[ad_1]

The RIG exploit kit is enjoying its most successful period, attempting around 2,000 intrusions per day and succeeding around 30% of the time, the highest rate in the service’s long operational history.
By exploiting relatively old vulnerabilities in Internet Explorer, RIG EK has been seen distributing various malware families, including Dridex, SmokeLoader, and RaccoonStealer.
According to a detailed report by Prodaft, whose researchers had access to the service’s main web panel, the exploit kit remains a significant large-scale threat to individuals and organizations.
The sordid history of RIG EK
RIG EK was first released eight years ago, in 2014, and presented as an “exploit as a service” hired out to other malware operators to deliver their malware to vulnerable devices.
The RIG exploit kit is a collection of malicious JavaScript scripts embedded in compromised or malicious websites by threat actors, which are then promoted through malicious advertisements.
When a user visits these sites, malicious scripts are executed that attempt to exploit various browser vulnerabilities to automatically install malware on the device.
In 2015, the kit’s authors released the second major version of the kit, laying the groundwork for more extensive and successful operations.
In 2017 however, RIG suffered a major blow following a coordinated withdrawal action which wiped out much of its infrastructure, severely disrupting its operations.
In 2019, RIG returned, this time focusing on ransomware distribution, helping Sodinokibi (REvil), NemtyAnd ERIS ransomwarecompromise organizations with data-encrypting payloads.
In 2021, the owner of RIG announced that the service would shut down; however, RIG 2.0 returned in 2022 with two new exploits (CVE-2020-0674 and CVE-2021-26411 in Internet Explorer), achieving an unprecedented hit rate.
In April 2022, Bitdefender reported that RIG was used to drop the Redline information-stealing malware on victims.
While many of the exploits targeted by RIG EK relate to Internet Explorer, which Microsoft Edge has long since replaced, the browser is still used by millions of enterprise devices, which is a primary target.
Current attack volumes
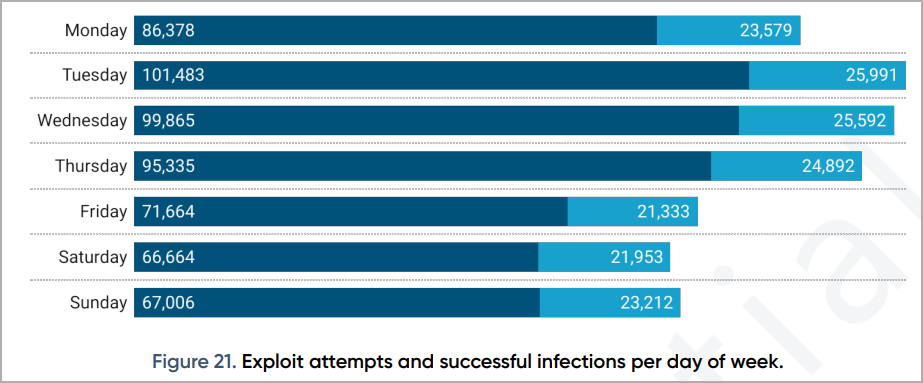
Prodaft says RIG EK currently targets 207 countries, launching an average of 2,000 attacks per day and having a current success rate of 30%. This rate was 22% before the exploit kit resurfaced with two new exploits, Prodaft said.
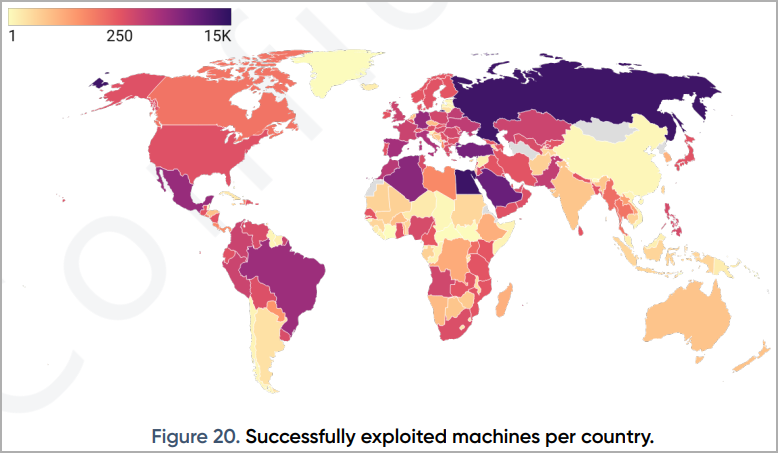
As the heat map published in the report shows, the most affected countries are Germany, Italy, France, Russia, Turkey, Saudi Arabia, Egypt, Algeria, Mexico and Brasil. However, there are victims all over the world.
The highest success rate is brought by CVE-2021-26411, reaching a successful exploit rate of 45%, followed by CVE-2016-0189 with 29% and CVE-2019-0752 with 10%.
