[ad_1]

Proof-of-concept exploit code will be released later this week for a critical vulnerability that allows remote code execution (RCE) without authentication in several VMware products.
Tracked as CVE-2022-47966, this pre-authentication RCE security flaw is due to the use of an outdated and vulnerable third-party dependency, Apache Santuario.
Successful exploitation allows unauthenticated hackers to execute arbitrary code on Acronis servers if SAML-based single sign-on (SSO) is or has been enabled at least once prior to the attack.
The list of vulnerable software includes almost all ManageEngine products. However, fortunately, Zoho has already fixed them in waves from October 27, 2022, updating the third-party module to a newer version.
Incoming “spray and pray” attacks
On Friday, security researchers from the Horizon3 attack team warned administrators that they have created a proof-of-concept (PoC) exploit for CVE-2022-47966.
“The vulnerability is easy to exploit and is a good candidate for attackers to ‘spray and pray’ across the Internet. This vulnerability allows remote code execution as NT AUTHORITY\SYSTEM, essentially giving an attacker complete control on the system,” vulnerability researcher Horizon3 said. James Cavalier said.
“If a user determines that they have been compromised, further investigation is required to determine the damage caused by an attacker. Once an attacker has SYSTEM-level access to the endpoint, attackers are likely to begin to dump credentials via LSASS or leverage existing public tools to access stored application credentials to perform lateral movement.”
Although they have yet to release the technical details and only Shared Indicators of Compromise (IOC) that defenders can use to determine if their systems have been compromised, Horizon3 plans to go out their PoC feat later this week.
Horizon3 researchers also shared the following screenshot showing their exploit in action against a vulnerable instance of ManageEngine ServiceDesk Plus.
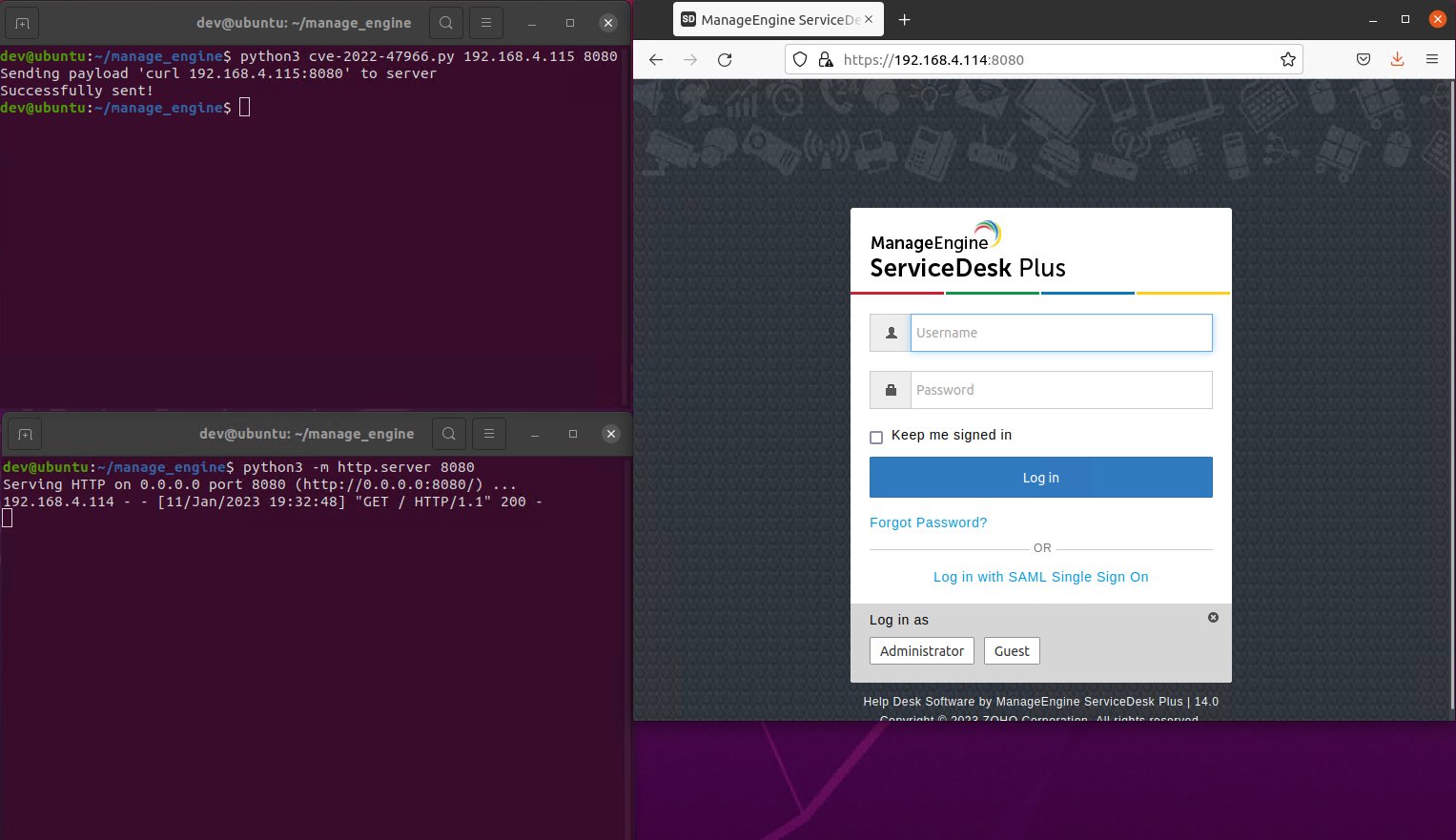
10% of all exposed instances are vulnerable to attack
By examining just two of the vulnerable ManageEngine products, ServiceDesk Plus and Endpoint Central, Horseman found thousands of unpatched servers exposed online through Shodan.
Among them, hundreds also had SAML enabled, with around 10% of all exposed ManageEngine products vulnerable to CVE-2022-47966 attacks.
Although there are no public reports of attacks exploiting this vulnerability and no attempt to exploit it in the wild According to cybersecurity firm GreyNoise, motivated attackers will likely move quickly to create their own RCE exploits once Horizon3 releases its PoC code, even if they release a minimal version.
Horizon3 previously released exploit code for:
- CVE-2022-28219a critical vulnerability in Zoho ManageEngine ADAudit Plus that may allow attackers to compromise Active Directory accounts,
- CVE-2022-1388a critical bug that allows remote code execution in F5 BIG-IP network devices,
- and CVE-2022-22972a critical authentication bypass vulnerability in several VMware products that allows attackers to gain administrator privileges.
Zoho ManageEngine servers have come under constant attack over the past few years, with nation-state hackers using similar tactics and tools as the China-linked APT27 hacking group targeting them between August and October 2021.
Instances of Desktop Central were also hacked in July 2020, with threat actors selling access to hacked organizations’ networks on hacking forums.
After this and other large attack campaigns, the FBI and CISA issued joint notices [1, 2] warning of state-sponsored attackers exploiting ManageEngine bugs to hijack critical infrastructure organizations.
[ad_2]
Source link
