the API, threat actors will deploy a DaemonSet named “proxy-api” which allows attackers to simultaneously commit the resources of all nodes in the cluster and exploit Dero using the resources available.
Installed miners will be joined in a Dero mining pool, where everyone contributes hash power and receives shares of all rewards.
Crowdstrike states that the Docker image used in the observed Dero cryptojacking campaign was hosted on Docker Hub and is a slightly modified CentOS 7 image containing additional files named “entrypoint.sh” and “pause”.
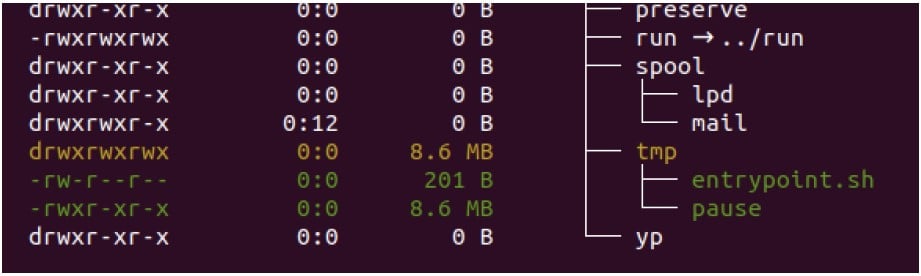
The first file initializes the Dero miner with a hard-coded wallet address and mining pool, while the “pause” binary is the actual coin miner.
Crowdstrike analysts did not notice any threat actor intent to move laterally, disrupt cluster operation, steal data, or cause other harm, so the campaign appears to be 100% motivated. by finance.
A turf war
Shortly after Crowdstrike uncovered the Dero campaign, its analysts detected a Monero cryptojacking operator attempting to hijack the same resources, ultimately kicking out the Dero miner.
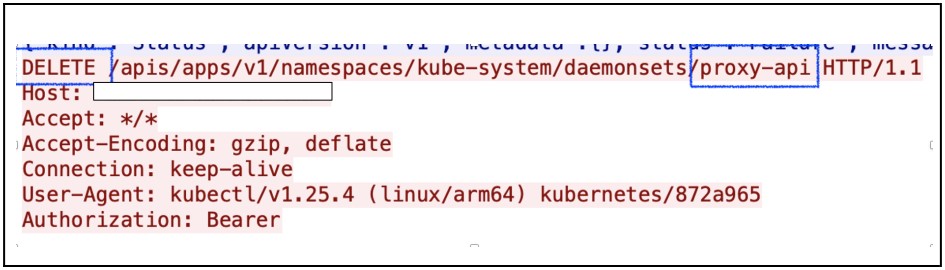
The second threat actor removed the “proxy-api” DaemonSet used by the Dero campaign, then performed a much more aggressive takeover of the cluster, using a privileged pod and mounting a “host” directory, attempting to s escape from the container.
Next, the threat actor used a custom XMRig miner downloaded from the attacker’s command and control server to mine Monero by switching to the host and installing a custom service.
The Monero campaign chose to mine on the host instead of the pods, like Dero did, to access more compute resources and make a bigger profit.
Also, running data mining processes on the host makes them harder to detect if properly hidden as system services.
Finally, the operator installed a cronjob to trigger the payload, thus ensuring persistence between Kubernetes cluster restarts.
While cryptojacking campaigns are almost a dime, mining Dero on other privacy coins, such as Monero, makes it a new campaign.
[ad_2]
Source link
