[ad_1]

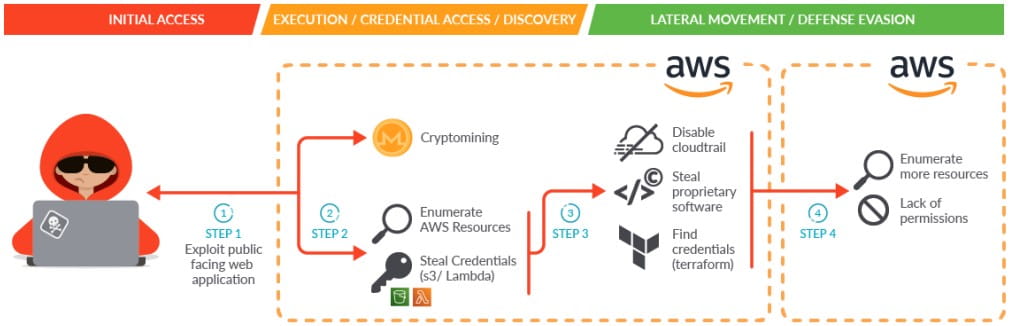
An advanced hacking operation dubbed “SCARLETEEL” targets public-facing web applications running in containers to infiltrate cloud services and steal sensitive data.
SCARLETEEL was discovered by cybersecurity intelligence firm Sysdig while responding to an incident in the cloud environment of one of its clients.
As the attackers deployed cryptominers in the compromised cloud environments, the hackers showed advanced expertise in AWS cloud mechanics, which they used to dig deeper into the company’s cloud infrastructure.
Sysdig believes the cryptojacking attack was used as a decoy for the threat actors’ real goal, which was to steal proprietary software.
SCARLET Attacks
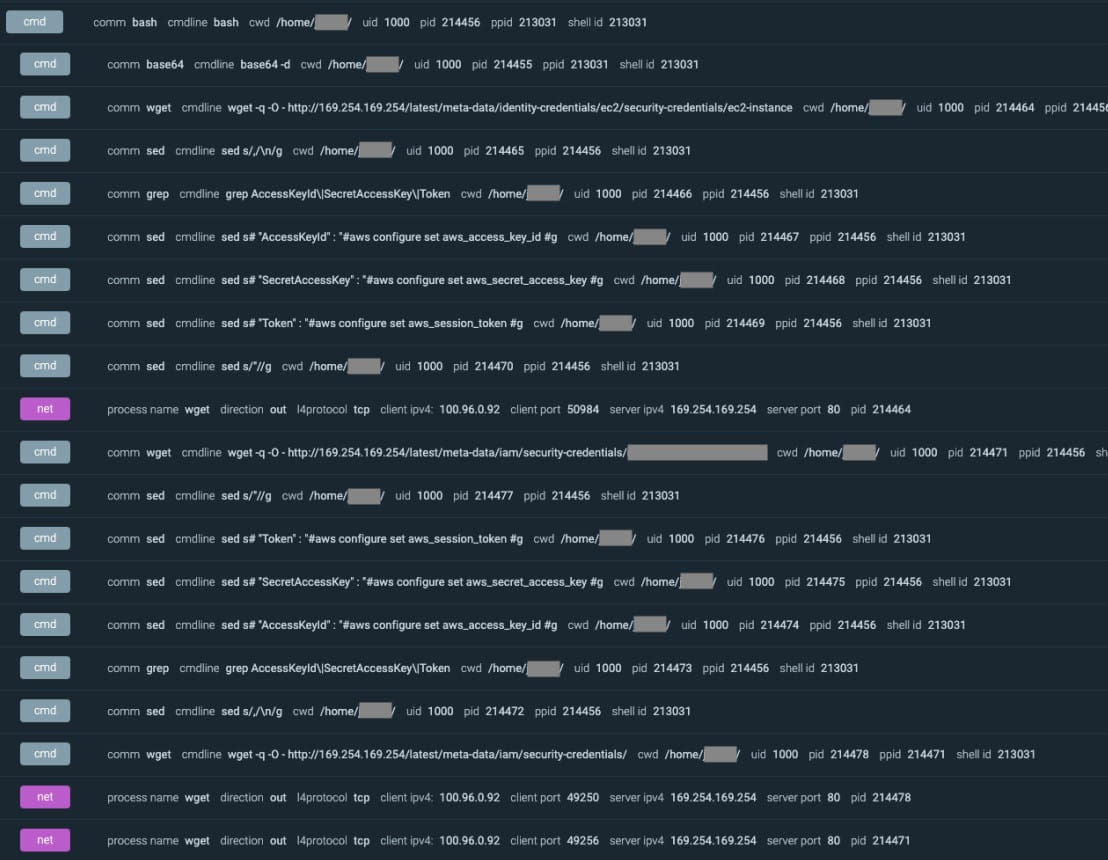
The SCARLETEEL attack began with hackers exploiting a vulnerable public service in a self-managed Kubernetes cluster hosted on Amazon Web Services (AWS).