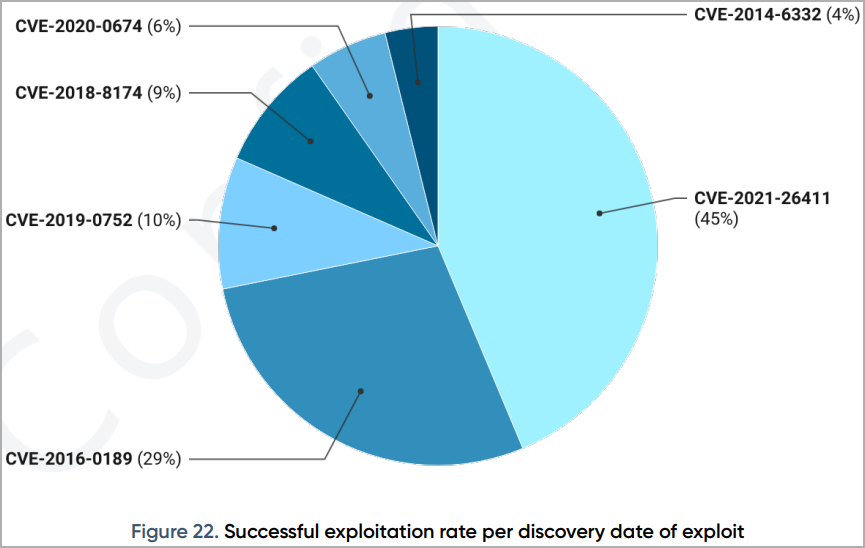
CVE-2021-26411 is a very serious memory corruption flaw in Internet Explorer that Microsoft patched in March 2021, triggered by visiting a maliciously crafted website.
Vulnerabilities CVE-2016-0189 and CVE-2019-0752 are also found in Internet Explorer, allowing remote code execution in the browser.
CISA published a active exploitation alert for CVE-2019-0752 in February 2022, notifying system administrators that the vulnerability is still being exploited and to apply available security updates.
A variety of malicious payloads
Currently, RIG EK primarily pushes information-stealing and initial access malware, with Dridex being the most common (34%), followed by SmokeLoader (26%), RaccoonStealer (20%), Zloader (2.5% ), Truebot (1.8%), and IcedID (1.4%).
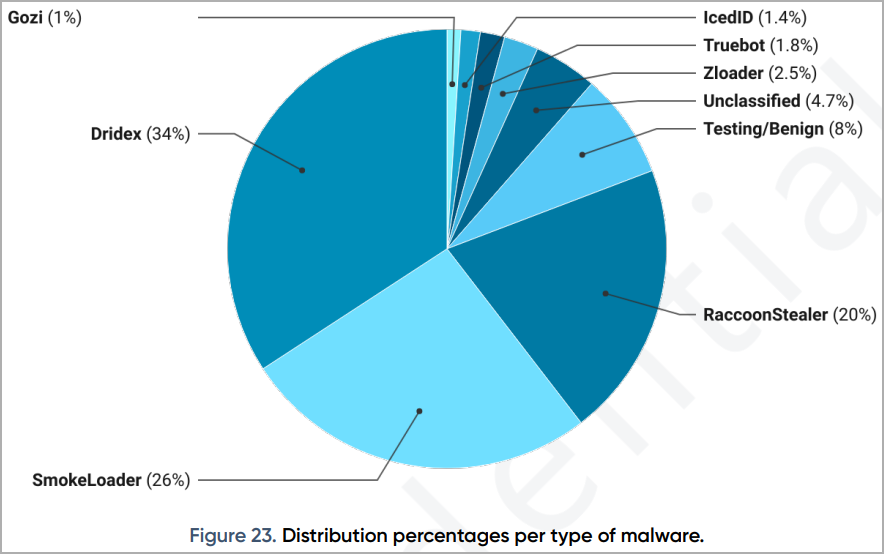
Of course, the types of malware distributed by RIG EK constantly change depending on which cybercriminals choose to use the service.
Prodaft has also previously observed the distribution of Redline, RecordBreaker, PureCrypter, Gozi, Royal Ransomware and UrSnif.
The distribution of the Dridex banking Trojan is particularly interesting because there are signs that the operators of the RIG have taken steps to ensure its distribution without problems.
“The RIG administrator had taken additional manual configuration steps to ensure that the malware was distributed smoothly”, explains Prodaft in the report.
“Given all these facts, we assess with great confidence that the malware developer Dridex has a close relationship with the administrators of the RIG.”
It should be noted that Dridex was related to Entropy ransomware a year ago, so RIG EK breaches could lead to data encryption incidents.
The RIG EK remains a significant threat to individuals and organizations using outdated software, threatening to infect their systems with stealth information thieves who can siphon highly sensitive data.
However, RIG EK’s focus on Internet Explorer may soon render the service obsolete, as Microsoft eventually Internet Explorer retired in February 2023redirecting users to Microsoft Edge.
[ad_2]
Source link