Once the attackers gain access to the container, they download an XMRig coinminer, which is supposed to act as a decoy, and a script to extract account credentials from the Kubernetes pod.
The stolen credentials were then used to make AWS API calls to gain persistence by stealing other credentials or creating backdoor users and groups in the cloud environment. ‘business. These accounts were then used to spread further in the cloud environment.
Depending on the AWS cluster role configuration, attackers can also access Lambda information, such as functions, configurations, and access keys.
Source: Sysdig
Then the attacker uses Lambda functions to enumerate and retrieve all proprietary code and software along with their runtime keys and Lambda function environment variables to find the IAM user credentials and exploit for subsequent enumeration cycles and privilege escalation.
Enumeration of S3 buckets also occurs at this point, and files stored in cloud buckets are likely to contain data valuable to attackers, such as account credentials.
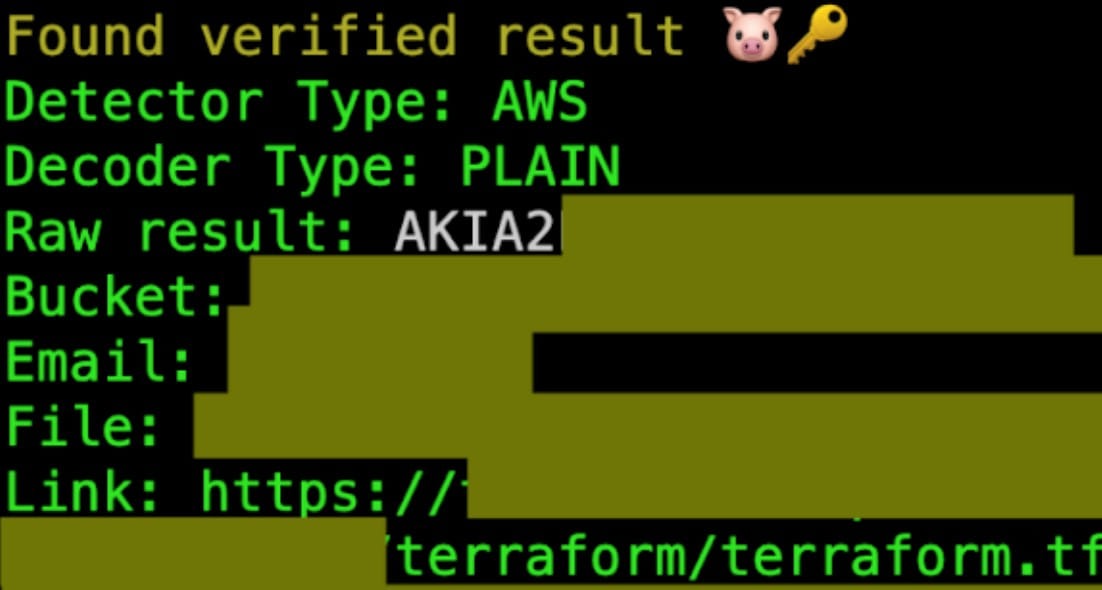
“During this particular attack, the attacker was able to retrieve and read over 1TB of information, including client scripts, troubleshooting tools, and log files,” the Sysdig report read.
“The 1TB of data also included Terraform-related log files, which were used in the account to deploy some of the infrastructure. These Terraform files will play an important role in the later stage where the attacker attempted to pivot to another AWS account.” – Sysdig.
Source: Sysdig
To minimize the traces left behind, the attacker attempted to disable CloudTrail logs in the compromised AWS account, which negatively impacted Sysdig’s investigation.
However, it was apparent that the attacker had retrieved Terraform state files from S3 buckets containing IAM user access keys and a secret key for a second AWS account. This account was ultimately used for lateral travel within the organization’s cloud network.
Source: Sysdig
Secure your cloud-based infrastructure
As the company increasingly relies on cloud services to house its infrastructure and data, hackers are following suit, becoming expert APIs and management consoles to pursue their attacks.
The SCARLETEEL attack proves that a single point of vulnerability in an organization’s cloud environment could be enough for persistent and savvy malicious actors to exploit it for network infiltration and theft of sensitive data.
Sysdig suggests that organizations take the following security measures to protect their cloud infrastructure against similar attacks:
- Keep all your software up to date.
- Use IMDS v2 instead of v1, which prevents unauthorized access to metadata.
- Adopt the principles of least privilege on all user accounts.
- Restrict read-only access to resources that may contain sensitive data such as Lambda.
- Delete old and unused permissions.
- Use key management services like AWS KMS, GCP KMS, and Azure Key Vault.
Sysdig also recommends having a comprehensive detection and alerting system in place to ensure that malicious attacker activity is quickly flagged, even when it evades protective measures.
[ad_2]
Source link
